In a concerning revelation, Microsoft has flagged two North Korean cyber threats, Diamond Sleet and Onyx Sleet, capitalizing on a vulnerability in the JetBrains TeamCity server since early October 2023. TeamCity, a popular continuous integration and deployment application, is crucial for many organizations involved in DevOps and software development.
The specific vulnerability under discussion, CVE-2023-42793, is a remote code execution flaw that affects numerous versions of the JetBrains TeamCity server. Historically, these North Korean actors, especially Diamond Sleet, have successfully penetrated software supply chains by gaining unauthorized access to build environments. The potential risk to impacted organizations is alarming. As a responsive measure, JetBrains has launched an update to combat this vulnerability, ensuring users still on older versions have a mitigation plan.
Distinctly, while exploiting the identical flaw, both threat actors deploy individual tools and techniques upon successful vulnerability exploitation. Microsoft’s analysis suggests that the actors could be capitalizing on this vulnerability more opportunistically, aiming at various servers. But, both are geared with malware, tools, and strategies that facilitate extended access to the victimized servers.
Diamond Sleet (also known as ZINC) leans towards espionage, network destruction, data theft, and monetary gains. Their primary targets include defense sectors, IT services, and media entities globally. Historically, they’ve been involved in attacks on security researchers, weaponizing open-source software, and even compromising German software supplies.
