Source: vanhoefm
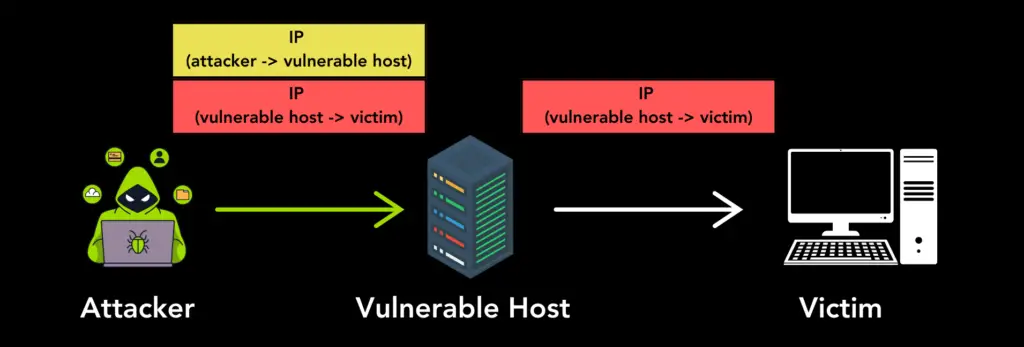
A report by security researcher Mathy Vanhoef, in collaboration with Top10VPN, has revealed critical vulnerabilities in widely-used tunneling protocols. Affecting over 4.26 million hosts worldwide, these flaws enable attackers to hijack systems for anonymous attacks, unauthorized network access, and denial of service (DoS). The vulnerabilities will be presented at the upcoming USENIX 2025 conference in Seattle.
Tunneling protocols such as IPIP, GRE, 4in6, and 6in4 lack built-in authentication and encryption, leaving systems open to exploitation. According to the report, “Internet hosts that accept tunneling packets without verifying the sender’s identity can be hijacked to perform anonymous attacks and provide access to their networks.”
Identifiers:
-
- GRE, GRE6: CVE-2024-7595
- 4in6, 6in4: CVE-2025-23018/23019
- GUE: CVE-2024-7596 (no known affected hosts)
The vulnerabilities affect:
- VPN servers
- ISP home routers
- Core internet routers
- CDN nodes (including major providers like Meta and Tencent)
Scope of Impact
- Total vulnerable hosts: 4.26 million
- Spoofing-capable hosts: 1.85 million
- Most affected countries: China, France, Japan, the U.S., and Brazil
The vulnerabilities expose hosts to various malicious activities:
- One-Way Proxy Attacks: Hijacked hosts can relay traffic, concealing the attacker’s identity.
- DoS Amplification: Attacks like the “Ping-Pong Amplification” create excessive traffic between hosts, overwhelming networks.
- Off-Path TCP Hijacking: Enables man-in-the-middle attacks on network traffic.
- Tunneled-Temporal Lensing (TuTL): A novel attack delivering bursts of malicious traffic to disrupt victim systems.
The impact of these vulnerabilities is far-reaching, potentially enabling new Denial-of-Service (DoS) techniques, DNS spoofing, TCP hijacking, and various other attacks. The most affected countries include China, France, Japan, the U.S., and Brazil, with over 11,000 Autonomous Systems (AS) impacted globally.
Vanhoef’s research also highlights that almost 40% of vulnerable ASs fail to filter spoofing hosts, further amplifying the risk. This means attackers can not only remain anonymous but also make it extremely difficult to trace the attack back to its source.
In particular, the report highlights, “Spoofing-capable hosts can have ANY IP address as the source address in the inner packet, so not only does an attacker remain anonymous, but the compromised host also becomes much harder to discover and secure.“
Researchers have developed scanning scripts to help IT administrators test for vulnerabilities in their systems. For a deeper dive into the findings and technical details, consult the full paper on Top10VPN.
Related Posts:
- DNS Tunneling: The Hidden Threat Exploited by Cyberattackers
- Hacker group Anonymous controls over 400 Russian cameras
- Anonymous hacks the Russian Defense Ministry