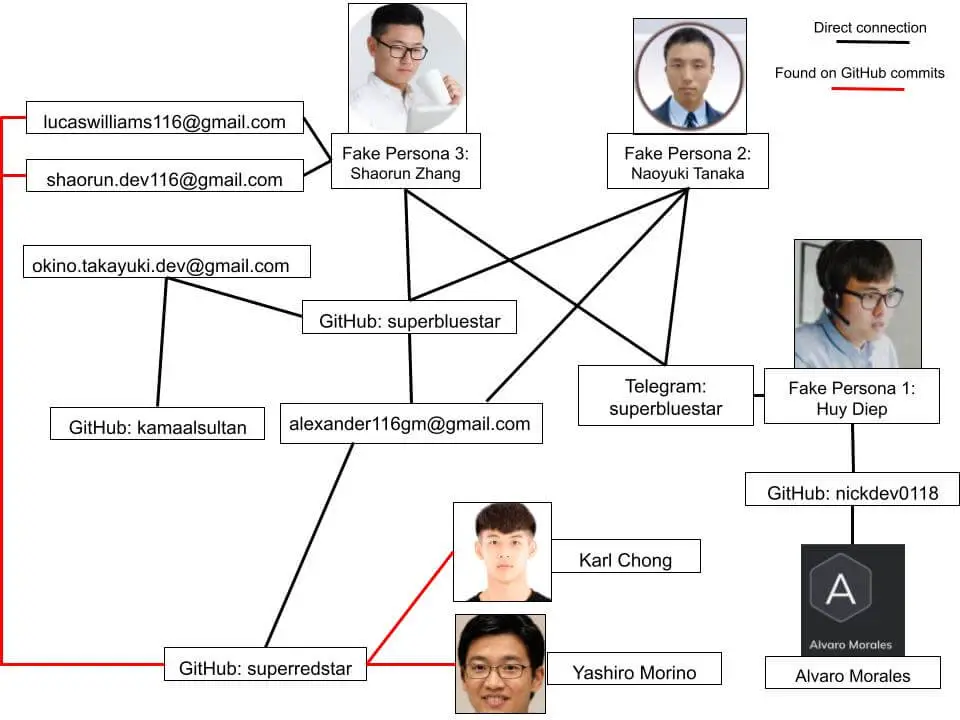
Network map of likely DPRK-affiliated personas
Cybersecurity analysts at Nisos have uncovered a North Korean (DPRK) employment fraud network using fake personas on GitHub to obtain remote IT jobs at companies in Japan and the United States. The fraudulent operation appears to be a financial scheme aimed at funding Pyongyang’s ballistic missile and nuclear weapons programs.
Nisos researchers identified multiple fake developer profiles posing as Vietnamese, Japanese, and Singaporean nationals. These profiles, crafted to appear as experienced full-stack and blockchain developers, leveraged matured GitHub accounts to backstop their false identities.
According to the report: “The network appears to be using GitHub to create new personas and is reusing matured GitHub accounts and portfolio content from older personas to backstop their new personas.”
These fake developer profiles aimed to secure employment at small to mid-sized tech firms by showcasing fabricated credentials and manipulated digital photos
Nisos has identified at least three individuals who have successfully gained employment using these tactics:
Huy Diep (HuiGia Diep)
- Employed at Tenpct Inc., Japan since September 2023.
- Profile features digitally altered photos to give the illusion of working in an office setting.
- Associated with GitHub account nickdev0118, which co-authored commits with a previously flagged DPRK-linked persona.
Naoyuki Tanaka
- Claimed employment at New York-based Enver Studio as a full-stack and blockchain engineer since November 2021.
- Linked to GitHub account superbluestar.
- Listed on multiple freelance job platforms, including Upwork and Himalayas, with inconsistent employment details.
Shaorun Zhang
- Listed experience as a freelancer and blockchain developer.
- Digital photo analysis revealed head pasted onto an advertisement image.
- Shared GitHub repositories with other known fraudulent DPRK personas.
To maintain credibility, DPRK-affiliated IT workers employ several deception techniques:
- Manipulated profile photos using stock images and face-pasting techniques.
- Backstopping fake personas by reusing older GitHub accounts to create an illusion of experience.
- Using identical email structures containing 116 and ‘dev’ to link multiple personas.
- Minimal social media presence, making detection harder for recruiters.
“Several indicators suggest that the network is likely DPRK-affiliated. These indicators are consistent with tactics, techniques, and procedures (TTPs) attributed to DPRK employment fraud actors,” Nisos reports.
Nisos researchers believe these fraudulent employment schemes are part of a state-sponsored effort to infiltrate tech firms globally. The ultimate goal is financial gain, with salaries from unsuspecting employers potentially funding North Korea’s weapons programs.
Related Posts:
- North Korea’s Job Scam: IT Specialists Fabricate Identities to Work for Western Firms
- Researchers Uncovers Sophisticated Phishing Campaigns Leveraging Cloudflare Workers
- North Korean APT Group Kimsuky Targets Japanese Organizations with Stealthy Malware Campaign
- SEO Poisoning: Unmasking the Malware Networks Behind Fake E-Commerce