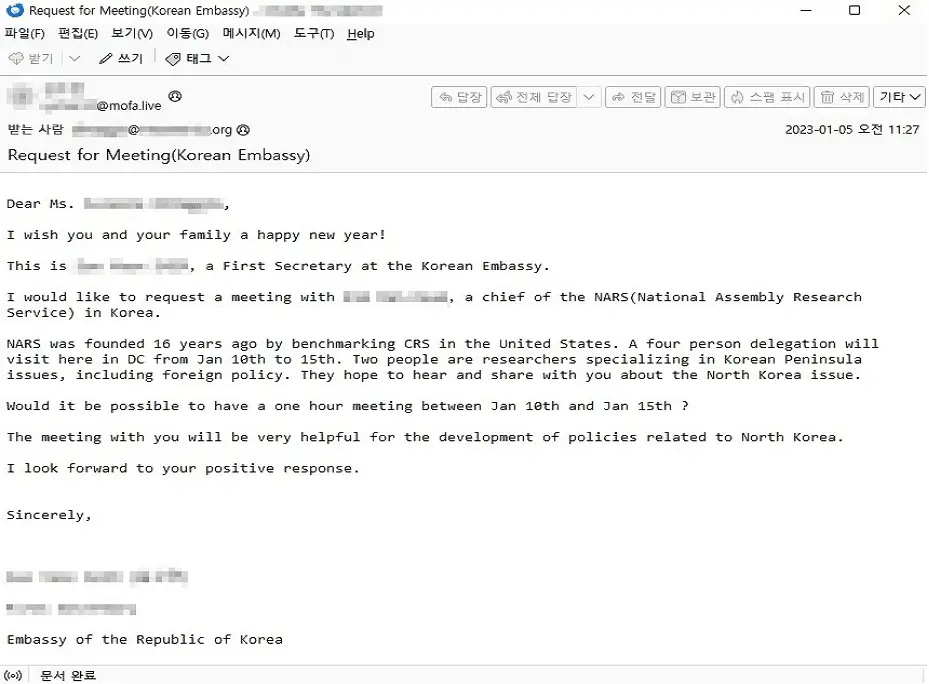
Phishing Email
The North Korean hacking organization, Kimsuky, has unleashed a sophisticated spearphishing campaign, targeting hundreds of influential individuals globally. This alarming development, as reported by security firm Hauri Inc., demands an immediate and vigilant response.
Between January and October 2023, the Kimsuky hacking organization deftly maneuvered 16 email servers and 24 counterfeit accounts, launching over 400 spearphishing emails. These meticulously crafted messages were not just sent randomly; they were strategically aimed at high-profile individuals in various countries, including research institutions and universities. Remarkably, one in four recipients opened these emails and even replied, unwittingly exposing themselves to potential malware infection.
What’s most concerning is the precision with which these attacks were executed. Kimsuky’s strategy involved tailoring replies to fit the victim’s profile, making interactions seem natural and trustworthy before deploying malicious software. This approach represents a significant evolution in spearphishing tactics, signaling a shift from traditional methods to more calculated, personalized attacks.
The spearphishing emails encompassed a range of subjects, from New Year greetings to requests for professional opinions, cleverly disguised as benign communications. These initial “decoy” emails, upon garnering the recipients’ attention, were followed by responses embedded with malware. The meticulousness extended to not pursuing recipients further if no reply was received, or sending follow-up emails to nudge the opening of the initial message.
The phishing accounts’ data revealed an alarming 25% response rate to these emails. The exact number of those infected by the malware remains unknown, but the risk of system infection for those who replied is significantly high.

The range of methods employed to distribute the malware is diverse, including Korean (.hwp) and document files (.doc, .docx), cloud service downloads (Google, Microsoft), Windows disk image files (.iso), malicious script files (.vbs), and HTML files. These were often sent with compression passwords to avoid detection by mail security solutions.
The malware used in these attacks is designed to be undetectable by certain antivirus programs, checking for their presence before deciding whether to activate. This sophisticated evasion technique underscores the need for updated and comprehensive cybersecurity measures.
Hauri Inc.’s Security Response Center warns that these spearphishing emails represent a significant departure from past malware distribution methods. The natural and meticulous nature of these communications makes them even more dangerous. As we move into 2024, it is expected that APT attack groups will continue to send spearphishing emails in various forms, necessitating heightened caution in email usage.