
A newly discovered malware, dubbed “DocSwap,” is targeting mobile device users in South Korea, according to a report by S2W Threat Research and Intelligence Center Talon. The malware, disguised as a document-viewing authentication app, is suspected to be linked to a North Korean-backed Advanced Persistent Threat (APT) group.
The malicious application, initially signed on December 13, 2024, employs a sophisticated technique to conceal its true purpose. It decrypts the “security.db” file within the package using an XOR operation and dynamically loads a DEX file. This process involves modifications to the Loaded ApkPlugin open-source project, with an additional XOR operation added to the original code.
“This malware represents a previously unidentified type of threat, masquerading as a Document-viewing authentication app,” the report states.
Once installed, DocSwap exhibits a range of malicious behaviors. After loading the DEX file, the app ultimately performs information theft functions, such as keylogging through accessibility services, file transfers via socket communication, camera manipulation, and audio recording.
The malware also ensures persistence on the infected device. The “com.security.library.MainService” service is executed, using the StartForeground API to generate a notification and maintain persistence. The malware triggers the “com.security.library.MainService” service when boot-related intents occur, ensuring that the malware runs even after a phone reboot.
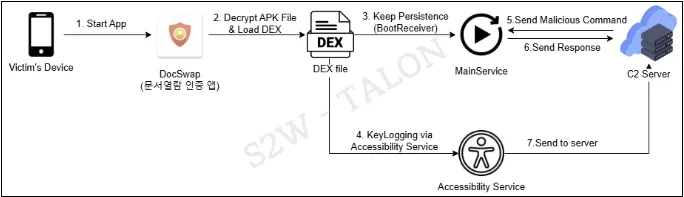
DocSwap establishes socket communication with a Command and Control (C2) server to receive instructions and exfiltrate data. The IP and port for socket communication are hardcoded, and a total of 57 malicious commands have been identified in the implementation. These commands enable a wide range of malicious activities, including:
-
Audio and camera recording
-
File manipulation
-
Information exfiltration (call logs, contacts, SMS messages, installed app information)
-
Device control (volume, Wi-Fi, Bluetooth)
-
Keylogging
-
Administrative actions (factory reset, lock screen control)
Attribution of the DocSwap malware has been linked to a North Korean APT group. When DocSwap malware was first discovered, a phishing page impersonating CoinSwap was identified on the C2 IP address used for socket communication. However, as of February 27, 2025, accessing the C2 address displayed Naver’s favicon and the message “Million OK !!!!“, indicating a possible connection to the Kimsuky group.
Related Posts:
- Malicious npm Packages Exploiting Typosquatting to Inject SSH Backdoors
- Malicious npm Packages Threaten Crypto Developers: Keylogging and Wallet Theft Revealed
- Expert: North Korean hackers harvest 11,000 Bitcoins in 2017
- Stealthy New Android Trojan Disguised as Popular Apps Steals Your Data
- Crafty Infostealer Campaign Leverages Fake Adobe Reader Installer, Advanced Tricks to Evade Detection