ntdsxtract: Active Directory forensic framework
ntdsxtract – Active Directory forensic framework
This framework was developed by the author in order to provide the community with a solution to extract forensically important information from the main database of Microsoft Active Directory (NTDS.DIT).
The modules are capable of extracting information from NTDS.DIT files obtained from the following Windows version:
- Windows Server 2003 (32 & 64 bit)
- Windows Server 2008 (32 & 64 bit)
The code is written in python and tested on the following platforms:
- MacOS
- Linux
The framework is capable of extracting information related to:
- user objects
- group objects
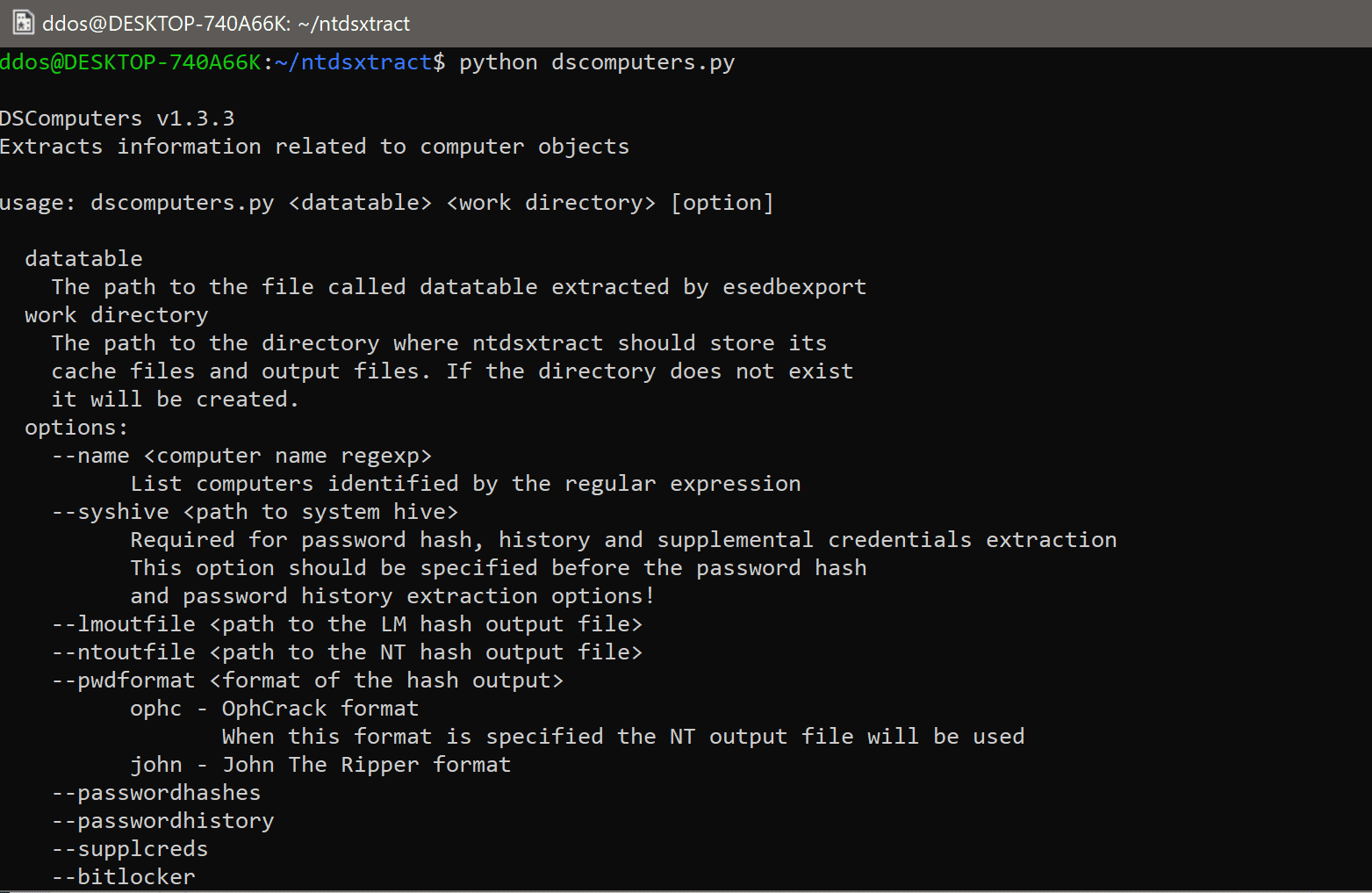
- computer objects
- deleted objects
Installation
git clone https://github.com/csababarta/ntdsxtract.git
python setup.py install
Usage

In order to utilize the framework, you should compile and install the library libesedb (see below). After that, you should run the esedbextract tool against the NTDS.DIT file and export all the tables. You can do that with the following command:
esedbexport ntds.dit
This command creates a folder in the current directory called ntds.dit.extract. Inside that folder, you will find the tables. You should use these tables as an input to the modules.
In order to extract password hashes and other encrypted data, you should obtain the registry from the same domain controller from which the NTDS.DIT file was extracted.
Copyright (C) 2014 csababarta
Source: https://github.com/csababarta/