North Korean APT Group Kimsuky Exploits DMARC Misconfigurations for Sophisticated Phishing Attacks

Email security has long been a critical pillar in defending organizations against cyberattacks, but recent reports reveal that even widely trusted protections like Domain-based Message Authentication, Reporting & Conformance (DMARC) can be exploited when misconfigured. A recent report by Sheila Hara, Senior Director of Product Management at Barracuda, highlights how the North Korean advanced persistent threat (APT) group Kimsuky has been leveraging DMARC misconfigurations to run highly targeted spear-phishing campaigns, threatening both private and public sectors globally.
Kimsuky, a well-documented North Korean APT group, operates under the Reconnaissance General Bureau and has been notorious for targeting think tanks, academia, and media outlets to gather intelligence on foreign policy and nuclear matters. Their latest tactic, as outlined by Hara, involves exploiting poorly configured DMARC policies to spoof legitimate domains and deceive email recipients.
“This isn’t just a geopolitical concern; it’s a reminder that email security flaws, however small, can be exploited by anyone with malicious intent,” Hara states.
DMARC plays a crucial role in preventing email-based attacks by verifying the legitimacy of emails using SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) protocols. These systems ensure that emails are sent from authorized servers, preventing spoofing. However, as Hara warns, “DMARC can only do its job if it’s configured correctly.”
Many organizations fall victim to incomplete or weak DMARC policies, where emails that fail SPF or DKIM checks are not properly quarantined or rejected. Kimsuky exploits these misconfigurations, sending phishing emails that mimic trusted sources like universities or research institutes. These spoofed emails often pass initial checks and make their way to the inbox, undetected by weak DMARC settings.
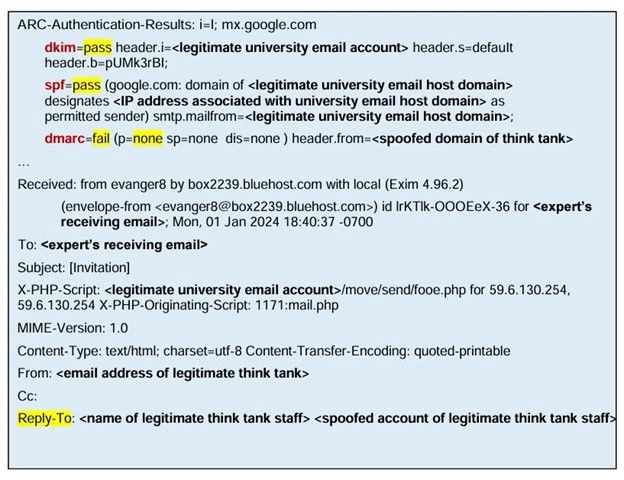
Example of a Kimsuki email attack (Source: Joint Cybersecurity Advisory)
In one documented case, Kimsuky sent a seemingly legitimate email, inviting a target to speak at a North Korean policy conference. The email passed SPF and DKIM checks, but due to improper DMARC configuration, the email was not blocked. This led to a successful spear-phishing attempt, showcasing the attackers’ ability to manipulate existing email systems.
What makes this scenario even more concerning is the prevalence of DMARC misconfigurations across industries. Hara highlights that many organizations either do not have DMARC policies in place or, worse, rely on a “monitor” policy that merely logs potential threats without taking action. This practice gives a false sense of security, leaving systems vulnerable to phishing attacks.
“Misconfigurations are more common than you’d think,” writes Hara. She adds, “Even when they do have a DMARC policy, many organizations use a ‘monitor’ setting, which fails to block the very threats they are trying to prevent.”
Related Posts:
- Critical Vulnerability in Hosted Email Services Exposes Users to Spoofing Attacks
- North Korean Hackers Hone Social Engineering Skills, Abuse DMARC to Target Foreign Policy Experts
- From Spear-Phishing to Zero-Day: Lazarus Group’s Latest Cyber Strategies
- Kimsuky APT: New TTPs Revealed in Rapid7 Cybersecurity Report