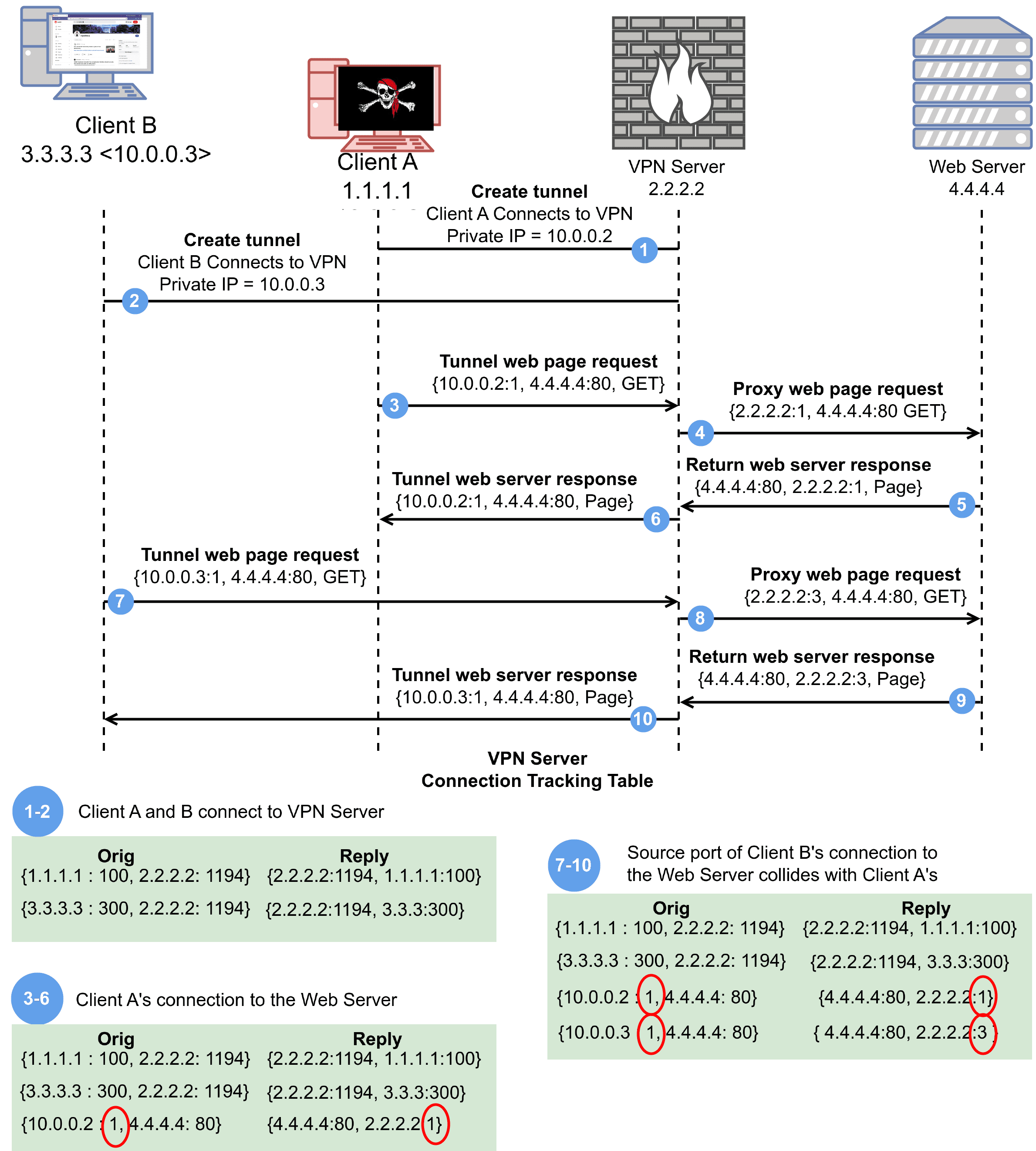
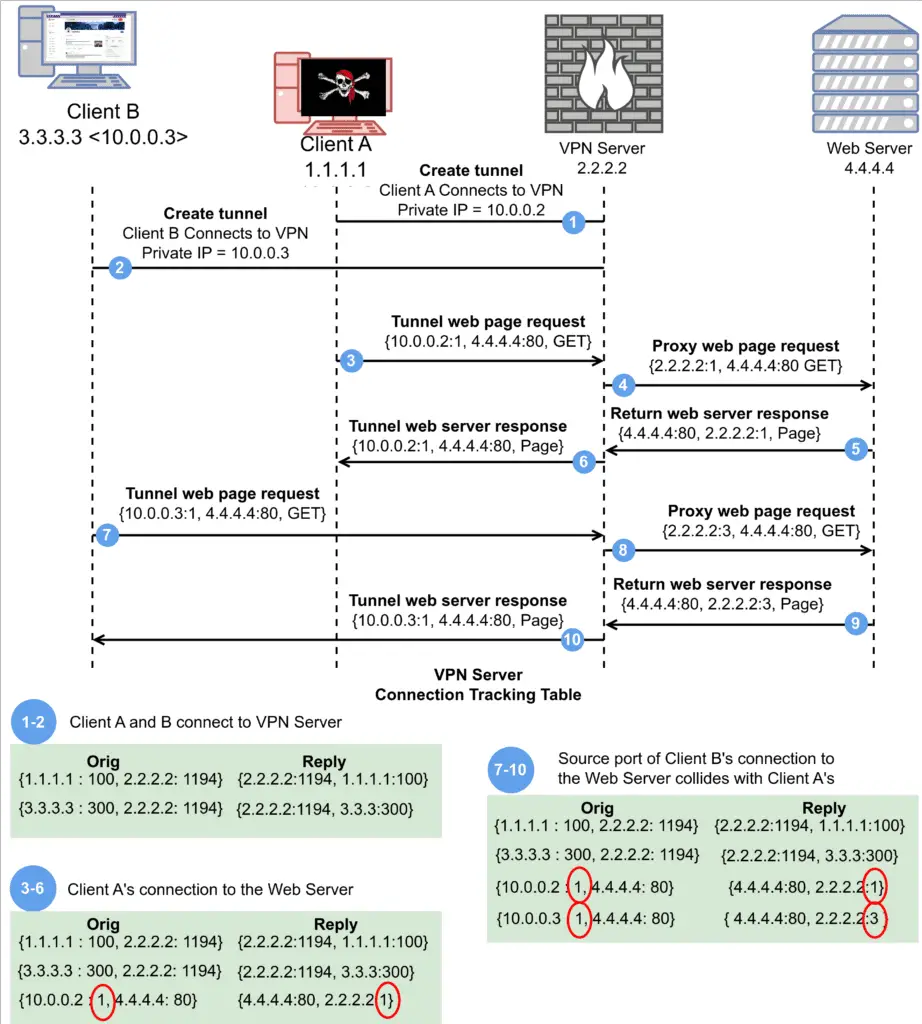
This diagram depicts a typical interaction between two VPN clients and a VPN server.
A new study presented at the Privacy Enhancing Technologies Symposium (PETS) 2024 has revealed a vulnerability in popular VPN protocols like OpenVPN and WireGuard. This flaw, dubbed “port shadow,” could potentially undermine the very privacy VPNs are designed to protect.
Researchers from Citizen Lab and other institutions have discovered that VPN software running on Linux or FreeBSD can make users less secure, allowing attackers to intercept and manipulate traffic, potentially even deanonymizing connections. This “port shadow” technique exploits shared resources within VPN servers, giving attackers the ability to act as a network router, even if they’re not physically near the victim.
The implications of this discovery are far-reaching, particularly for individuals who rely on VPNs for sensitive activities like journalism, activism, or whistleblowing. By exploiting the “port shadow” vulnerability, malicious actors could potentially compromise the confidentiality and integrity of VPN connections, exposing users to surveillance and other threats.
The vulnerability‘s technical details are complex, but essentially, it allows an attacker to act as a rogue router within the VPN server, even if they are not physically located near the victim. This unprecedented level of access grants attackers a range of capabilities, from eavesdropping on unencrypted traffic to redirecting connections to malicious websites.
The research team has responsibly disclosed the vulnerability to relevant parties, including VPN developers and operating system maintainers. However, the currently available mitigations are primarily server-side and require specific firewall configurations. Until these mitigations are widely adopted, users are advised to exercise caution when selecting VPN services, opting for those that have explicitly addressed the “port shadow” vulnerability.
In the meantime, users can mitigate the risk by choosing alternative VPN protocols like Shadowsocks or Tor, which do not rely on the same connection tracking frameworks that make OpenVPN and WireGuard susceptible to this attack.
The research underscores the inherent risks in using common VPN software, especially when connecting to shared servers. The port shadow exploit demonstrates that even tools designed to enhance privacy can, under certain conditions, make users more vulnerable. This discovery calls for a reevaluation of VPN security practices and the development of more robust mitigation strategies.