
A new malware campaign, identified as I2PRAT (I2P Remote Access Trojan), is raising the bar for cybercriminals’ ability to evade detection. Detailed in a report by Banu Ramakrishnan, a Malware Analyst at G DATA, this sophisticated malware leverages the Invisible Internet Project (I2P), an encrypted peer-to-peer overlay network, to anonymize its Command and Control (C2) communications.
Unlike traditional malware, which often relies on more traceable C2 communication methods, I2PRAT employs I2PD, an open-source C++ implementation of the I2P client, to anonymize its activities. Using I2P enables encrypted peer-to-peer communication, making it impossible for an observer to access the content of messages or identify their source and destination. This ensures that both the attackers and the victim machines remain hidden.
I2PRAT’s infection strategy is as cunning as it is dangerous:
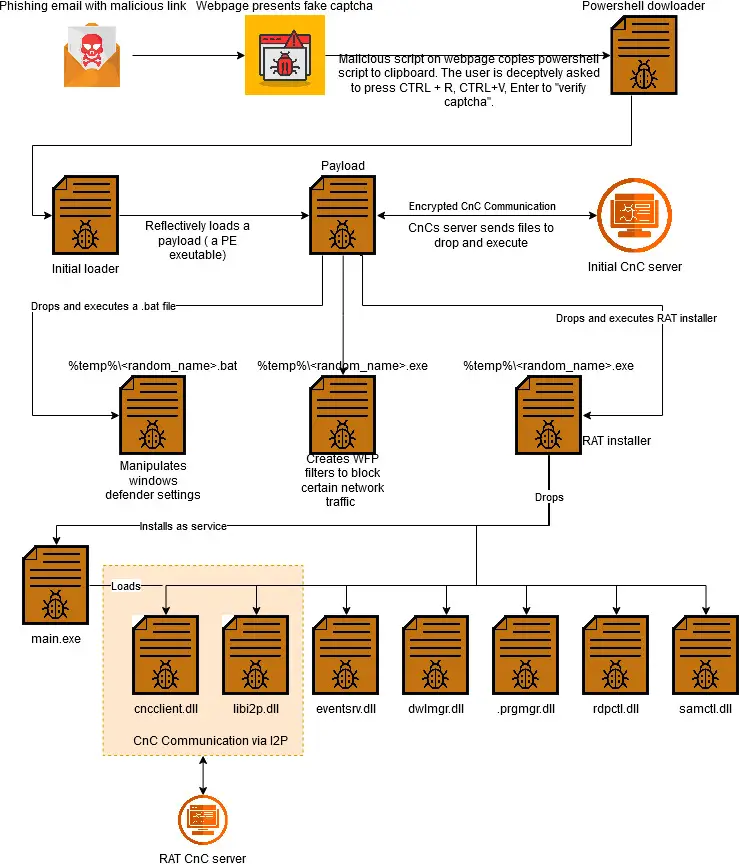
- Phishing Emails: Victims are lured into clicking a malicious link through carefully crafted phishing emails.
- Fake CAPTCHA Pages: These links direct users to fake CAPTCHA pages embedded with malicious JavaScript. The script copies a PowerShell command to the clipboard and tricks users into executing it by simulating human verification steps.
- Payload Deployment: The PowerShell script downloads and executes the first-stage malware loader, which then escalates privileges using an AppInfo RPC server bypass to achieve administrative access.
- RAT Installation: The loader installs the modular Remote Access Trojan (RAT), creating a hidden directory to store its components.
I2PRAT includes advanced mechanisms to neutralize system defenses:
- Microsoft Defender Manipulation: The malware disables key features of Microsoft Defender, blocks cloud-based telemetry, and prevents updates to security intelligence.
- Windows Filtering Platform (WFP) Filters: By modifying WFP rules, the malware ensures Microsoft Defender remains blind to its actions while simultaneously blocking Windows Update services.
I2PRAT’s modular structure makes it an extremely versatile tool for attackers. Plugins such as cnccli.dll, dwlmgr.dll, and rdpctl.dll enable capabilities like:
- Encrypted C2 Communication: The malware establishes secure channels with its operators through I2P, ensuring anonymity.
- File Downloading and Uploading: Attackers can remotely transfer files to and from victim systems.
- RDP Hijacking: The RAT enables remote desktop connections, even on systems with limited functionality, such as Windows Home editions.
Analysis of the malware’s activity reveals that it has been active since at least March 2024 and is potentially older. There is evidence suggesting that I2PRAT might be distributed through PrivateLoader.
Related Posts:
- New malware uses specially crafted UDP protocol for C&C Communications
- Hackers make poisoned Final Cut Pro specifically to target Mac users
- Leak: NSA and US Army can capture Tor, I2P, VPNs to monitor Monero users
