Kaspersky Security Labs has discovered a very interesting malware that detects system configuration to determine which threat scheme to use.
Ransomware and mining malware is currently at the top of the list of malicious threats, and this malware maximises the benefits of both integrations.
After the initial infection, the malware also performs complex tests to avoid the security personnel’s virtual machine debugging, but Kaspersky eventually monitored it.
Determine the system configuration to decide which solution to use:
The malware detects which setting to use when configuring the system. If the user’s computer configuration is high, download the mining software to use the computer for mining.
The full mining software will use the graphics card and processor resources to mine Monroe, the original chain of Monroe, and the less common Dash.
If it detects that the user’s computer configuration is relatively low, then download the ransomware, and then you can encrypt all the user’s files for ransom and so on.
To maximise the benefits, the hacker also loads the backdoor to monitor the user, including checking the list of currently running processes and automatically intercepting the screen.

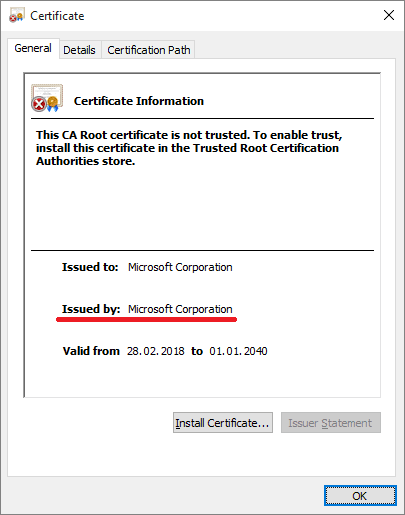
Fake Microsoft Corporation certificate
Forged documents are spread by email:
The main transmission route of this malware is mass spam, which indicates that the contract or contact information induces users to download and open.
However, it contains malicious code to perform malicious operations through the macro function of Microsoft Office, but in the end, it needs the user to confirm before executing.
To trick the user into clicking on the confirmation to open the document, a prompt will appear that the system file is missing, and then the Microsoft digital signature impersonation system file is forged.
What’s interesting is that the hacker tried to insert the fake digital certificate into the system root directory through the above steps, which can facilitate the subsequent stable operation of the mining process.