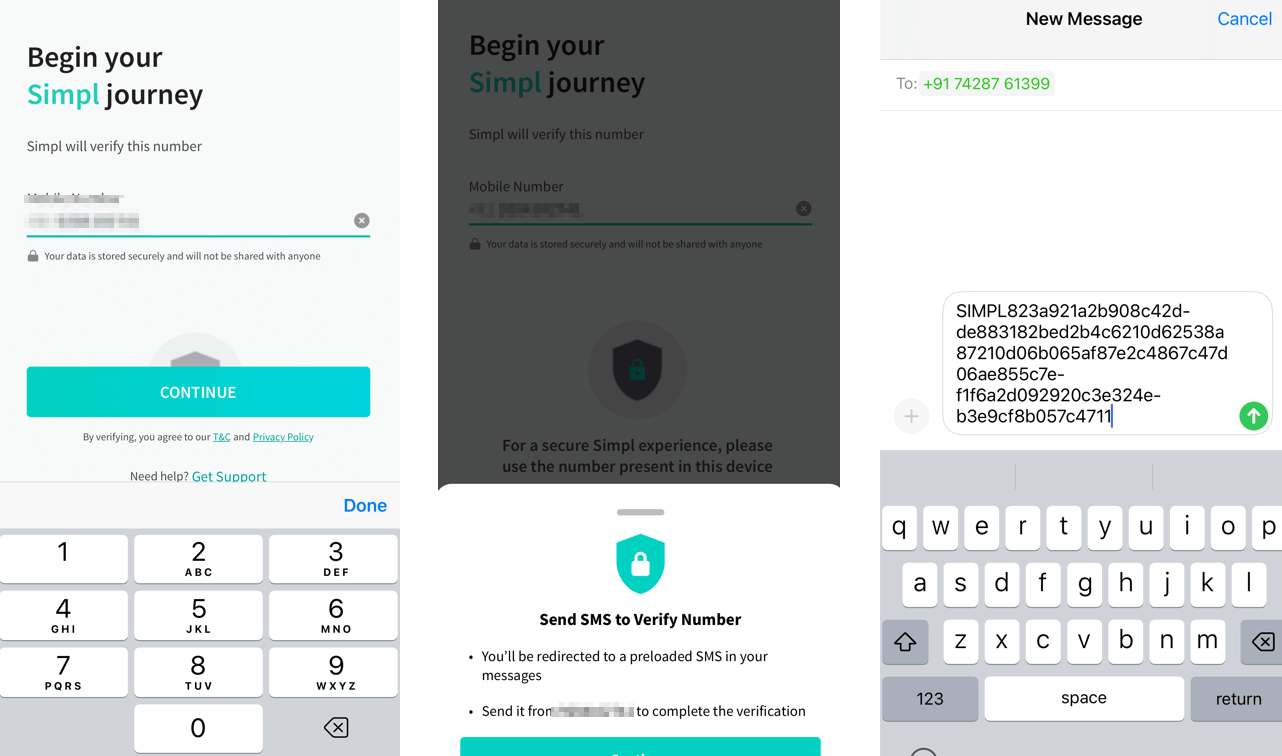
Simpl app’s number verification message
A new, insidious phishing scam impersonating India’s Regional Transport Office (RTO) has been detected, preying on unsuspecting Android users via WhatsApp. The scam, disguised as an official notice about traffic violations, lures victims into downloading a malicious app named “VAHAN PARIVAHAN.apk.”
According to Cyble Research and Intelligence Labs (CRIL), this malware is particularly stealthy, operating in the background to harvest sensitive data like SMS messages and contact lists, even intercepting verification codes from financial apps like Simpl. It then relays this information to a Telegram bot controlled by the attackers.
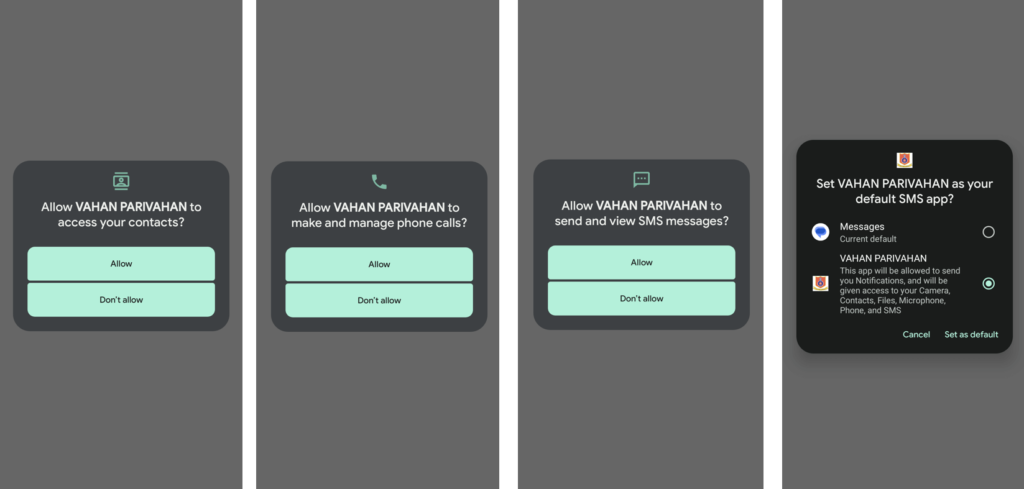
Unlike previous malware campaigns that used phishing screens mimicking Indian banks, this new malware lacks a launcher activity. This absence means the app icon does not appear in the app drawer, making it difficult for victims to detect and uninstall the malware. Instead, the application operates silently in the background, sending and collecting SMS messages and contact lists from the infected device.
