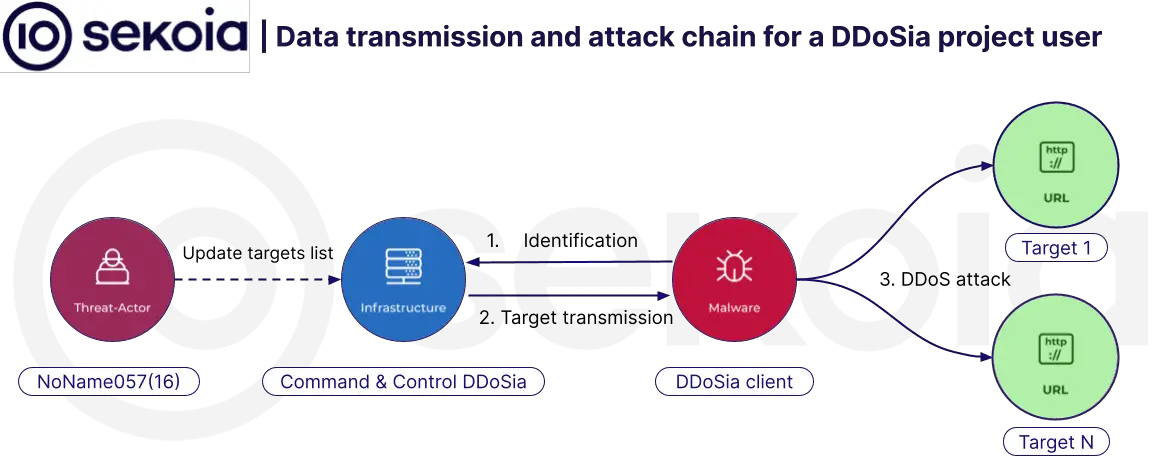
The war in Ukraine ignited a new breed of cyber conflict, where hacktivist groups act as proxies for state interests. Russia’s NoName057(16) has become synonymous with the DDoSia project, a relentless campaign of DDoS attacks that target nations supporting Ukraine. Unlike groups focused on data theft or espionage, NoName057(16) seeks to overwhelm and disrupt, turning the digital world into a tool of geopolitical warfare.
Since SEKOIA.IO began tracking them, their methods have evolved, revealing a persistent and adaptable threat that follows the shifting tides of the conflict and broader tensions with the West.
DDoSia Evolves: New Features, Shifting Infrastructure

On November 11, 2023, DDoSia received a major update, expanding compatibility for a wider range of devices and operating systems. Notably, administrators geographically tailored versions, cautioning Russian users to employ VPNs to mask their location when participating in attacks.
This new version introduced more sophisticated data encryption, allowing finer tracking of DDoSia users. This data likely helps administrators gauge the project’s effectiveness and could be a valuable resource for law enforcement and threat intelligence efforts.
Despite enhanced software, NoName057(16) struggles with C2 (command-and-control) server stability. Frequent takedowns have forced them to switch servers at a dizzying pace in 2024, sometimes making multiple changes in a single day. This suggests concerted efforts to disrupt their operations. Interestingly, they lack features to automate C2 changes, leading to downtime for users.
Shifting Targets: Following the Frontlines
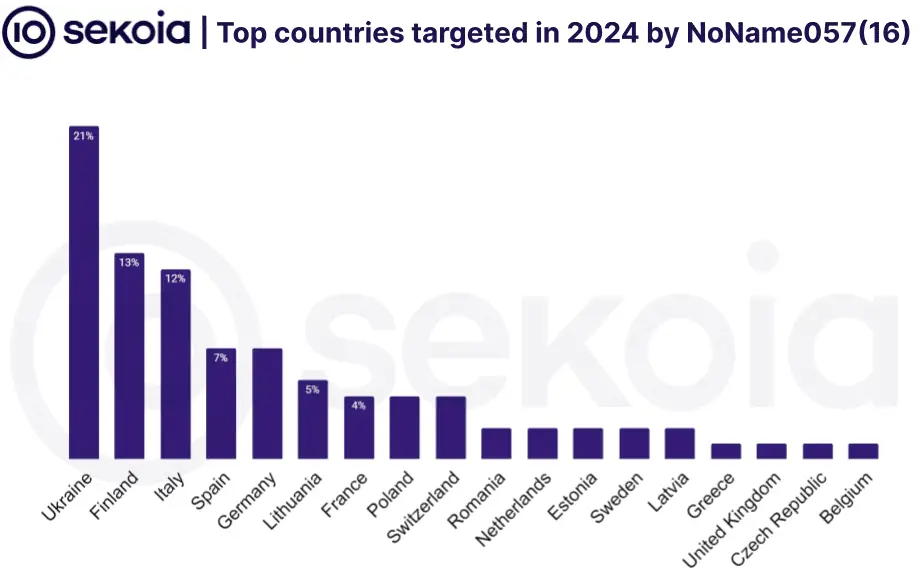
SEKOIA.IO’s tracking reveals NoName057(16)’s targets mirror Russia’s geopolitical adversaries. Ukraine remains in their crosshairs, but Finland and Italy were hit hard in early 2024, likely due to their pro-Ukraine stance within NATO. Most recently, a surge of DDoSia attacks hit Japan after its substantial aid package for Ukraine, a clear display of retaliatory intent.
Focus on Disruption: What does it Achieve?
Governments remain the primary targets, with over half of attacks impacting public sector entities. However, a notable portion attacks the transportation and banking sectors. While DDoSia attacks rarely cause lasting damage, the disruptions serve several purposes:
- Symbolic Retaliation: Punishing countries supporting Ukraine.
- Psychological Warfare: Disruptions create a sense of unease among civilian populations, undermining confidence.
- Smoke and Mirrors: They may mask more potent attacks happening behind the scenes.
The Growing Threat
NoName057(16)’s user base and alliances with other hacktivist groups are expanding rapidly. While DDoSia Project themselves might be mere annoyances, the group’s evolution highlights a concerning trend:
- State-sanctioned Cyber Disruption: Russia may offer these groups protection or even direction, allowing attacks to align with government aims.
- The “Hacktivist” Toolkit Spreads: Their DDoSia software is freely shared, meaning copycat groups are likely to emerge.
Staying Ahead: The Defense Challenge
While NoName057(16)’s attacks are often unsophisticated, their relentless activity, evolving tactics, and geopolitical alignment make them a disruptive force. To defend against them, we must:
- Focus on Resilience: Ensuring critical services can withstand temporary outages mitigates the bulk of the threat.
- Proactive Threat Intelligence: Tracking infrastructure, tools, and communication channels like SEKOIA.IO does is key to anticipating shifts in focus.
- International Cooperation: As attacks often cross borders, collaboration among cybersecurity agencies is crucial for takedowns and attribution.