Image: Fortinet
Since the source code for the Mirai botnet was released in 2016, FortiGuard Labs has discovered a number of Mirai-based variants. In addition to Mirai’s original Telnet brute-force login functionality, they have been added with many new features such as exploits to target more system architectures.
In its long-term observation, FortiGuard Labs also noticed that hackers based on the Mirai source code are mainly motivated by money. Mirai was originally involved in launching a Distributed Denial of Service (DDoS) attack, but some of the variants that followed showed a gradual shift towards tapping cryptocurrencies with infected devices.

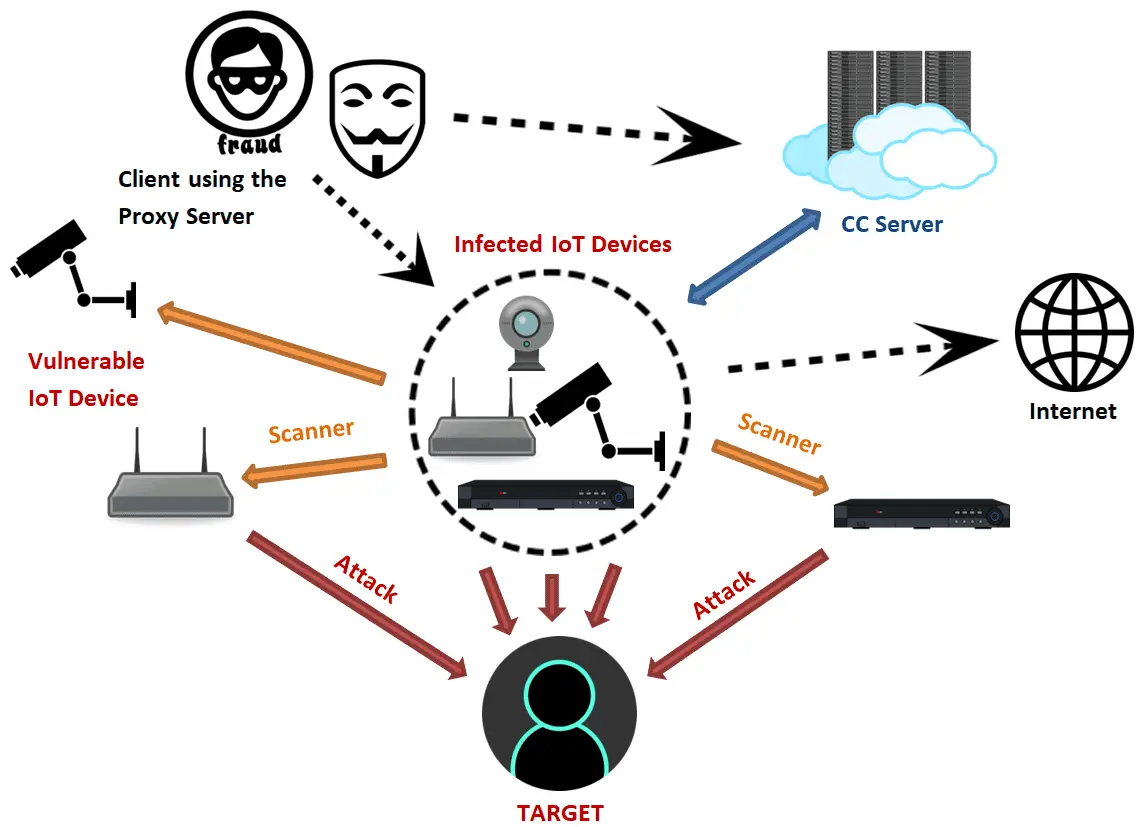
Last week, FortiGuard Labs once again found a new Mirai variant, which they named “OMG.” The OMG’s goal is to convert IoT devices to proxy servers for money, regardless of the original Mirai program or later variations.
Security expert Brian Krebs published an article in 2016 on how to get money by converting IoT devices to proxy servers. The article pointed out that hackers can use the proxy server to achieve anonymity, in order to carry out other malicious activities to get money. In addition, hackers can also profit from the sale of proxy servers to other cybercriminals.
Like the original Mirai program, OMG’s configuration tables are also encrypted from the beginning, requiring the use of a key to unlock them. In addition, OMG retains multiple modules of the original program to preserve Mirai’s original features (such as killing processes, Telnet brute-force logins, and launching DDoS attacks).
The difference is that OMG adds a firewall rule based on the original program, as OMG will use 3proxy, an open source software, to implement proxy functionality. In order for the proxy server to work properly, the OMG must set up a firewall to allow traffic to penetrate two random ports.
After initializing the module, OMG tries to connect to the command and control (C & C) server. However, during the analysis of the FortiGuard lab, the C & C server did not respond. Therefore, the researchers have reason to believe that OMG developers are only interested in selling proxy server access, and as a direct profit
FortiGuard Labs emphasizes that this is the first time they’ve observed the Mirai variant’s ability to simultaneously launch DDOS attacks and turn IoT devices into proxy servers. It may be a trend that more and more Mirai variants may come with more features at the same time, and their natural purpose is to seize money from us.
Source: Fortinet