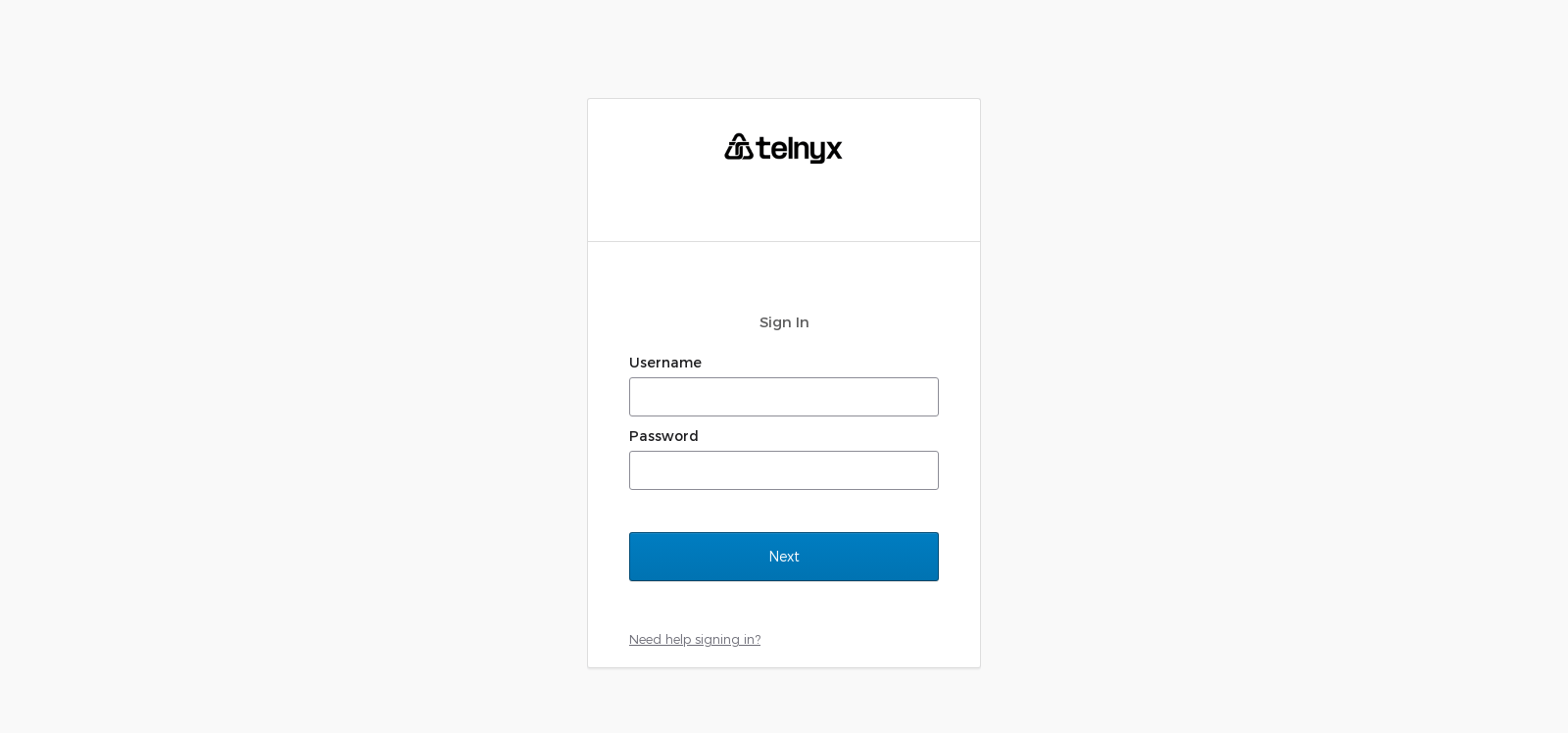
Source: Screenshot of the telynyx Okta phishing site
The notorious cybercriminal group, Scattered Spider, previously known for high-profile attacks on MGM and Caesars, has now broadened its scope to aggressively target the finance and insurance industries, according to a recent report from Resilience threat researchers. Using sophisticated tactics and lookalike domains, this group has orchestrated attacks on over 30 companies, demonstrating a dangerous evolution in their operational tactics.
Scattered Spider, also known by multiple aliases including 0ktapus and Muddled Libra, is a financially motivated threat actor group active since May 2022. Originally focusing on telecommunications firms to facilitate SIM swaps, the group has significantly widened its targeting spectrum to include a variety of industries from food services to video games, utilizing elaborate phishing schemes to breach corporate defenses.

A hallmark of Scattered Spider‘s operations involves the creation of convincing lookalike domains to host fake Okta and Content Management System (CMS) login pages. This method has been particularly effective in deceiving employees into entering their credentials, thinking they are accessing legitimate company resources. For example, domains such as “victimname-okta[.]com” mimic official login portals, leading to credential theft and unauthorized access to sensitive corporate data.
Investigations into Scattered Spider’s phishing kits revealed distinct fingerprints that link back to their operations, including derogatory and hateful language within URL paths, and a distinct pattern in the data handling backend, like POST requests directed to “/f*ckyou[.]php”. These kits not only steal credentials but are also linked to broader criminal networks, illustrating the deep connections within the cybercriminal underworld.

April 2024 marked another bold move by Scattered Spider, targeting Charter Communications with domains crafted to intercept VPN credentials, showcasing their evolving strategy and precision in selecting high-value corporate targets. This indicates a shift from traditional telecommunication targets to broader sectors, increasing the potential impact of their attacks.
For organizations at risk, proactive defense strategies are critical. Monitoring for the registration of lookalike domains, training employees to recognize and report phishing attempts, and employing advanced security measures to detect and respond to suspicious activities are vital steps in thwarting these attacks. Companies are also encouraged to enhance their authentication processes and consider multi-factor authentication to mitigate the risk of credential theft.