Network Exploitation, Reconnaissance & Vulnerability Engine
Network Exploitation, Reconnaissance & Vulnerability Engine (N.E.R.V.E)
We believe security scanning should be done continuously. Not daily, weekly, monthly, or quarterly.
The benefit of running security scanning continuously can be any of the following:
- You have a dynamic environment where infrastructure gets created every minute/hour / etc.
- You want to be the first to catch issues before anyone else
- You want the ability to respond quickly.
NERVE was created to address this problem. Commercial tools are great, but they are also heavy, not easily extensible, and cost money.
About NERVE
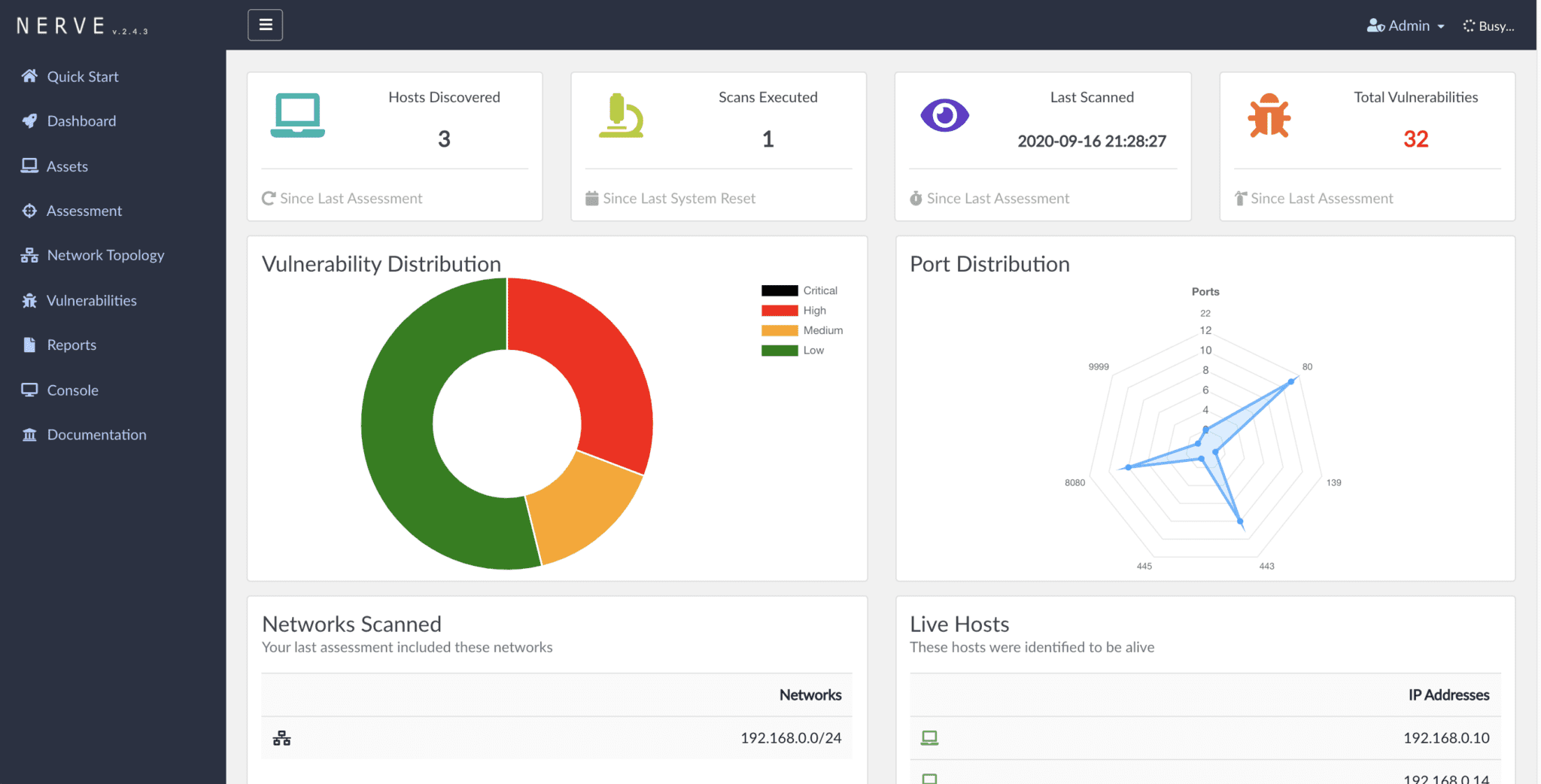
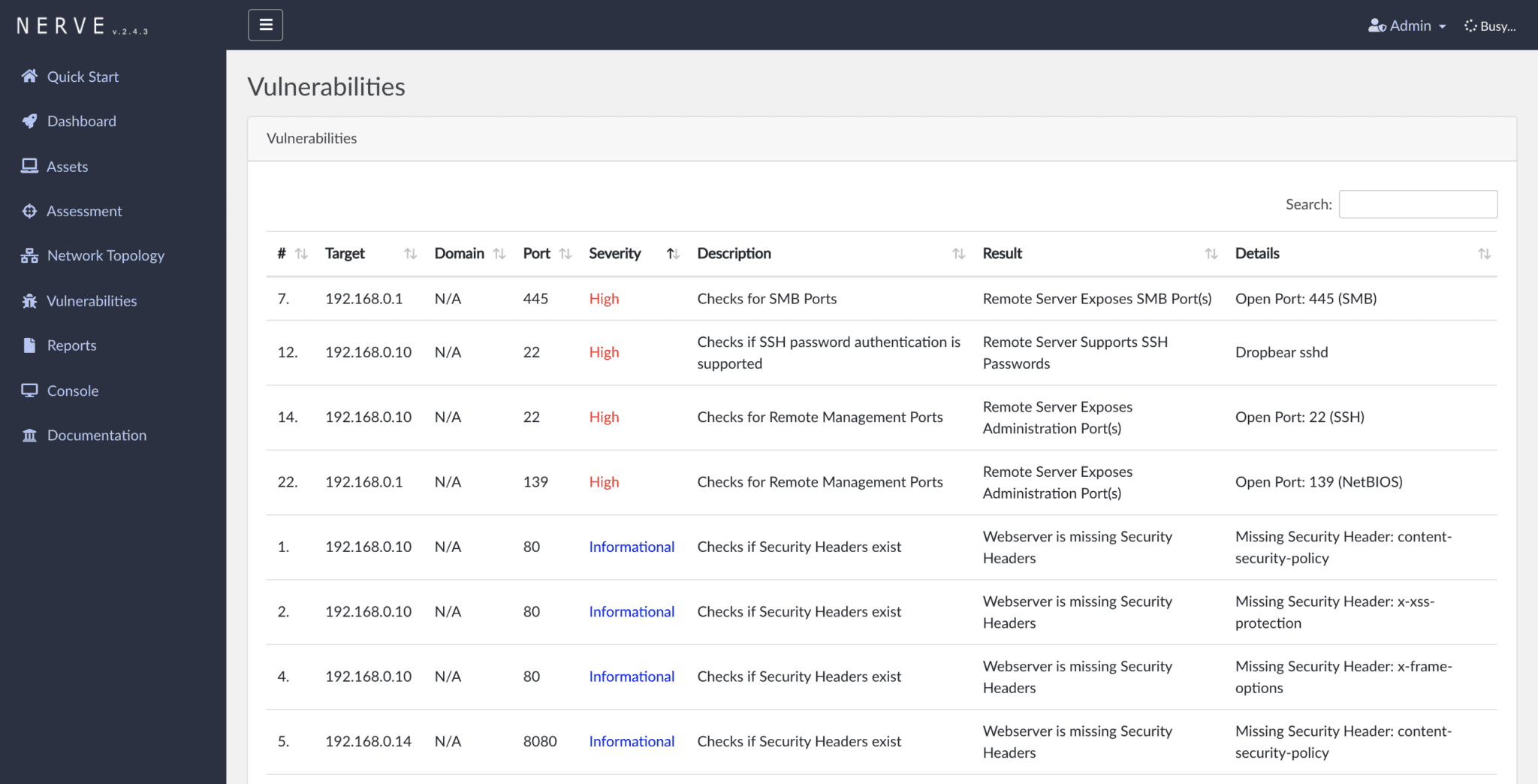
NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations, network services, and unpatched services.
Example of some of the NERVE’s detection capabilities:
- Interesting Panels (Solr, Django, PHPMyAdmin, etc.)
- Subdomain takeovers
- Open Repositories
- Information Disclosures
- Abandoned / Default Web Pages
- Misconfigurations in services (Nginx, Apache, IIS, etc.)
- SSH Servers
- Open Databases
- Open Caches
- Directory Indexing
- Best Practices
It is not a replacement for Qualys, Nessus, or OpenVAS. It does not do authenticated scans and operates in black-box mode only.
Features
NERVE offers the following features:
- Dashboard (With a Login interface)
- REST API (Scheduling assessments, Obtaining results, etc)
- Notifications
- Slack
- Webhook
- Reports
- TXT
- CSV
- HTML
- XML
- Customizable scans
- Configurable intrusiveness levels
- Scan depth
- Exclusions
- DNS / IP Based
- Thread Control
- Custom Ports
- Network Topology Graphs
We put together the Graphical User Interface primarily for ease of use, but we will be putting more emphasis on detections and new signatures than creating a full-blown user interface.
Install & Use
Copyright (c) 2020 Exposed Atoms






