Simplified overview of the attack flow | Image: Rapid7
Cybersecurity firm Rapid7 has uncovered a widespread malvertising campaign that is actively targeting individuals searching for popular utilities like WinSCP and PuTTY. This sophisticated attack uses malicious ads on common search engines like Bing, luring unsuspecting users to download trojanized installers.

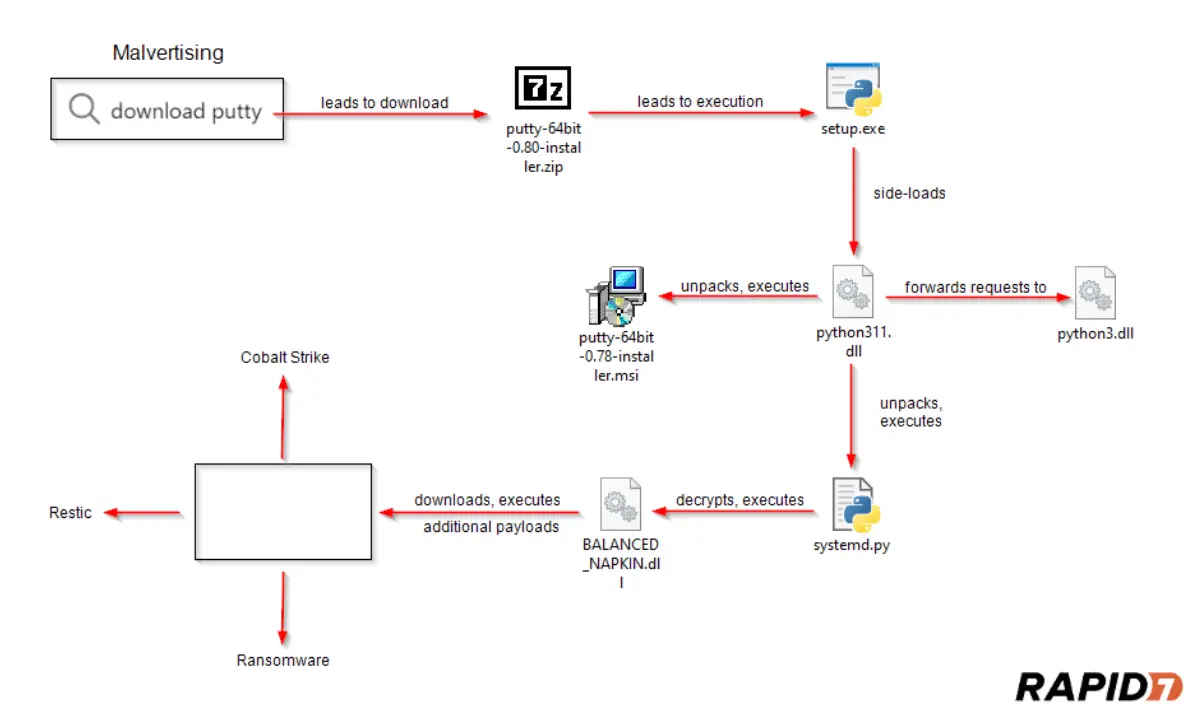
Since early March 2024, Rapid7 has been tracking an increase in compromised installers for WinSCP, a file transfer client, and PuTTY, a secure shell (SSH) client. The attackers exploit search engine advertising to lure victims to download from clone sites that mimic legitimate software distribution pages. This infection process begins when an unsuspecting user clicks on an ad, which redirects them to a deceptive download page.
The infection is initiated through a seemingly benign setup process. Victims download a ZIP archive containing a trojanized version of the software, which includes a renamed version of pythonw.exe, disguised as setup.exe. Upon launching, this executable side-loads a malicious DLL, python311.dll, effectively bypassing typical security checks by replacing the legitimate python311 DLL, which is renamed to python311x.dll in the same directory.
This technique, known as DLL side-loading, is facilitated by hijacking the DLL search order—a method where the system looks for required DLLs in the same directory as the executable before searching system-wide directories.
The primary payload within the malicious DLL is an encrypted archive that, once unpacked during execution, performs multiple operations:
- Legitimate Software Installation: The malware first executes a legitimate installer for WinSCP to reduce suspicion.
- Malicious Script Execution: It then runs a Python script, systemd.py, which decrypts and performs reflective DLL injection to introduce a Sliver beacon into the system.
Upon establishing a connection via the Sliver beacon, the malware can receive additional payloads, including Cobalt Strike beacons, facilitating further malicious activities like data exfiltration and ransomware deployment.
The techniques, tactics, and procedures (TTPs) observed in this campaign bear resemblances to previous campaigns conducted by BlackCat/ALPHV, as noted by Trend Micro and other security entities. This includes the use of the Sliver toolset for establishing a robust foothold within compromised networks.
Rapid7 recommends several mitigation strategies to combat this threat:
- Verify Software Sources: Always ensure that the source of any downloaded software is legitimate. Check the digital signatures and hash values of downloaded files.
- DNS Monitoring: Use tools like DNSTwist to identify and block DNS requests to potentially malicious permutations of known domains.
- Educate IT Teams: As IT professionals are the primary targets, it is crucial to train these teams to recognize the signs of these attacks and verify the authenticity of the tools they download.