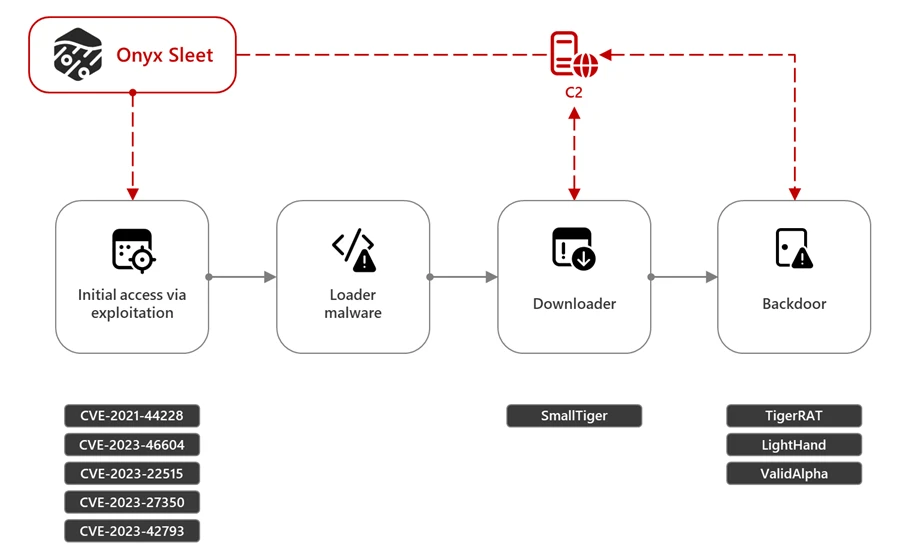
Onyx Sleet attack chain
Unit 42, the threat intelligence team at Palo Alto Networks, has uncovered a disturbing new trend in the cybercrime landscape: North Korean state-sponsored hackers are collaborating with ransomware gangs. In a recent report, they detail how Jumpy Pisces, a group linked to the Reconnaissance General Bureau of the Korean People’s Army, played a key role in a Play ransomware attack.
Historically known for cyberespionage and financial crime, Jumpy Pisces—also referred to as Andariel or Onyx Sleet—has now turned its attention to ransomware. According to Unit 42, “This change marks the first observed instance of the group using existing ransomware infrastructure,” suggesting Jumpy Pisces could be functioning as an Initial Access Broker (IAB) or even an affiliate of Play ransomware, also known as Fiddling Scorpius. Unit 42 adds, “This shift in their tactics, techniques and procedures (TTPs) signals deeper involvement in the broader ransomware threat landscape.”
The investigation began after a Play ransomware incident in early September, but traces of unauthorized access by Jumpy Pisces date back to May 2024. The attack lifecycle highlights a slow and methodical intrusion, where Unit 42 observed, “a compromised user account accessed a particular host through a firewall device.” Using this foothold, Jumpy Pisces spread malware such as Sliver and DTrack across the network via Server Message Block (SMB) protocol.
Jumpy Pisces maintained persistence within the network, with activity peaking sporadically. Interestingly, the attackers used customized versions of open-source tools. Sliver, an alternative to the well-known Cobalt Strike, was repurposed by Jumpy Pisces to communicate with a command-and-control (C2) server at IP address 172.96.137[.]224, which remained active until the day prior to the ransomware deployment.
In early September, another unidentified threat actor accessed the network using the same compromised account. Unit 42 notes, “pre-ransomware activities including credential harvesting, privilege escalation and the uninstallation of EDR sensors” set the stage for the deployment of Play ransomware. This methodical escalation underscores a sophisticated approach that ensured EDR solutions were incapacitated before executing the ransomware.
The tools employed by Jumpy Pisces demonstrate a blend of custom development and modified public tools, a hallmark of advanced persistent threat (APT) groups. These include:
- DTrack: Previously linked to North Korean cyber operations, this infostealer disguises collected data as GIF files, adding a layer of obfuscation.
- Mimikatz: A modified version of this credential dumping tool was observed, with logs stored in
C:\windows\temp\KB0722.log. - TokenPlayer and PsExec: These tools were used for Windows access token abuse and privilege escalation, with files strategically placed in
C:\Users\Public\Music, a known technique linked to Play ransomware, according to an Adlumin report cited by Unit 42.
All these tools were digitally signed with invalid certificates that allowed them to mimic legitimate software files, bypassing standard detection mechanisms.
As Unit 42 concludes, “This development could indicate a future trend where North Korean threat groups will increasingly participate in broader ransomware campaigns, potentially leading to more widespread and damaging attacks globally.”
Related Posts:
- North Korean Hackers Gleaming Pisces Poisoned Python Packages Target Linux & macOS
- KLogEXE & FPSpy Backdoor: Kimsuky’s Evolving Cyber Espionage Arsenal
- Group-IB and other security firms assisted Ukrainian police in taking down on DDoS criminal gangs
- Defend Your Cloud: 8220 Gang Targets Linux & Windows