Image: Lookout Threat Lab
A new Android surveillance tool, dubbed KoSpy, has been discovered by Lookout Threat Lab researchers, with evidence suggesting a targeted campaign against Korean and English-speaking users. The spyware is attributed with medium confidence to the North Korean advanced persistent threat (APT) group ScarCruft, also known as APT37.
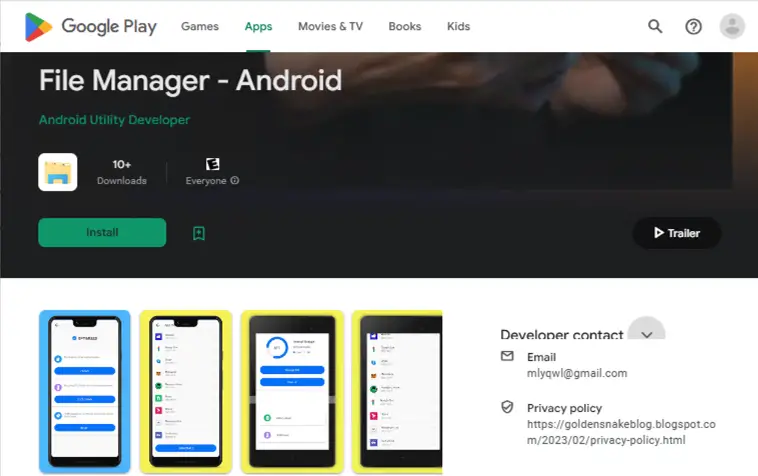
The KoSpy spyware family is relatively new, with early samples dating back to March 2022 and the most recent samples acquired in March 2024. Researchers at Lookout observed KoSpy samples masquerading as various utility applications, including “File Manager,” “Software Update Utility,” and “Kakao Security,” to deceive users into installing the malware.
KoSpy employs a two-staged command and control (C2) management approach, providing threat actors with flexibility and resilience. After initial infection, KoSpy retrieves a simple configuration from Firebase Firestore, an encrypted configuration containing an “on/off” switch and the C2 server address. This allows attackers to enable or disable the spyware and change C2 addresses at any time.
The spyware also incorporates anti-analysis techniques. KoSpy ensures the device is not an emulator and that the current date is past a hardcoded activation date. “This activation date check ensures that the spyware does not reveal its malicious intent prematurely,” the report states.
KoSpy is designed to collect an extensive amount of sensitive information from victim devices. With the help of dynamically loaded plugins, KoSpy’s capabilities include:
-
Collecting SMS messages
-
Collecting call logs
-
Retrieving device location
-
Accessing files and folders on local storage
-
Recording audio and taking photos with the cameras
-
Capturing screenshots or recording the screen while in use
-
Recording keystrokes by abusing accessibility services
-
Collecting Wi-Fi network details
-
Compiling a list of installed applications
The collected data is encrypted with a hardcoded AES key before being sent to the C2 servers.
Lookout researchers attribute the KoSpy activity to the ScarCruft APT group with medium confidence. ScarCruft is a North Korean state-sponsored cyber espionage group active since 2012, primarily targeting South Korea but also conducting operations in various other countries.
The report highlights connections between KoSpy and previous malicious activities attributed to North Korean threat groups APT43 and APT37. One of the C2 domains of KoSpy, st0746[.]net, resolves to an IP address that has been associated with many potentially malicious Korea-related domain names in the past.
While the apps mentioned in the report have been removed from Google Play and the associated Firebase projects have been deactivated by Google, users should remain vigilant. It is crucial to exercise caution when downloading apps from third-party sources and to verify app permissions before installation.
Related Posts:
- An Ongoing Social Engineering Campaign Targets 130+ US Organizations
- ScarCruft Strikes: North Korea’s Cyber Espionage Against Media and Experts Unveiled
- North Korean APT-C-28 Expands Cyber Espionage Campaign
- New Agent Tesla Spyware Variant was spread via Microsoft Word documents
- How Spyware Evades Detection through Advanced Obfuscation