Flow of the communication mechanism via Outlook API for Squidoor | Image: Unit 42
A newly discovered stealthy backdoor named Squidoor has been identified targeting high-profile organizations across Southeast Asia and South America. According to Unit 42 researchers, Squidoor is linked to a suspected Chinese threat actor known as CL-STA-0049 and has been in active use since at least March 2023. The malware is highly modular and designed for both Windows and Linux, utilizing multiple covert communication methods to maintain persistent access.
The threat actor behind Squidoor has been observed targeting governments, defense, telecommunication, education, and aviation sectors. Their primary objective appears to be collecting sensitive information from compromised organizations, including intelligence on high-ranking officials and key personnel.
Unit 42 researchers explain: “The observed activity includes collecting sensitive information from compromised organizations, as well as obtaining information about high-ranking officials and individuals at those organizations.”
The attack typically starts by exploiting vulnerabilities in IIS servers, allowing the attackers to deploy multiple web shells that serve as persistent backdoors. These web shells facilitate remote command execution and lateral movement across the network.
Squidoor is an advanced modular backdoor engineered for stealth. Unlike conventional malware, it supports multiple covert communication methods to avoid detection, including:
- Outlook API tunneling
- DNS tunneling
- ICMP tunneling
- Reverse TCP and UDP connections
- Named pipes for internal communication (Windows only)
Researchers from Unit 42 highlight Squidoor’s adaptability: “Squidoor offers a range of different protocols and methods operators can use to configure the malware to communicate with its C2 server. The Windows version of Squidoor grants the attackers 10 different methods for C2 communication, and the Linux version allows nine.”
To avoid detection, the attackers leverage a rarely observed Living-Off-The-Land Binary and Scripts (LOLBAS) technique, abusing Microsoft Console Debugger (cdb.exe) to execute Squidoor’s payload. The attackers renamed cdb.exe to fontdrvhost.exe, using it to execute shellcode directly in memory.
Unit 42 notes: “While using cdb.exe is a known living-off-the-land technique, its use is quite rare and has only been reported a handful of times.”
Once executed, Squidoor employs a modular payload system that allows it to:
- Collect host reconnaissance data (username, OS type, IP address)
- Inject code into processes (e.g., mspaint.exe, conhost.exe, taskhostw.exe)
- Exfiltrate files
- Execute arbitrary commands
- Deploy additional malware
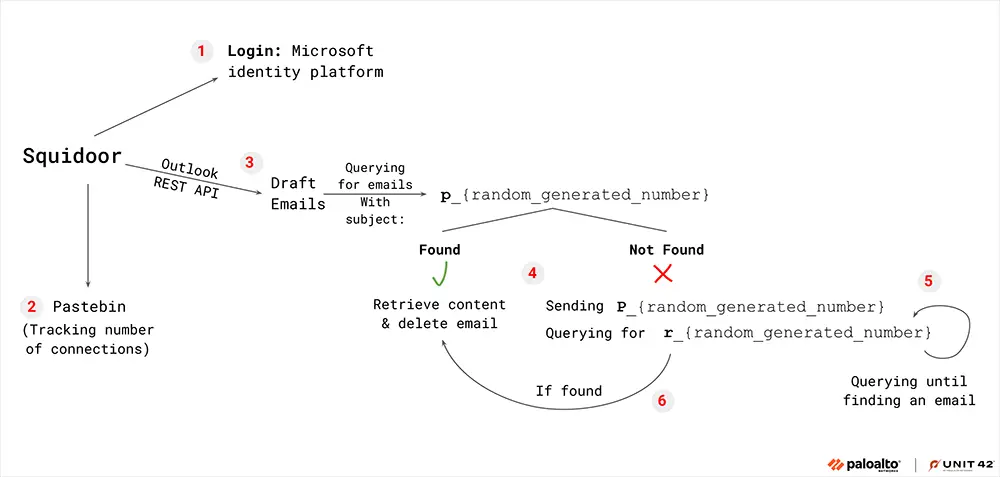
One of Squidoor’s most sophisticated techniques is its abuse of Outlook’s API for covert command-and-control communication. When configured to use the COutLookTransChannel, Squidoor logs into Microsoft’s identity platform using a hardcoded refresh token. It then queries emails for hidden commands embedded in the drafts folder.
Researchers describe this process: “Squidoor sends an HTTP GET request to a specific Pastebin page that is hard coded in its configuration. The Pastebin page is named Local365, and only contains the number 1. We suspect the attackers monitor these GET requests to Pastebin as a method to track how many implants have connected via the Outlook API.”
Attackers then use draft emails to send encoded commands to infected hosts, ensuring that no outbound network traffic raises suspicion.
Once inside a network, the attackers use Windows Management Instrumentation (WMI), cURL, and Impacket to spread Squidoor implants to other machines. The malware maintains persistence through a scheduled task disguised as a Microsoft AppID service.
Squidoor’s persistence was achieved using a scheduled task named Microsoft\Windows\AppID\EPolicyManager, which executed the shellcode.
Additionally, Squidoor can send commands to other Squidoor implants within the same network using named pipes, reducing the need for external C2 communication.
Related Posts:
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs
- Chinese Threat Groups Leverage Ransomware for Political Gain
- A New Set of Tools for Cyber Espionage: Targeting the Middle East, Africa, and the US
- New VMware Findings: Kernel Drivers’ Vulnerabilities Risk Total Device Takeover
