
Jamf Threat Labs has uncovered a series of targeted attacks against individuals in the cryptocurrency industry, aligning with recent FBI warnings about North Korean cyber activity. The attacks employ sophisticated social engineering tactics, often initiated through professional networking platforms like LinkedIn, to trick victims into downloading malware.
One observed case involved a fake recruiter reaching out to a developer under the guise of offering a coding challenge. This challenge, delivered via a Visual Studio project, contained hidden malicious scripts designed to install a second-stage payload on the victim’s machine.
Attackers from DPRK have shown remarkable skill in using social engineering tactics, targeting individuals by impersonating recruiters or colleagues on professional networking sites. According to the FBI, these actors conduct thorough research on their targets by reviewing social media profiles, making their attempts more convincing.
One case studied by Jamf involved a fake LinkedIn profile, claiming to be from a decentralized finance (DeFi) tech company, used to contact a potential victim. This profile had zero followers—an immediate red flag—and used a polished but fake website to bolster its legitimacy. The attackers lured the target into downloading a malicious Visual Studio project that appeared to be a legitimate coding test.
In the observed attack, the malicious Visual Studio project asked the developer to convert Slack messages into CSV format—a seemingly innocent task. However, hidden within the project’s files were two malicious bash scripts that downloaded and executed additional malware, later identified as the “Thiefbucket” malware, known in some circles as “Rustdoor.” This payload allowed attackers to exfiltrate data and maintain persistent access to the compromised machine.
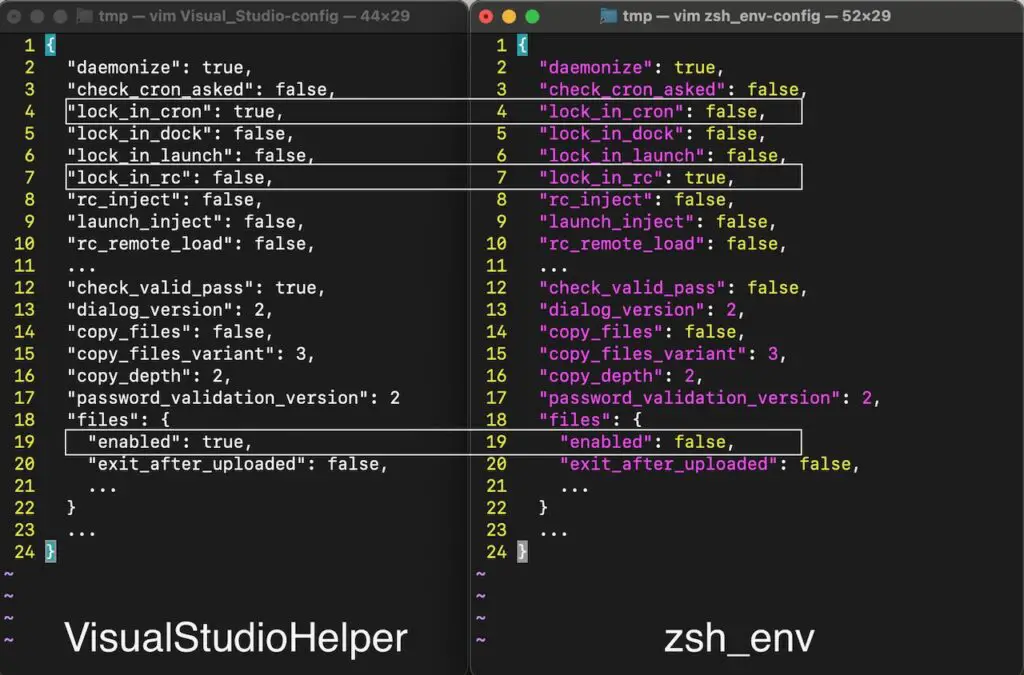
The two payloads, VisualStudioHelper and zsh_env, targeted developers by abusing cron jobs and the zshrc configuration file to establish persistence. The first payload, VisualStudioHelper, operated as an infostealer, while zsh_env acted as a backdoor. Both scripts were designed to execute malicious commands and connect to command-and-control (C2) servers, further indicating that the attack was part of a broader, coordinated effort by DPRK-affiliated actors.
Thiefbucket, the malware used in these attacks, has been evolving since its original discovery. Jamf Threat Labs reports that it continues to automate the theft of sensitive files, upload and download data, execute commands, and maintain persistence on compromised machines. The malware’s creators have even re-written portions of its code, transitioning from Rust to Objective-C, making it more suited to attack macOS environments.
The VisualStudioHelper payload goes beyond simple backdoor functions by prompting the user for credentials during the execution of a “fake” Visual Studio setup. This tactic is designed to steal user passwords by mimicking legitimate software behavior, taking advantage of the victim’s trust during the coding exercise.
As attackers continue to refine their tactics, organizations and individuals must stay informed and adapt their defenses accordingly. By prioritizing cybersecurity awareness and implementing robust security practices, the industry can better protect itself against the persistent threat of cyberattacks.
Related Posts:
- Sergey Tokarev: Ukrainian Startups Can Get Aid from Tech Circle
- Jamf Threat Labs Uncovers a Stealthy Malware Strain from BlueNoroff APT
- The Hidden Threat in Pirated macOS Applications: Unveiling a New Malware Campaign