Cybersecurity company Lastline discovered a new attack technology that leverages Office Excel spreadsheets in early December 2017 and has just recently expanded to include other Office applications. The researchers discovered a new type of malicious Office Excel file that downloads and executes malware without any clues to macros, shellcode or DDE code. And when the researchers scanned the files submitted to Virustotal, a website that offers free suspicious file analysis services, only three anti-virus software defined it as malicious, so this is a new attack technique for Excel spreadsheets.
Attack and Payload
When the user opens the Excel file, a dialog box will pop up saying:
External links
Is a feature of Microsoft Office that allows authors to share Office documents through external resource links without having to embed those resources directly into the document, making the entire document smaller, newer and more flexible.
From this perspective, this attack appears to be very similar to the DDE attack, which is the more popular Office File Utilization technology used to execute external code through Microsoft’s Dynamic Data Exchange facility.
Once the user agrees to update the link, the document immediately creates a cmd / PowerShell process that downloads and executes the next phase payload (exe file): Execute malware.
Since only three software detected such attacks, even scanning for an Excel infection was considered a false positive and may not be further investigated or remedied. The researchers confirmed that the payload sent by the Excel script was Loki, a notorious “document stealing” malware.
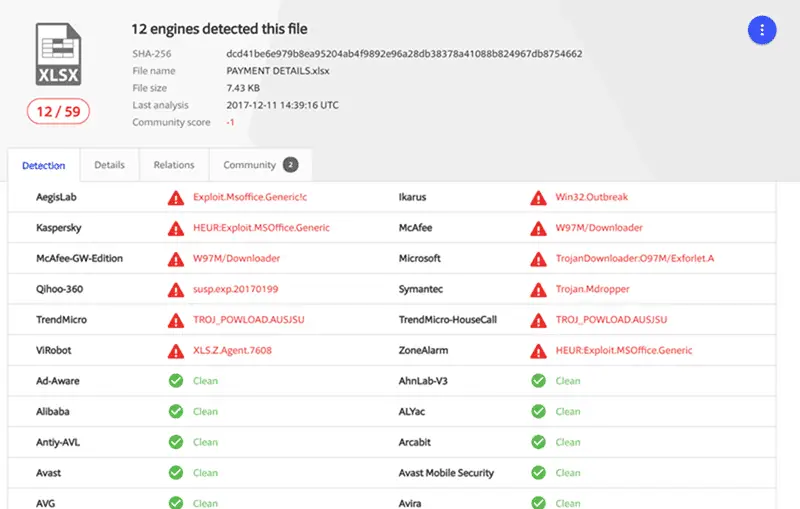
Figure B: Twelve days after initial detection, 12 AV tools detected this threat
For most security response teams, this is a double blow. First, the low detection rate makes the security team think it is false positives. Second, even if they discovered Loki, the mitigation was often mistakenly implemented. When subsequent threat attackers use the leaked credentials to gain unauthorized access and attempt to move laterally, the victim is vulnerable to a second “no malware” attack.
The researchers submitted the malicious Excel script to Virustotal on December 10 and 12 of 60 anti-virus tools detected it as a threat. After the log tracing found a file named “_output23476823784.exe”, about 50% of the detection engines identified the file as a malicious file.
Most anti-virus programs mark _output23476823784.exe Payload as a Trojan, which indicates that it is a Trojan.Generic Payload.
The real body of this Payload: Malware Loki Bot
Behavioral Intelligence further identifies the dubious Payload as a Loki bot.
Figure G: Dark Market Ad
Loki’s promotional videos show that it can capture vouchers for a variety of applications, especially FireFox (47% stolen documents) and Chrome (41%), while Windows and email vouchers account for just 1% -3%.
Figure I: Vulnerable websites as per Loki
Once the victim’s voucher has been stolen, Loki shows vulnerable sites for identity theft, including social media sites, payment portals, bitcoin wallets, and even a Moroccan government login page.
Malware LokiBot
In November 2017, “LokiBot”, a malicious software evolved from “BankBot,” is known as the first “Transformers” Android malware because “LokiBot” has its own unique features compared to other bank hijackings, Which can initiate attacks according to different target environments, such as initiating interface hijacking to user equipment, encrypting user equipment data, extorting money from users, establishing socks5 proxy and SSH tunnel, and infiltrating intranet data.
“LokiBot” Spreads The user’s installation was induced through malicious updates such as “Adobe Flash Playe”, “APK Installer”, “System Update”, “Adblock”, “Security Certificate” and other application updates.
Reference: lastline