AutoRecon: multi-threaded network reconnaissance tool
AutoRecon
AutoRecon is a multi-threaded network reconnaissance tool which performs automated enumeration of services. It is intended as a time-saving tool for use in CTFs and other penetration testing environments (e.g. OSCP). It may also be useful in real-world engagements.
The tool works by firstly performing port scans/service detection scans. From those initial results, the tool will launch further enumeration scans of those services using a number of different tools. For example, if HTTP is found, nikto will be launched (as well as many others).
Everything in the tool is highly configurable. The default configuration performs no automated exploitation to keep the tool in line with OSCP exam rules. If you wish to add automatic exploit tools to the configuration, you do so at your own risk. The author will not be held responsible for negative actions that result from the mis-use of this tool.
AutoRecon was inspired by three tools which the author used during the OSCP labs: Reconnoitre, ReconScan, and bscan. While all three tools were useful, none of the three alone had the functionality desired. AutoRecon combines the best features of the aforementioned tools while also implementing many new features to help testers with the enumeration of multiple targets.
Features
- Supports multiple targets in the form of IP addresses, IP ranges (CIDR notation), and resolvable hostnames.
- Can scan targets concurrently, utilizing multiple processors if they are available.
- Customizable port scanning profiles for flexibility in your initial scans.
- Customizable service enumeration commands and suggested manual follow-up commands.
- An intuitive directory structure for results gathering.
- Full logging of commands that were run, along with errors if they fail.
- Global and per-scan pattern matching so you can highlight/extract important information from the noise.
Install
git clone https://github.com/Tib3rius/AutoRecon.git
cd AutoRecon
pip install -r requirements.txt
apt install seclists
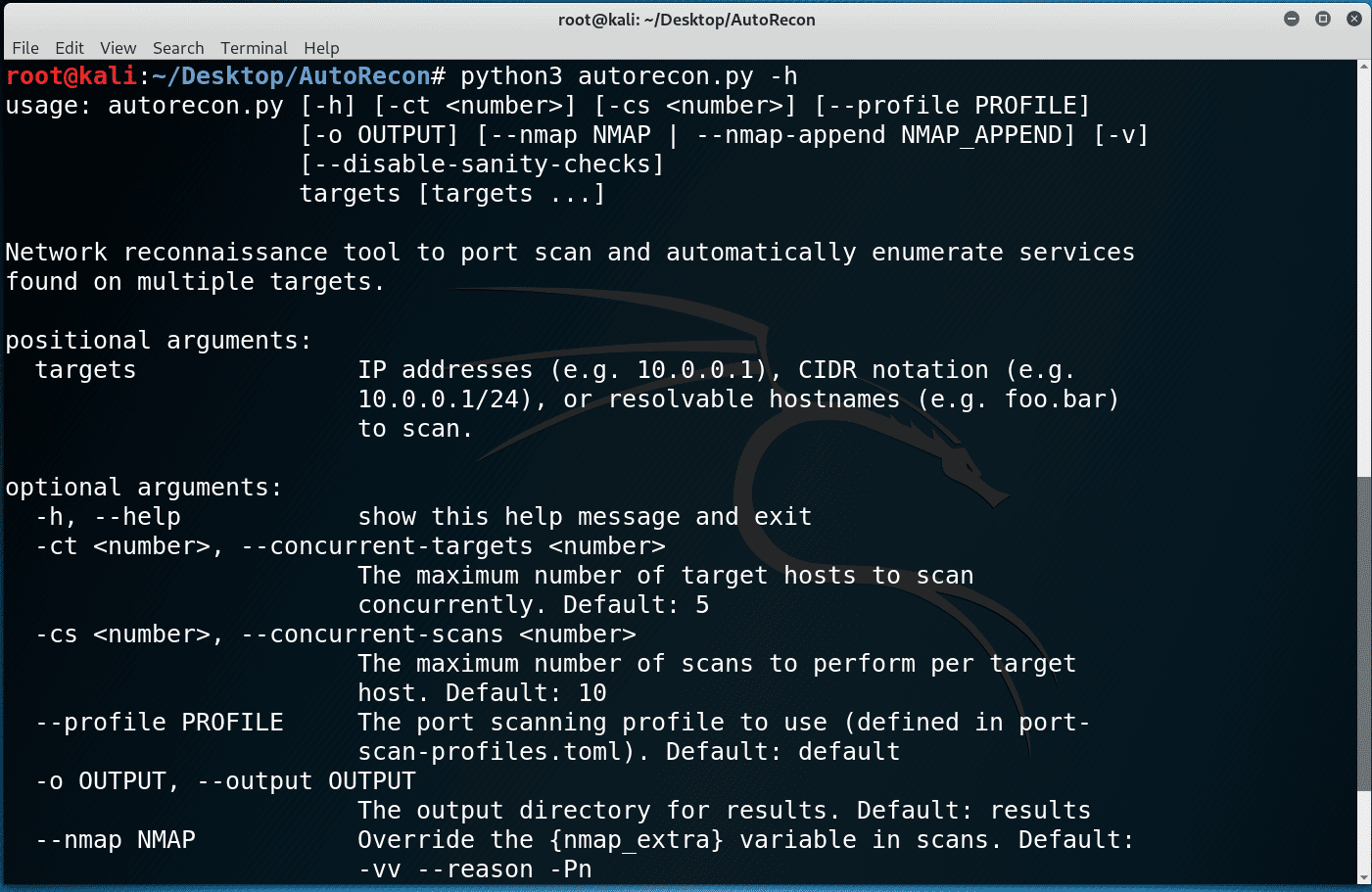
Usage
Copyright (C) 2019 Tib3rius
Source: https://github.com/Tib3rius/





