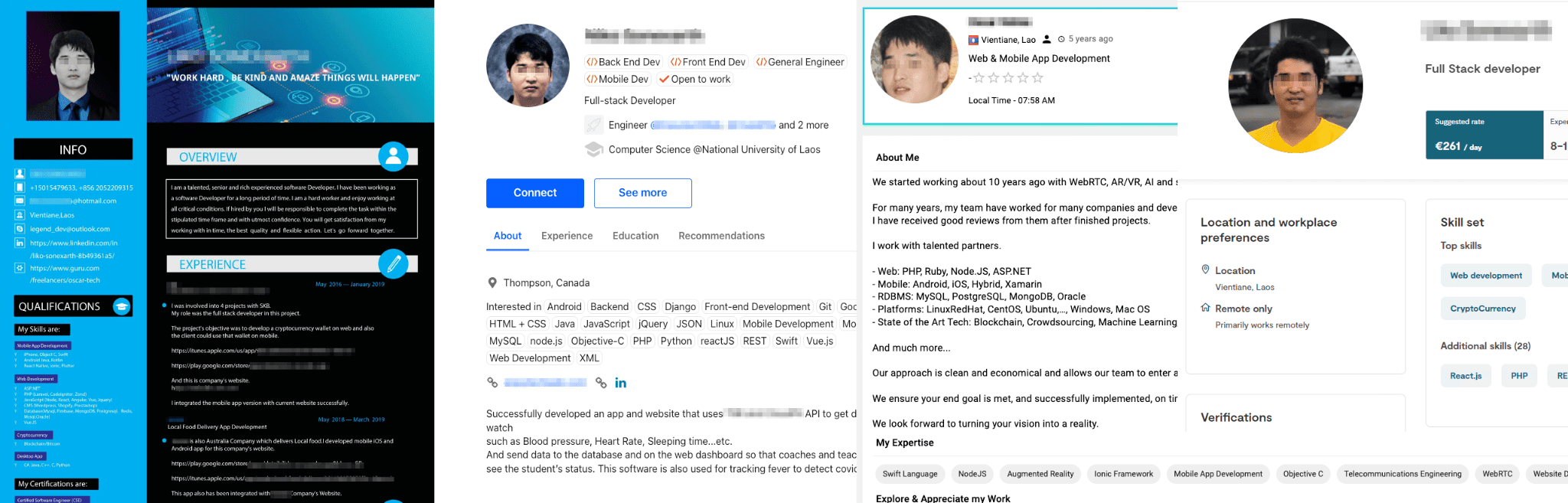
Fake resumes created by CL-STA-0237 | Image: Unit 42
A recent report by Unit 42 researchers uncovers a complex phishing campaign linked to a cluster of North Korean IT workers tracked as CL-STA-0237. This group used malware-infected video conference apps to target job seekers globally, exposing an evolution of cyber tactics. Unit 42’s findings reveal links between these IT workers and North Korea’s broader network of cyber operations, supporting illicit activities like weapons development.
The campaign, dubbed the “Contagious Interview Campaign”, initially targeted JavaScript developers using npm packages. However, the latest iteration employs fake video conferencing apps, such as MiroTalk and FreeConference, as malware delivery mechanisms. Unit 42 explains, “This method allows attackers to target a broader range of job seekers, rather than only those with npm JavaScript development expertise and specific machine configurations”.
Victims are lured into downloading conference call installers embedded with BeaverTail malware, which subsequently deploys the InvisibleFerret RAT. These tools provide attackers with extensive remote access capabilities, enabling data theft, system compromise, and further intrusion.
Unit 42 identified the CL-STA-0237 cluster as a key player in this campaign, using fake resumes to infiltrate companies. These IT workers often impersonate freelance developers, leveraging stolen identities to secure remote positions. Fake resumes created by CL-STA-0237 feature headshots that appear to be the same individual with slight variations, suggesting their dual role in fraudulent job applications and malware distribution.
The group’s operations appear to be based in Laos, with evidence pointing to physical presence. Headshot images from fake resumes were traced to a shopping mall in Vientiane, further corroborating their activities in the region.
The report connects CL-STA-0237 to North Korea’s extensive cyber campaigns, including the Wagemole Campaign, which exploits remote IT jobs for espionage and financial gain. Unit 42 observed a disturbing trend: North Korean IT workers “have begun transitioning into more aggressive roles, including participating in insider threats and malware attacks”.
These activities generate significant revenue to fund North Korea’s ballistic missile and weapons programs. Ethereum wallet transactions associated with the Wagemole Campaign were traced to Sang Man Kim, a North Korean financier sanctioned by the U.S. Treasury for supporting illicit state operations.
As Unit 42 concludes, “Despite numerous reports, media coverage and law enforcement efforts, these campaigns have not diminished. We anticipate that North Korean job-related campaigns will likely persist and even escalate.”
To counter such sophisticated threats, Unit 42 advises organizations to:
- Strengthen Hiring Practices: Conduct thorough background checks to identify fake resumes and stolen identities.
- Monitor for Insider Threats: Implement robust detection tools to identify unusual employee behavior.
- Scrutinize Outsourced Services: Evaluate the security practices of third-party service providers.
- Segregate Work and Personal Devices: Ensure employees do not use corporate systems for personal tasks.
Related Posts:
- LockBit Ransomware: The Hidden Threat in Resume Word Files
- Researchers Uncover Sophisticated Phishing Campaigns Leveraging Cloudflare Workers