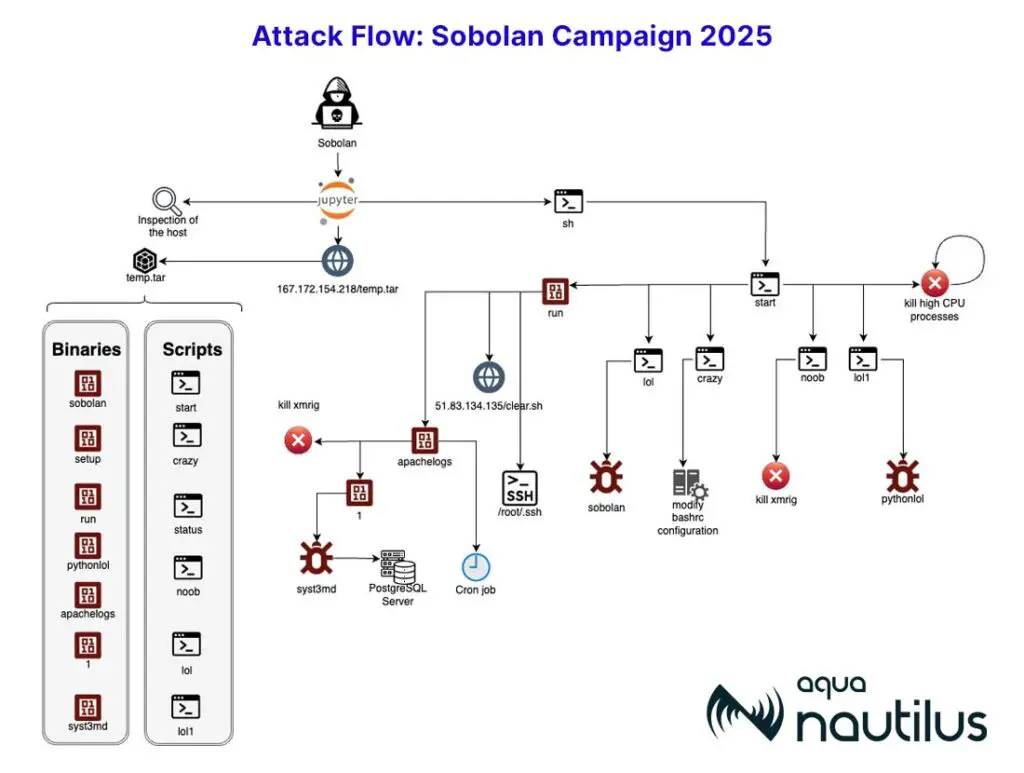
Sobolan campaign attack flow | Image: Aqua Nautilus
Aqua Nautilus researchers have uncovered a new malware campaign that specifically targets interactive computing environments like Jupyter Notebooks, posing a significant threat to cloud-native infrastructure. The Sobolan malware campaign utilizes a multi-stage attack chain to infiltrate and compromise systems, deploying cryptominers and establishing persistent backdoors for long-term control.
The attack begins with exploiting an unauthenticated JupyterLab instance, allowing the attacker to download a compressed archive containing malicious binaries and shell scripts. Once executed, these scripts initiate a series of processes designed to hijack system resources for cryptomining, establish persistence, and evade detection.
The Sobolan malware employs several techniques to maintain its presence on the compromised system. It modifies the ~/.bashrc file to display a fake login prompt, effectively restricting terminal access unless the attacker’s hardcoded password is provided. Additionally, it creates cron jobs to ensure the continued execution of malicious components.
The attackers utilize various binaries and scripts to achieve their objectives. The lol and lol1 scripts are responsible for running the cryptominers pythonlol and sobolan, while the noob script kills processes with high CPU usage, likely to prevent interference with the cryptomining operation. The run binary inspects SSH credentials and executes the apachelogs binary, which in turn runs a service that terminates competing cryptominers and executes the syst3md cryptominer.
This campaign highlights the increasing risks faced by organizations utilizing interactive computing environments in the cloud. The exploitation of unauthenticated instances and the deployment of sophisticated malware like Sobolan underscore the need for robust security measures in cloud-native environments.
Organizations are recommend implementing strong authentication mechanisms, regularly updating software to patch vulnerabilities, and employing runtime security solutions to detect and prevent malicious activities.
Related Posts:
- Log4j Campaign Exploited to Deploy XMRig Cryptominer
- Recruitment Scam Targets Job Seekers with Fake CrowdStrike Branding
- Scattered Spider Targets the Cloud: A Growing Threat to the Insurance and Financial Sectors
- Critical TeamCity Flaws Exploited: Ransomware, Cryptominers, and More Target Businesses