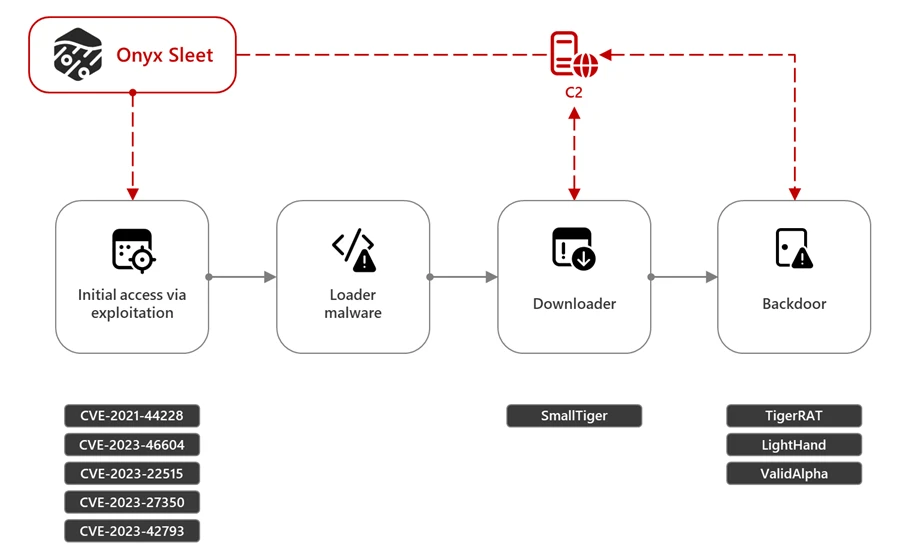
Onyx Sleet attack chain
A North Korean hacker has been indicted in the U.S. for allegedly using ransomware attacks on American hospitals to finance espionage activities against military and government targets. The hacker, Rim Jong Hyok, is accused of exploiting vulnerabilities in hospital systems to deploy ransomware and extort money, which was then channeled into state-sponsored cyber espionage campaigns.
The U.S. Department of Justice claims that Rim, operating under the Andariel hacking group (aka APT45, Nickel Hyatt, Onyx Sleet, Silent Chollima, Stonefly, and TDrop2) linked to North Korea’s military intelligence, targeted at least five hospitals, including one in Kansas where crucial medical imaging data was compromised. The stolen funds were then used to launch attacks on a wide range of U.S. federal agencies and defense contractors, seeking sensitive information related to missile technology, drones, and nuclear development.
The indictment reveals a concerning pattern of attacks aimed at both U.S. and international entities, including NASA, defense contractors in various countries, and even a Chinese energy company. These attacks reportedly compromised valuable military data, potentially giving North Korea access to sensitive information on anti-aircraft laser weapons.
U.S. authorities emphasize the symbiotic relationship between North Korea’s ransomware operations and its broader cyber espionage efforts. The ransom payments serve as a crucial funding source for the regime’s ongoing intelligence-gathering activities.
In response to these actions, the U.S. State Department has announced a $10 million reward for information leading to the identification or location of Rim Jong Hyok and the Andariel group. The Department of Justice has also confirmed the disruption of several accounts associated with North Korea’s cyber infrastructure, highlighting the importance of cooperation between victims and law enforcement agencies in combating such threats.
In a blog post, Microsoft revealed that they first encountered the activities of this hacker group in 2014. Experts caution that the group’s continuous enhancement of their tools and methods makes them particularly perilous. While the hackers previously relied heavily on spear-phishing tactics, they now increasingly exploit newly discovered software vulnerabilities. For instance, the group actively exploited a security flaw in the TeamCity platform last year.