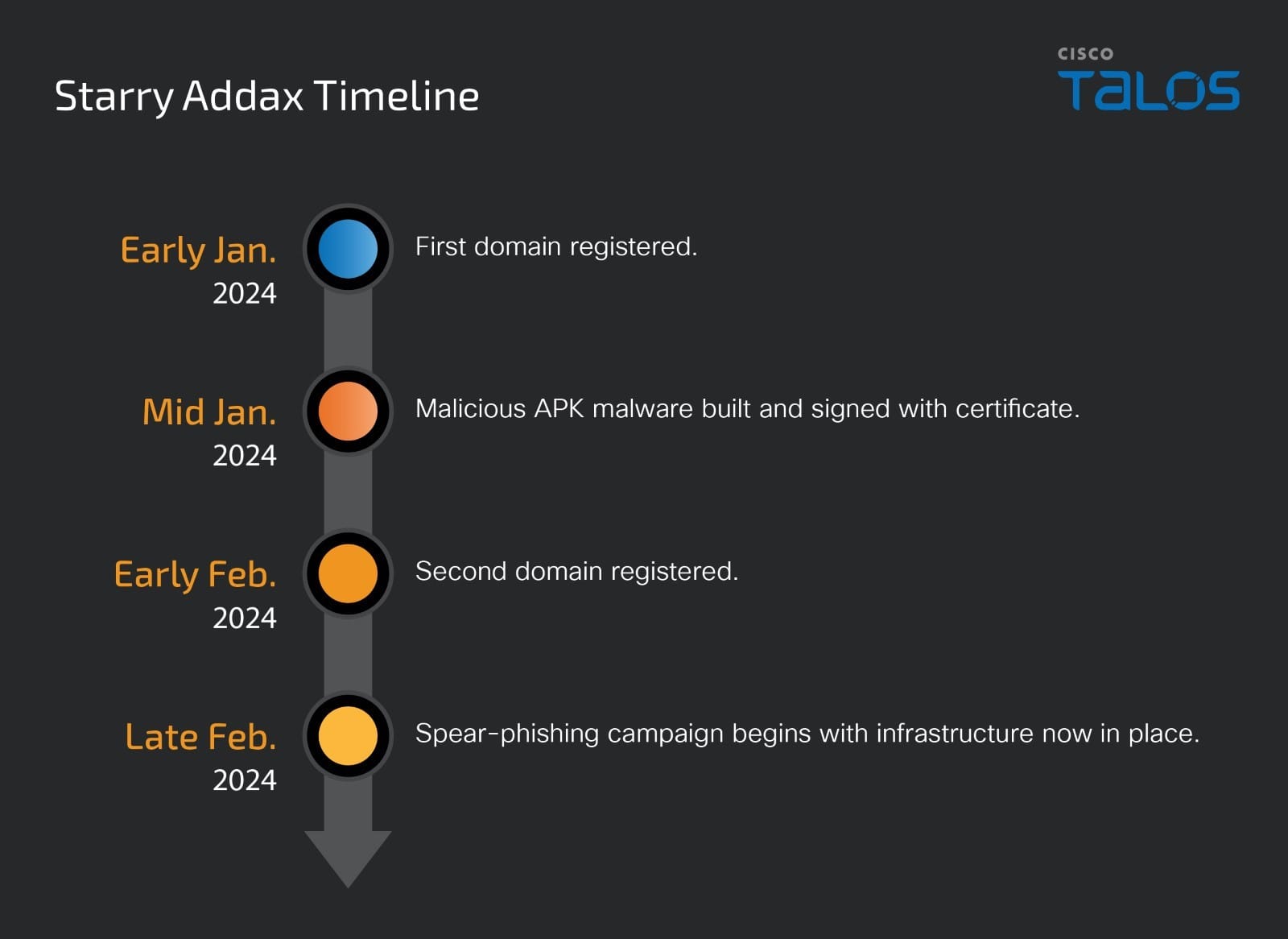
Security researchers at Cisco Talos have uncovered a sophisticated new malware campaign orchestrated by a threat actor they’ve named “Starry Addax.” This group is aggressively targeting human rights activists with ties to the Sahrawi Arab Democratic Republic (SADR) cause, utilizing both Android malware and credential-harvesting techniques.
Dual-Pronged Attack Strategy
Starry Addax initiates attacks with carefully crafted spear-phishing emails designed to deceive individuals of interest, particularly those involved in human rights advocacy in Morocco and the Western Sahara region. These emails might request the installation of a fake Sahrawi News Agency mobile app or contain content specifically relevant to the Western Sahara issue.
Victims who install the malicious app, known as “FlexStarling,” unwittingly grant it access to a vast array of sensitive data on their Android devices. Those using Windows machines are redirected to fraudulent login pages impersonating popular media websites, where their credentials are stolen.
Stealthy Operations and Extensive Capabilities
FlexStarling stands out as a potent and tailor-made piece of malware. It demands a wide range of permissions on Android devices, enabling it to extract call logs, SMS messages, contact lists, and more. The malware also incorporates anti-emulation techniques, allowing it to evade standard analysis and detection tools.
Furthermore, Starry Addax’s custom-built infrastructure appears designed for maximum stealth. By avoiding the use of commodity malware or readily available spyware, the group reduces its risk of exposure and aims to maintain a long-term presence on infected devices.
A Growing Threat

The timing of the artifacts associated with this campaign suggests that Starry Addax may be ramping up its operations. Security experts warn that individuals associated with the SADR cause, as well as human rights activists in the region, need to maintain a state of heightened vigilance. It’s anticipated that the threat actor could develop additional malware variants or expand the scope of its infrastructure.