nShield: Anti-DDoS solution for VPS,Dedicated Servers and IoT devices
nShield
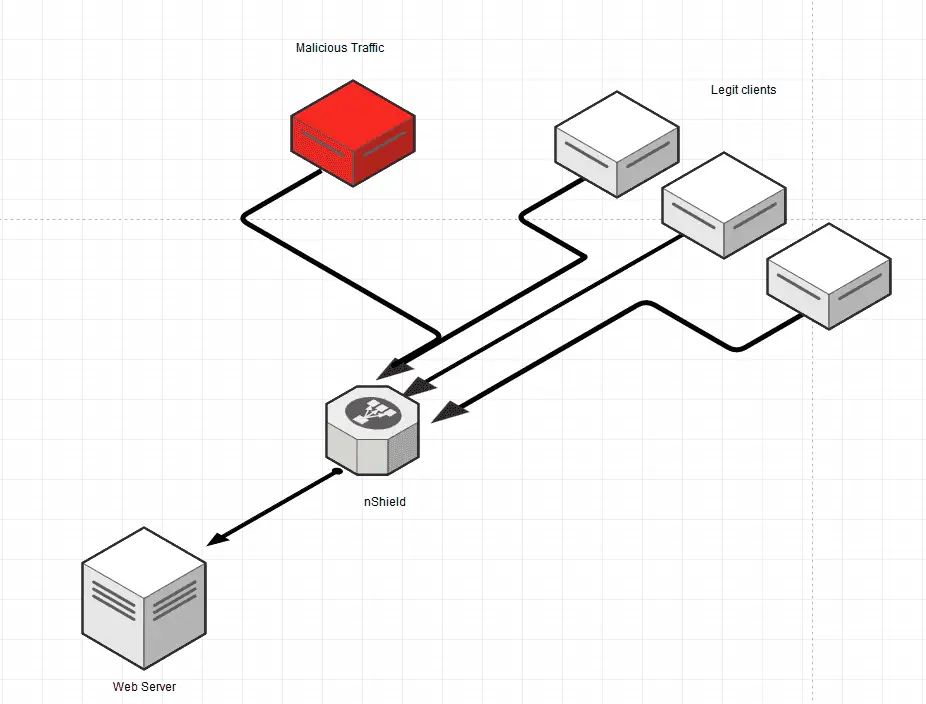
An Easy and Simple Anti-DDoS solution for VPS, Dedicated Servers and IoT devices based on iptables
How it works
Basically this python script is set by default to run every 30 minutes and check the config file to execute these operations:
- Get the latest Bot, Spammers, Bad IP/Net reputation lists and blocks if those Bad guys are attacking your server (Thank you FireHol http://iplists.firehol.org/ )
- Enables basic Anti-DDoS methods to deny unwanted/malicious traffic
- Rate limits when under attack
- Allows HTTP(S) Proxying to protect your site with an external proxy/server (You need to manually run SSL Verification first time)
Requirements
- Linux System with python, iptables
- Nginx (Will be installed automatically by install.sh)
Installation
Usage
The above quickstart/installation script will install python if not present and download all the repo with the example config files after that will be executed a bash script to set up some settings and a cron that will run every 30 minutes to check connections against common ipsets. You can find example config files under examples folder.
HTTPS Manually verification is executed with this command under the repository directory:
The python script after reading the config will prompt you to insert an email address (For Let’s Encrypt) and change your domain DNS to the nShield server for SSL DNS Challenge confirmation. Example:
Now your domain is verified and an SSL cert is issued to Nginx configuration and you can change your A record to this server.
Copyright (c) 2017 Sami
Source: https://github.com/fnzv/



