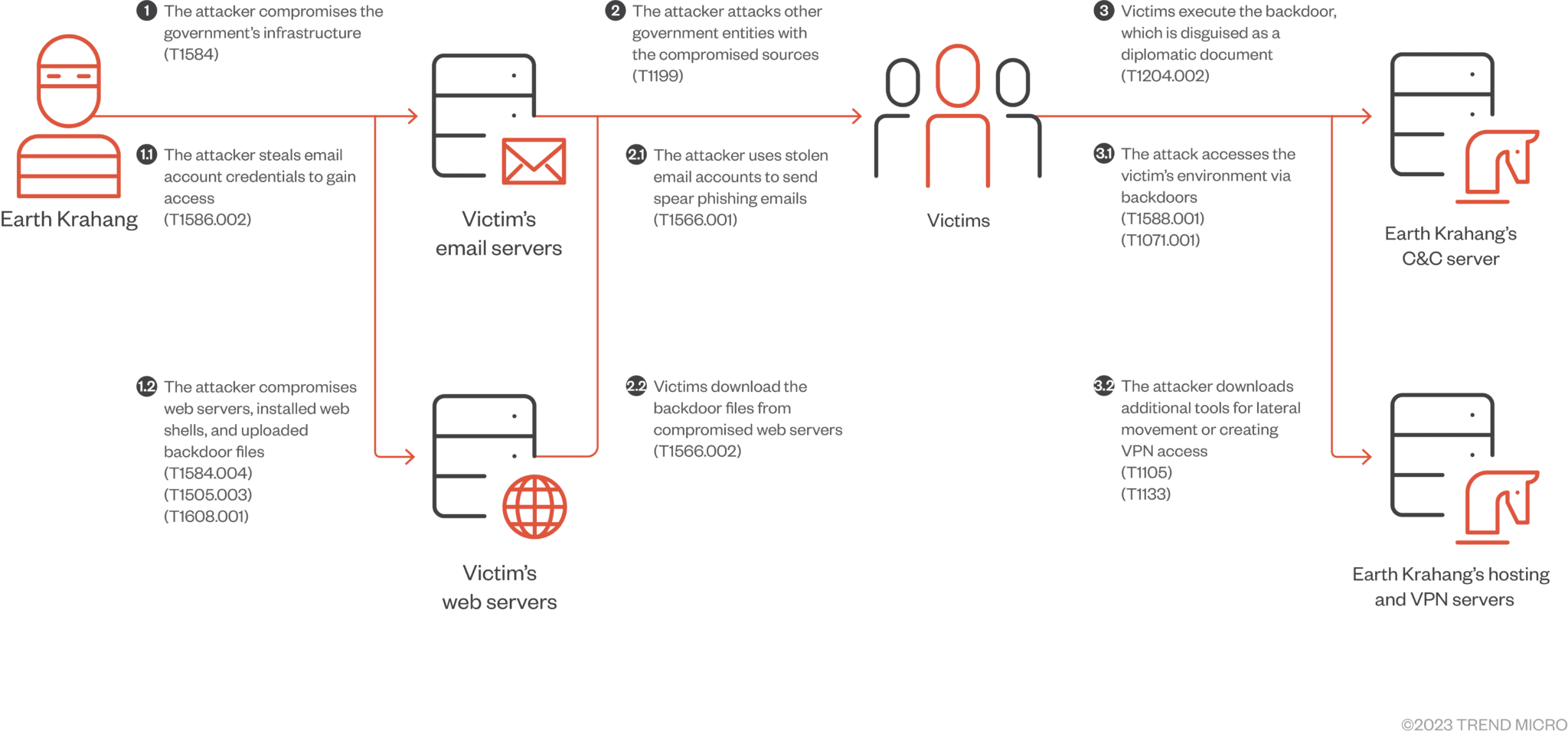
Infection chain of an Earth Krahang’s spear-phishing attack
In a recently released report, Trend Micro reveals details of a new advanced persistent threat (APT) campaign they’ve named Earth Krahang. This China-nexus threat actor demonstrates alarming sophistication, with an unwavering focus on compromising government entities worldwide. Earth Krahang’s primary target areas are in Southeast Asia, but their reach extends far beyond, impacting organizations in Europe, America, and Africa.
A Calculated and Multi-Pronged Attack Strategy

The Earth Krahang campaign stands out due to its cunning blend of technical exploitation and social engineering. They tirelessly scan public-facing servers, searching for exploitable vulnerabilities such as CVE-2023-32315 and CVE-2022-21587. Once found, these weaknesses become entry points for brute-force attacks, allowing them to crack passwords and gain access. Spear-phishing campaigns play a critical role, with attackers crafting emails using geopolitical themes to entice government officials into opening malicious attachments or clicking on poisoned links.
In a particularly insidious tactic, Earth Krahang compromises government infrastructure, weaponizing it against other government entities. This includes hosting malicious payloads on compromised web servers, proxying attack traffic to disguise their origin, and even sending spear-phishing emails from compromised government email accounts – a strategy designed to exploit existing trust relationships.
Custom Tools and Evolving Techniques
Trend Micro has observed Earth Krahang’s toolset undergoing active development. Initially using a custom backdoor called RESHELL, they have since shifted to XDealer, a more feature-rich backdoor. This evolution signals a determination to maintain a technological edge. Other observed tools include the popular Cobalt Strike framework, along with utilities used for privilege escalation and network reconnaissance.
Wide-Ranging Government Espionage
The primary goal of the Earth Krahang campaign appears to be cyber espionage. The group targets government organizations across numerous sectors. Ministries of Foreign Affairs are under particularly heavy attack, but they also infiltrate education departments, telecommunications providers, and a range of other critical government functions. The Earth Krahang threat actor uses a combination of brute-force attacks and custom scripts to breach email servers and steal sensitive data.
Links to Earth Lusca and Implications for Attribution
Trend Micro’s analysis paints a complex picture. While Earth Krahang initially operated with unique infrastructure and tools, strong connections have emerged to Earth Lusca, a previously identified China-linked threat actor. This suggests that Earth Krahang is a separate intrusion set, possibly operating as a specialized unit under the umbrella of a larger, well-resourced threat group.
Security Measures are Essential
The Earth Krahang campaign poses a significant threat to governments and their affiliated organizations globally. Here are crucial steps to mitigate risks:
- Patching is Paramount: Apply security patches to software and systems with the utmost urgency.
- Employee Awareness: Train staff extensively on recognizing and resisting social engineering attempts, especially targeted phishing emails.
- Zero-Trust Architecture: Implement least privilege access and assume breaches are a possibility.
- Threat Intelligence: Maintain up-to-date knowledge of the latest threats and tactics employed by advanced groups.
- Multi-layered Defense Utilize endpoint protection, network monitoring, and advanced threat detection solutions to create a robust defensive posture.