Image: Jamf Threat Labs
Researchers from Jamf Threat Labs have discovered multi macOS malware samples embedded within applications developed using the Flutter framework, potentially linked to North Korean Advanced Persistent Threat (APT) actors. This malicious campaign leverages Flutter’s inherent obfuscation, making it challenging for researchers to detect and analyze the code within these applications.
Flutter, a popular framework by Google, is commonly used for developing cross-platform applications. While its primary design goal is to simplify app development, it inadvertently provides an ideal cover for malicious activities. The malicious macOS applications were discovered in late October on VirusTotal, where they initially appeared harmless. “The domains and techniques in the malware align closely with those used in other DPRK malware,” noted Jamf Threat Labs, suggesting a potential North Korean origin.
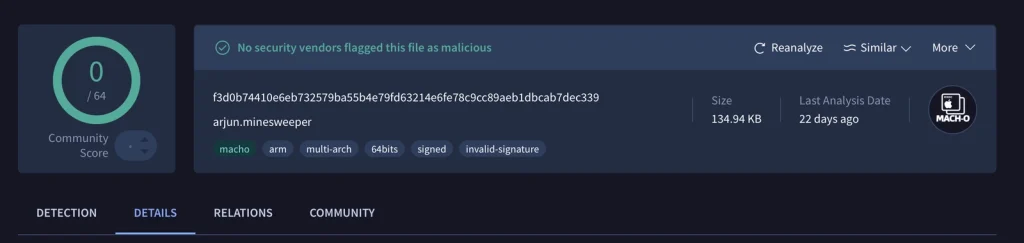
One app that stood out was titled New Updates in Crypto Exchange. When launched, the application presented users with a simple minesweeper game. However, beneath this innocent-looking interface lurked a complex architecture designed to communicate with an external domain. Jamf Threat Labs observed that the app made a network request to mbupdate[.]linkpc[.]net upon execution—a domain previously associated with North Korean malware.
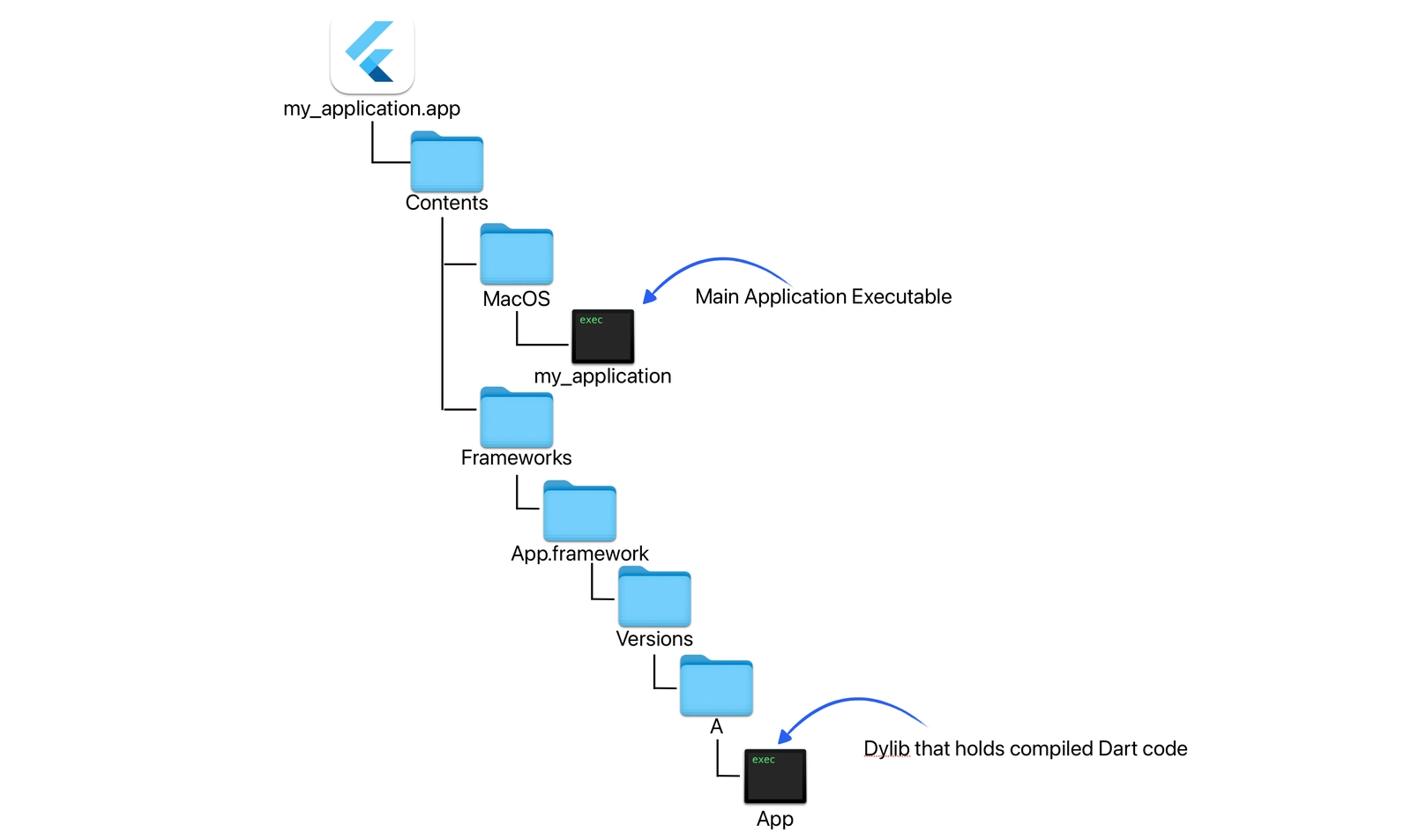
The malware’s use of Flutter adds a layer of difficulty to malware analysis techniques. The malicious code resides in a “dylib” file within the application package, but unlike typical shared libraries, Flutter’s unique compilation process obscures this file’s presence. “Applications built using Flutter lead to a uniquely designed app layout that provides a large amount of obscurity to the code,” explained the researchers.
In addition to the network communication, Jamf’s team discovered strings in the application indicating support for AppleScript execution. By redirecting traffic to a local environment, the team confirmed that the malware could execute AppleScript commands sent from a remote server. “Our testing showed the stage two AppleScript must be written backward in order to be successfully executed by the malware,” the report details.
The malware was signed with developer certificates, which Apple has since revoked. Researchers speculate that this campaign could represent a trial run rather than a fully-fledged attack. “This theory stems from the fact that the actor is known for putting together highly convincing social engineering campaigns,” the researchers noted, raising the possibility that the actor is testing methods to slip through Apple’s notarization process and evade antivirus systems.
Related Posts:
- Jamf Threat Labs Uncovers a Stealthy Malware Strain from BlueNoroff APT
- Chrome 131 Rolls Out with Security Fixes and Performance Enhancements