On the flip side, Onyx Sleet (or PLUTONIUM) zeroes in on defense and IT services, focusing on entities in South Korea, India, and the U.S. They possess a diverse toolkit, allowing them to maintain extended access discreetly, often exploiting N-day vulnerabilities for initial access.
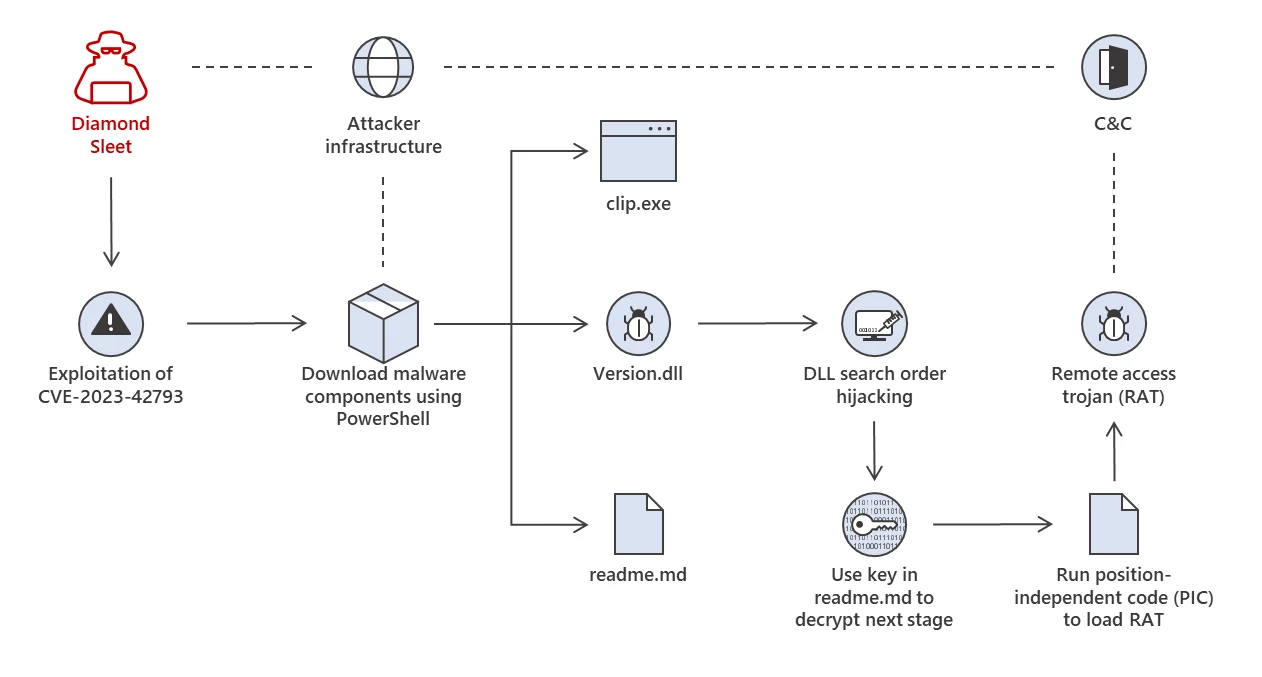
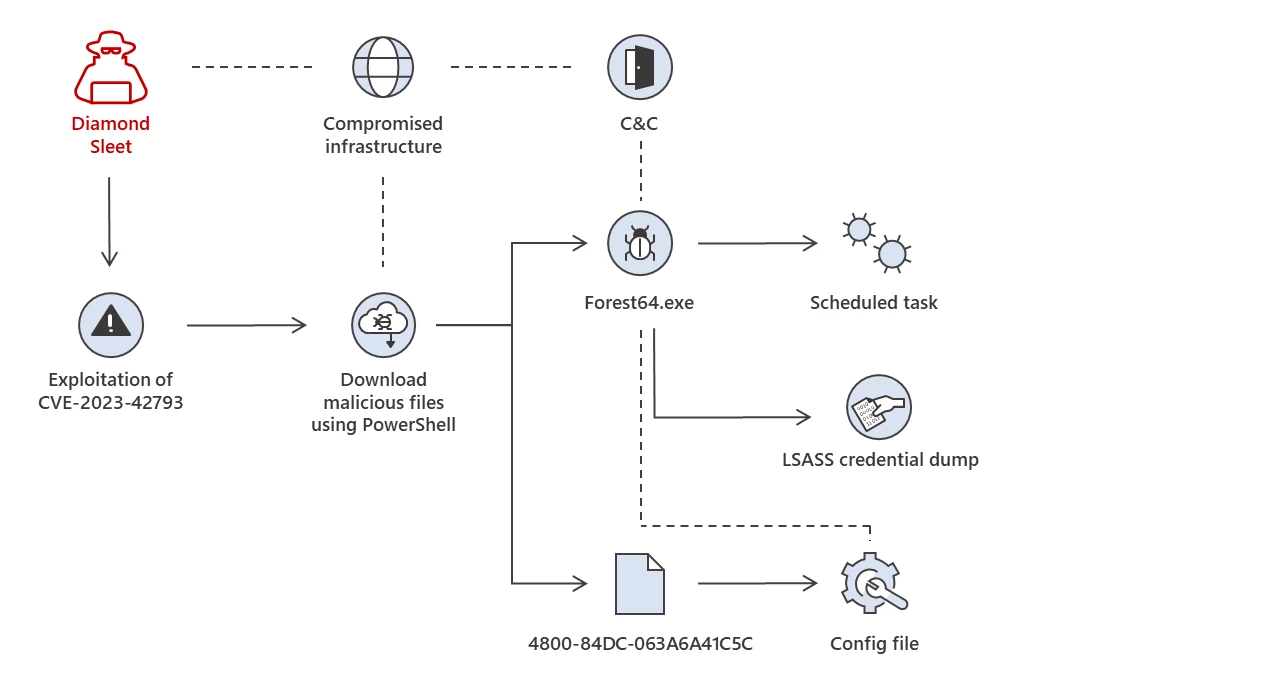
Diamond Sleet stands out with two primary attack paths. Firstly, they use the ‘ForestTiger’ backdoor. Post-compromise, they deploy PowerShell to fetch two payloads, notably Forest64.exe and 4800-84DC-063A6A41C5C, which become stored in the C:\ProgramData directory. These tools play crucial roles in their attack mechanism. In their second approach, they exploit DLL search-order hijacking, employing PowerShell to fetch a malicious DLL.

Onyx Sleet, however, follows a different trajectory. They create an imitation user account (krtbgt) resembling Windows’ legitimate KRBTGT account. They indulge in system discovery commands and deploy unique payloads fetched via PowerShell. This payload essentially acts as a proxy tool, forming a link between the victimized host and the control infrastructure of the attacker.
For organizations, this signifies the importance of robust cybersecurity strategies. Microsoft has been proactive in notifying compromised or targeted customers, offering essential information to bolster their defenses. Further, Microsoft Defender Antivirus recognizes and counters the malware and tools used by these threat actors.
In conclusion, the cyber realm’s complexity is ever-increasing, with nation-state actors becoming more sophisticated. Firms need to stay updated, vigilant, and proactive in their defense mechanisms, ensuring safety and operational continuity.