
Chain of events leading to compromise | Image: Group-IB
Lazarus Group, the infamous North Korean hacking collective, has continued its aggressive campaign in 2024, evolving its strategies and expanding its reach. According to a new report by Group-IB researchers, Lazarus is targeting job seekers and blockchain professionals through a malicious campaign called “Contagious Interview,” designed to infect victims with the BeaverTail malware and its notorious backdoor, InvisibleFerret.
The Contagious Interview campaign begins deceptively, with Lazarus posing as legitimate recruiters on job search platforms like LinkedIn, Upwork, and Moonlight. After initial contact, the attackers move the conversation to Telegram and request the victim to download what appears to be a Node.js project or a video conferencing app. Unbeknownst to the victim, the download contains BeaverTail, a powerful malware that can exfiltrate credentials, cryptocurrency wallet data, and browser information.
BeaverTail, first detected in November 2023, was initially a JavaScript-based malware targeting Windows systems. However, in 2024, Group-IB identified new versions of BeaverTail, including a native macOS variant and a Python version, showcasing Lazarus’ ability to adapt and improve its tools for different operating systems.
In mid-August 2024, researchers discovered a fraudulent video conferencing application named FCCCall, mimicking legitimate software to trick victims into installing malware. This application, developed using Qt6, a framework allowing cross-compilation across macOS and Windows, was found distributing BeaverTail. The app appears authentic by loading a legitimate URL, asking users for a meeting access code, all while malicious processes run covertly in the background.
Lazarus’ malicious efforts aren’t limited to job interviews. The group has also targeted gaming repositories on platforms like GitHub and GitLab. By injecting harmful JavaScript into game projects, particularly those built using Create React App or Create Next App, Lazarus continues to widen its net. Their updated tactics also include obfuscation techniques designed to hide malicious code in repositories, making detection by cybersecurity tools and researchers more challenging.
In addition, the group has expanded the scope of its attacks, now targeting a wide array of browser extensions, including password managers, cryptocurrency wallets, and even Microsoft Sticky Notes, stealing data from SQLite databases where sensitive user notes are stored.
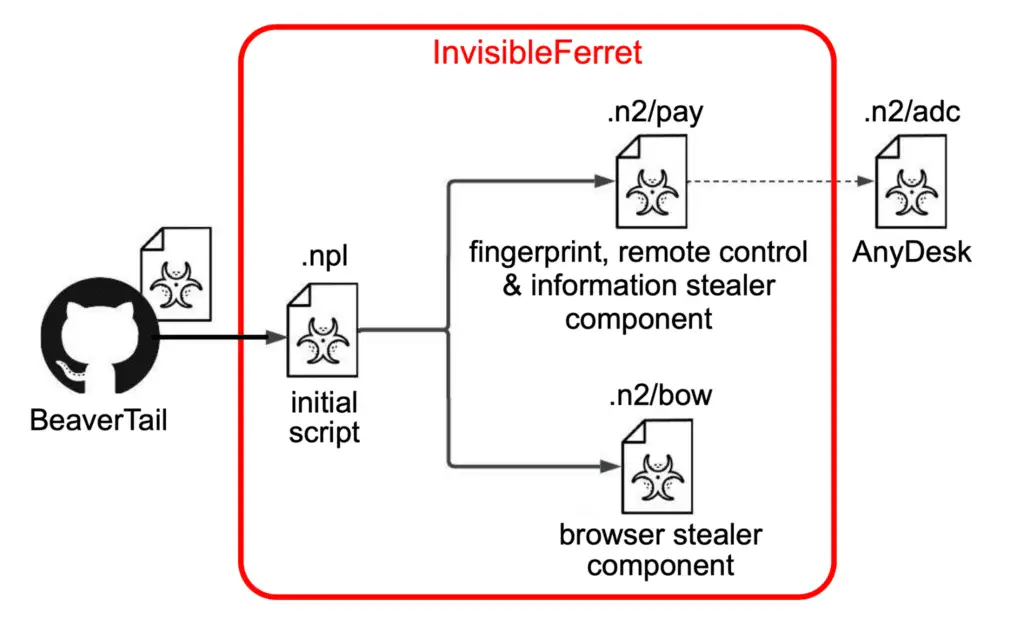
InvisibleFerret, a Python-based backdoor, continues to be a key part of Lazarus’ toolkit. With capabilities like remote control, keylogging, and data theft, it is frequently downloaded alongside BeaverTail. InvisibleFerret has also seen numerous updates in recent months, now employing more complex encryption methods to evade detection. The malware can now upload stolen data through both FTP servers and Telegram, further enhancing Lazarus’ exfiltration capabilities.
Related Posts:
- Temptation from Money: Lazarus APT extended to cryptocurrencies
- North Korea’s Lazarus Group: A Persistent Threat to the Defense Sector
- From Spear-Phishing to Zero-Day: Lazarus Group’s Latest Cyber Strategies
- Lazarus Hacking Group’s Malicious Python Packages Uncovered
- Lazarus Group Suspected in Telegram Phishing Attacks on Investors