Zscaler ThreatLabz has uncovered a novel malware campaign leveraging Node.js applications for Windows to deliver cryptocurrency miners and information stealers. Dubbed NodeLoader, this malware takes advantage of Node.js’s flexibility and the relative scarcity of antivirus signatures targeting JavaScript-based threats.
NodeLoader stands out for its innovative use of Node.js, a framework typically associated with web development rather than native desktop applications. According to Zscaler ThreatLabz, “The attackers employ Node.js compiled executables to deliver second-stage payloads, including XMRig, Lumma, and Phemedrone Stealer.”
The malware uses the pkg module of Node Package Manager (NPM) to package Node.js code into standalone Windows executables. These executables exploit legitimate tools like sudo-prompt, a GitHub-hosted module, to escalate privileges, bypassing User Account Control (UAC) in certain configurations.
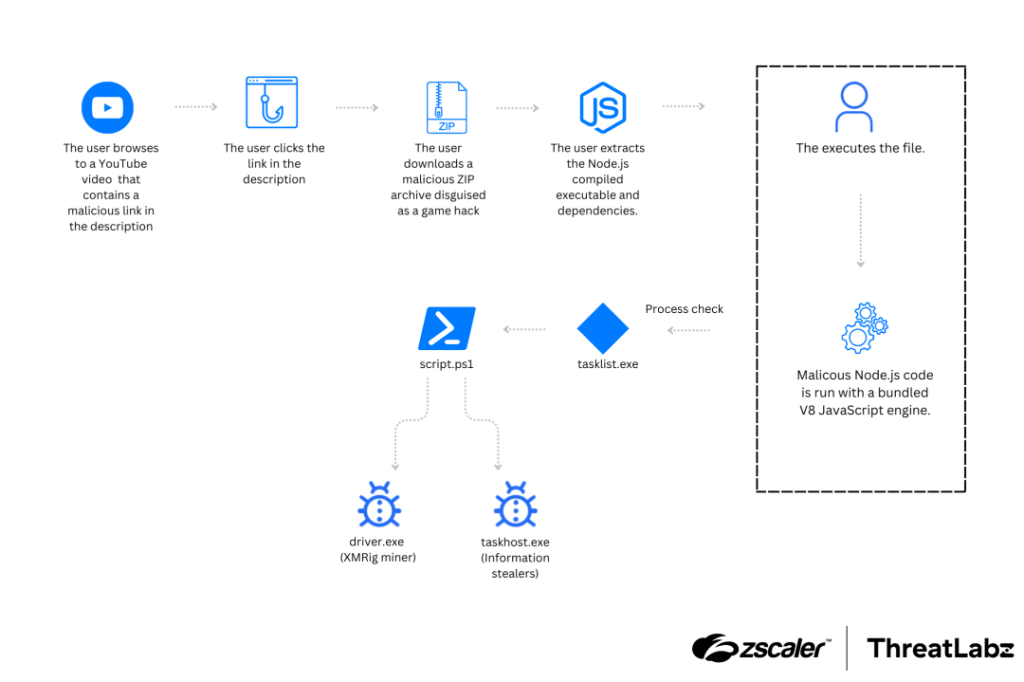
NodeLoader employs a multi-stage attack chain that relies heavily on social engineering:
- Initial Distribution:
- Threat actors distribute NodeLoader via fake gaming utility websites and malicious links embedded in popular YouTube videos.
- These links often mimic legitimate platforms, such as Korepi, to lure unsuspecting users.
- Victims are enticed to download a ZIP file containing the malicious NodeLoader executable.
- Execution and Evasion:
- Once executed, NodeLoader uses the V8 JavaScript engine to run its payload.
- The malware employs the attrib command to hide created directories and files, ensuring stealth.
- Privilege Escalation:
- Using sudo-prompt, NodeLoader runs batch commands with administrative privileges.
- In one instance, Zscaler observed, “If UAC is configured to not display a prompt, the batch file executes in elevated mode without user consent.”
- Payload Deployment:
- NodeLoader downloads PowerShell scripts to install second-stage payloads, including:
- XMRig Cryptocurrency Miner: Exploits system resources for mining cryptocurrency.
- Phemedrone Stealer: Exfiltrates browser data, including login credentials, to a Telegram channel.
- Lumma Stealer: Dynamically injects its payload into a legitimate process (e.g., RegAsm.exe).
- NodeLoader downloads PowerShell scripts to install second-stage payloads, including:
A key challenge posed by NodeLoader is its ability to evade detection. Zscaler notes: “When compiled using the pkg NPM module, a single line of code results in a large Windows binary exceeding 35 MB. This large file size complicates detection for some security products.” Additionally, the limited number of antivirus signatures for malicious JavaScript-based code enables the malware to operate with minimal resistance.
Related Posts:
- Zscaler found 150 Android apps infected with Windows malware
- Sophisticated Campaign Targets Manufacturing Industry with Lumma Stealer and Amadey Bot
- Zscaler Report: 300% increase in phishing attacks delivered over SSL
- The Rise of Mac Malware: 2024 Threat Report Reveals Alarming Trends
- AI Powers a Phishing Frenzy – Zscaler Report Warns of Unprecedented Threat Wave