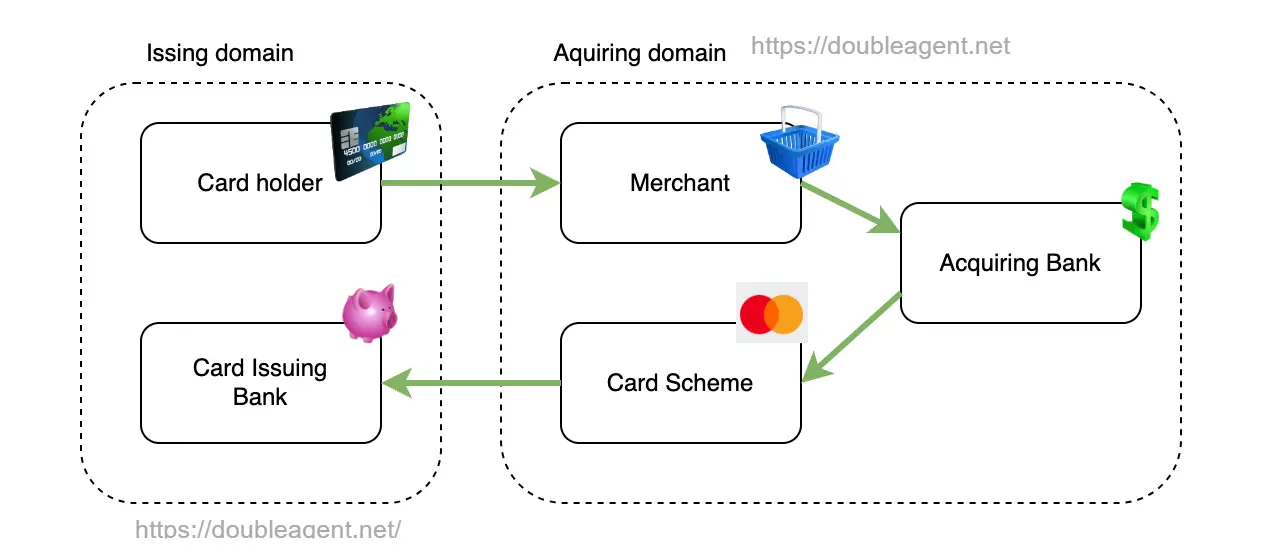
Example flow of an authorization request for a purchase with a credit card | Image: HaxRob
Security researcher HaxRob has uncovered a new Linux variant of the notorious FASTCash malware, attributed to North Korean state-sponsored hacking groups. This malware targets financial institutions by manipulating payment systems to facilitate unauthorized ATM withdrawals. The Linux variant adds another operating system to the growing list of FASTCash targets, which already include IBM AIX and Windows. HaxRob’s analysis reveals that the malware has been designed to exploit payment switches in banking networks.
FASTCash is a sophisticated malware used by North Korean hacking groups, primarily attributed to the Lazarus group and its subgroups such as APT38 and BeagleBoyz. The malware enables threat actors to issue fraudulent withdrawal approvals by compromising the internal payment switches used by banks. These switches are responsible for processing transactions between ATMs and the bank’s core financial systems.
