
Components of InvisibleFerret Source: Unit 42
Palo Alto Networks Unit 42 researchers have uncovered a new wave of attacks in the ongoing Contagious Interview campaign, where North Korean threat actors are posing as recruiters to target job seekers in the tech industry. The campaign, which was first reported in November 2023, has now evolved with updated malware variants—BeaverTail and InvisibleFerret—that pose a significant threat to both individuals and organizations in the tech sector.
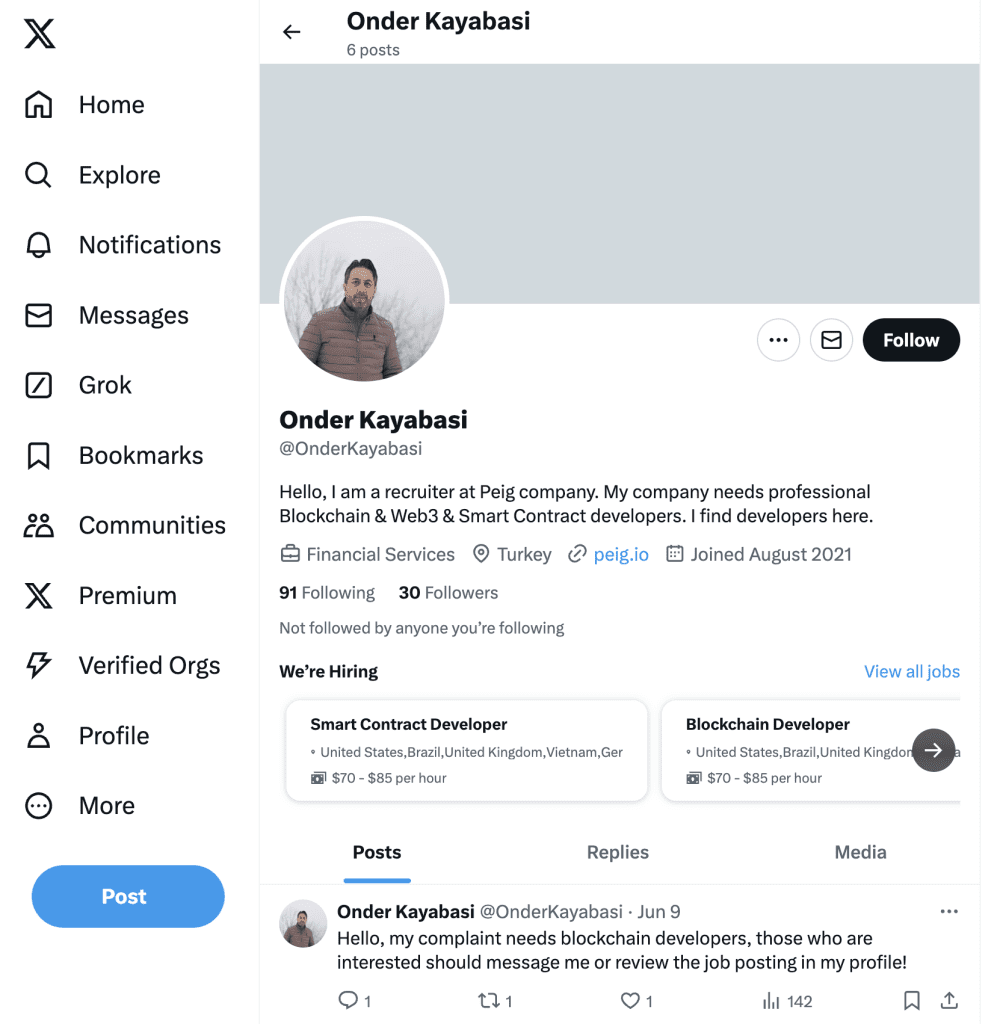
The attackers behind this campaign have developed an intricate method to engage victims by pretending to be recruiters on job search platforms like LinkedIn. According to Unit 42’s findings, the threat actors set up fake technical interviews, convincing victims to download and install malware masquerading as job-related tools. A prominent example involved a recruiter alias, Onder Kayabasi, which remained active on social media platforms well into 2024.
Once victims download and install the malware, it connects to the attacker’s command and control (C2) server, allowing the threat actor to gain remote access to the infected device. This remote access not only compromises the victim’s personal data but also opens the door to wider corporate espionage, especially if the infected device is company-owned.
The BeaverTail malware, a downloader and infostealer, is a critical part of the Contagious Interview campaign. Unit 42 reports that the new variant of BeaverTail, first seen in July 2024, was developed using the Qt framework, enabling it to target both Windows and macOS platforms from the same source code. This new version of BeaverTail has undergone significant updates, including the ability to steal browser passwords and cryptocurrency wallets across both operating systems.
The malware is cleverly disguised as applications like MiroTalk (a video conferencing tool) and FreeConference. Once installed, it appears as a normal application to the victim, but in the background, it exfiltrates sensitive data such as browser credentials and cryptocurrency wallet information. “This newer Qt version of BeaverTail targets 13 different cryptocurrency wallet browser extensions, compared to only nine wallets previously targeted by the JavaScript variant,” the report notes. Among the wallets targeted are MetaMask, Coinbase, and Binance.
Once BeaverTail has established a foothold on the victim’s system, it proceeds to download and execute the InvisibleFerret backdoor. Written in Python, InvisibleFerret provides the attackers with powerful capabilities, including keylogging, remote control of the infected device, and exfiltration of sensitive files. “InvisibleFerret is capable of fingerprinting the infected endpoint and can even download additional software like AnyDesk for further remote control,” Unit 42 highlights.
In this campaign, InvisibleFerret has undergone several code modifications, making it more efficient and harder to detect. For instance, its latest update includes improvements in file searching algorithms on both Windows and macOS, allowing it to locate and exfiltrate specific data faster than before.
The Contagious Interview campaign appears to be financially motivated, as the malware is specifically designed to steal cryptocurrency wallets and other valuable digital assets. North Korean threat actors are known for conducting financially-driven cybercrimes to support the country’s regime. “This campaign may be financially motivated, since the BeaverTail malware has the capability of stealing 13 different cryptocurrency wallets,” the report emphasizes.
To mitigate the risk, individuals and organizations are encouraged to exercise caution when engaging with online recruiters, particularly those requesting downloads during job interviews. Employers should also ensure that endpoint detection and response (EDR) tools are in place to identify and block such threats before they can cause damage.
Related Posts:
- North Korean Hackers Launch Job Interview Scam to Deploy BeaverTail and InvisibleFerret Malware
- Threat Group TA4557 Exploits Recruiters for Malware Delivery