Upon installation and opening of the application, the malware prompts the user to grant permissions for SMS and contact access. The main activity loads a blank screen into the WebView and asks the user to designate the “VAHAN PARIVAHAN” application as the default SMS application. Concurrently, the malware sends device information, including the model number, version number, battery status, carrier name, and other relevant details, along with the contact list from the infected device, to a Telegram bot URL: hxxps://api[.]telegram.org/bot7487929666
/sendDocument.
After gathering data and obtaining necessary permissions, the malware initiates a background service that connects to the Firebase URL “hxxps://numnumfour-default-rtdb.firebaseio[.]com/-1002221216537/.json.” The service retrieves data, including lists of phone numbers and text messages, and uses this information to send SMS messages from the infected device to the numbers obtained from the Firebase server.
Upon accessing the Firebase URL, CRIL observed a JSON response containing Indian phone numbers and random text. A similar URL, “hxxps://hookuptolookup-default-rtdb[.]firebaseio.com/-1002118750305/.json,” was also identified, managing data with phone numbers and text messages. This suggests a broader campaign utilizing multiple Firebase URLs.
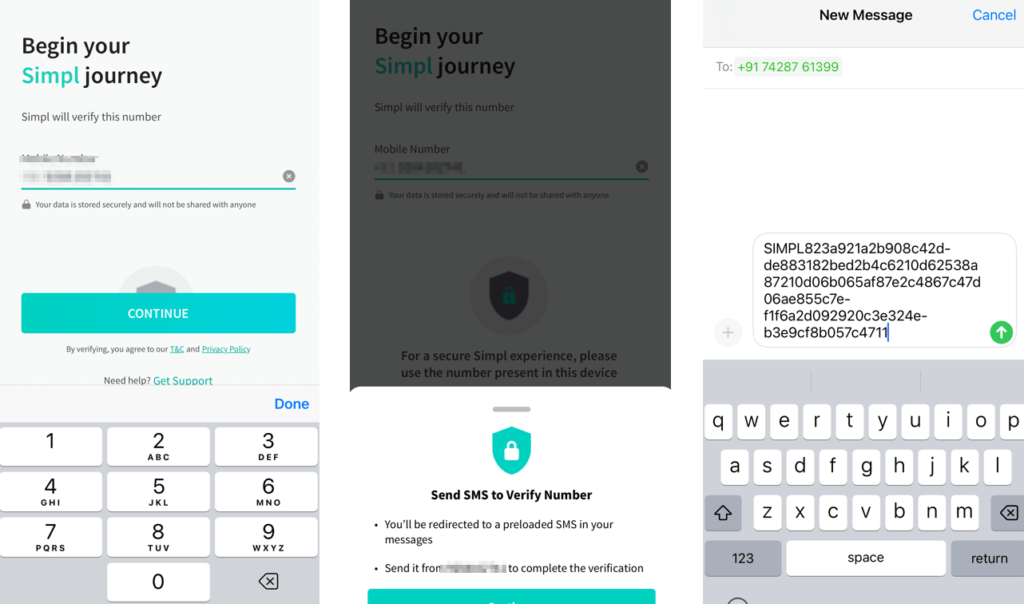
One notable observation in the data, indicated under ID 11357, includes text messages beginning with “SIMPL,” linked to the verification process of the Simpl app, a Buy Now, Pay Later (BNPL) service in India. This tactic, previously identified by CRIL in December 2022, involves sending verification messages from the victim’s device to enable threat actors to verify UPI apps on their own devices.
To protect against these sophisticated attacks, CRIL recommends the following cybersecurity best practices:
- Be wary of unsolicited messages, especially those containing links or attachments.
- Always verify the authenticity of messages from official sources.
- Download apps only from trusted platforms like the Google Play Store.
- Keep your device and apps updated with the latest security patches.
- Use a reputable antivirus and internet security solution.