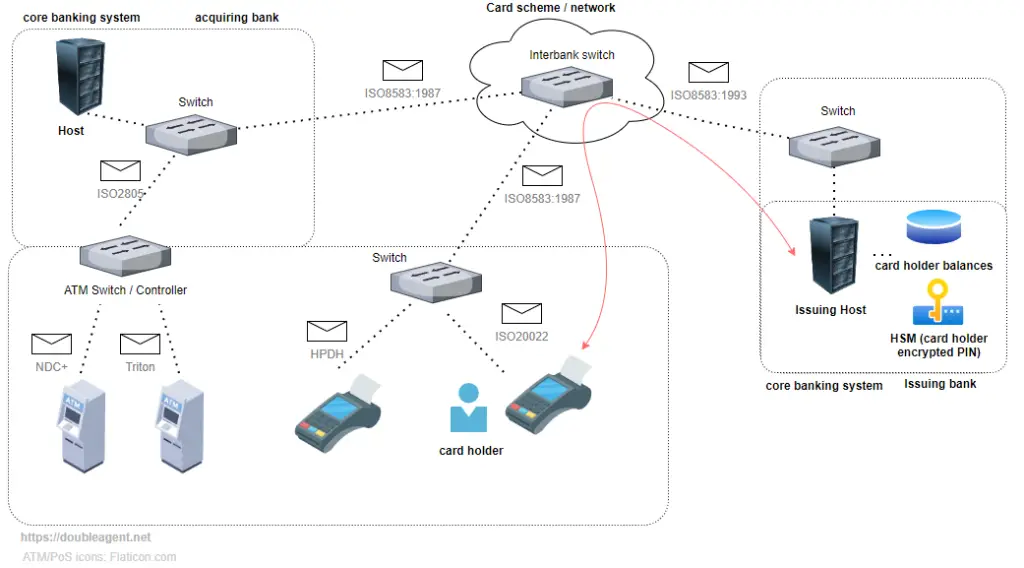
According to HaxRob, the malware targets a key vulnerability in the payment processing system: “FASTCash malware modifies transaction messages in a point in the network where tampering will not cause upstream or downstream systems to reject the message.” This tampering allows the malware to approve fraudulent ATM transactions without raising alarms.
While previous versions of FASTCash targeted IBM AIX and Windows systems, the discovery of a Linux variant marks an expansion in the malware’s versatility. HaxRob notes, “The newly identified Linux variant retains key functionality, such as intercepting declined transactions and authorizing them with a random amount of funds in Turkish Lira”. This shows how the threat actors behind FASTCash are continually adapting their tactics to infiltrate a broader range of systems.
The Linux version, compiled for Ubuntu 20.04, was likely developed in a virtual machine environment. Interestingly, both the Linux and Windows variants target similar payment infrastructures, hinting at a coordinated effort by the attackers to compromise multiple platforms within the same financial networks.
HaxRob highlights that “the Linux variant has slightly reduced functionality compared to its Windows predecessor, although it still retains key functionality: intercepting declined (magnetic swipe) transactions messages for a predefined list of card holder account numbers and then authorizing the transaction with a random amount of funds in the currency of Turkish Lira”. This interception allows the malware to authorize fraudulent transactions despite insufficient funds in the victim’s accounts.
FASTCash malware works by intercepting ISO8583 messages—standard messages used in credit and debit card transactions—between the ATM or point-of-sale terminal and the bank’s payment processing system. Once the malware is in place, it modifies messages to authorize transactions even when they should be declined. HaxRob explains that the malware “a random amount of Turkish Lira to be fraudulently added to the authorization response messages”, bypassing normal transaction validation processes.
In the Linux variant, the malware hooks into the recv() function of a compromised process, monitoring for transaction requests. If a declined transaction is detected, the malware injects a fraudulent approval message back into the system, allowing ATM withdrawals despite the account’s lack of funds.
FASTCash’s attacks have primarily focused on payment switches operating in Turkish Lira, though older versions of the malware targeted other currencies like the Indian Rupee. By manipulating the ISO8583 messages, the malware avoids detection by standard transaction validation systems. This makes it incredibly dangerous, as it can be used to drain ATMs across various regions without triggering immediate red flags in banking systems.
The discovery of this Linux variant underscores the need for improved detection and response mechanisms, especially for Linux-based systems that are increasingly becoming targets for sophisticated malware campaigns. HaxRob recommends that financial institutions implement chip and PIN verification for debit cards, along with message authentication codes to validate transaction responses. He emphasizes that “The process injection technique employed to intercept the transaction messages should be flagged by any commercial EDR or opensource Linux agent with the appropriate configuration to detect usage of the ptrace system call”.
To combat the threat posed by FASTCash and similar malware strains, HaxRob and other security experts recommend that financial institutions implement strict security controls, including:
- Implement chip and PIN requirements for debit cards.
- Require and verify message authentication codes on issuer financial request response messages.
- Perform authorization response cryptogram validation for chip and PIN transactions.