Distribution via HuggingFace
A new threat actor group, NullBulge, has emerged with a captivating narrative: hacktivists fighting against AI’s encroachment on the art world. But beneath this veneer of activism lies a more complex reality, revealed by a recent report from SentinelLabs.
NullBulge presents itself as a hacktivist group with a noble cause—defending artists against the encroachment of AI. They promote their mission through a dedicated blog and occasional posts on 4chan, claiming their actions are a form of payback, targeting AI-related applications and games with malicious mods and extensions. However, the group’s extensive and well-coordinated campaigns hint at deeper, profit-driven motives.
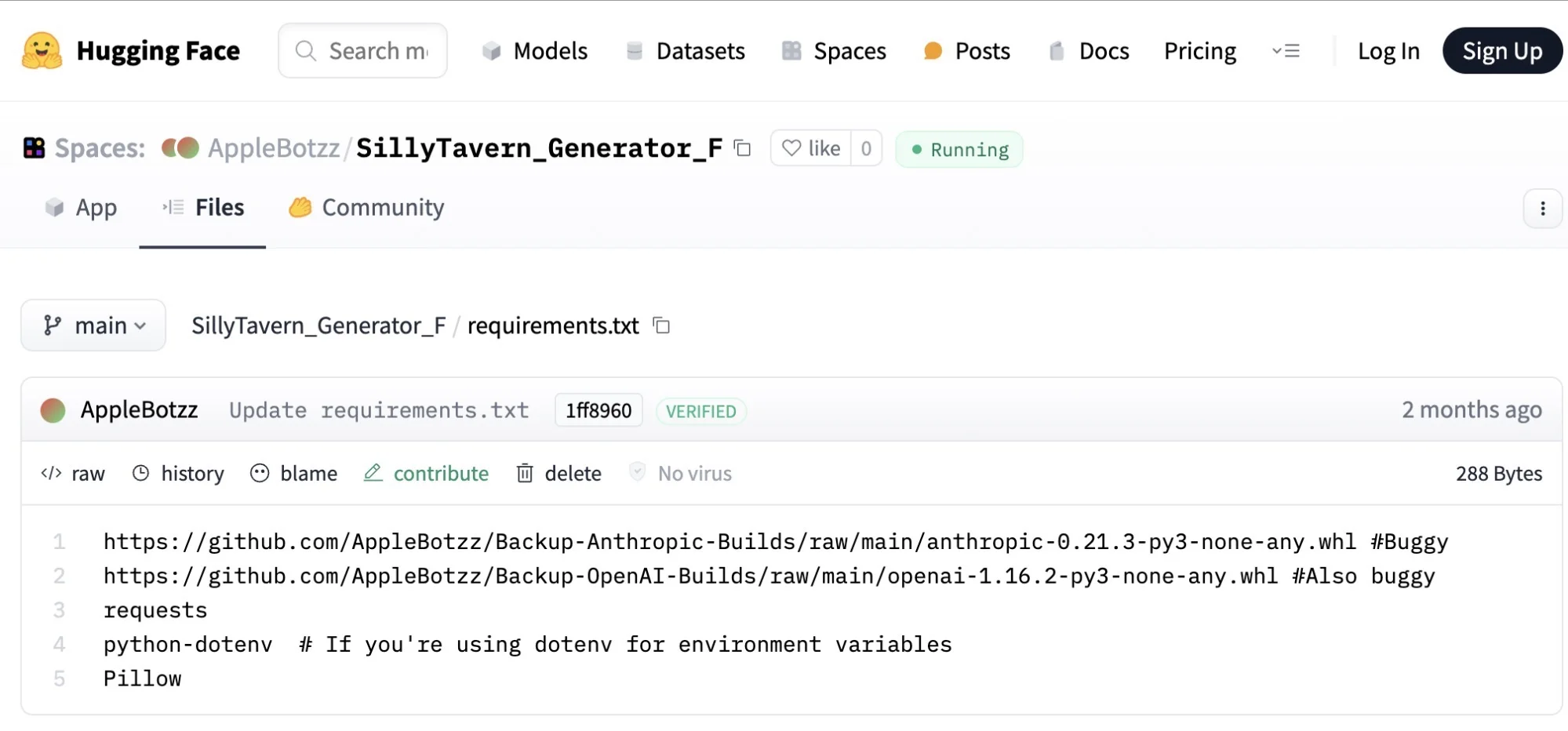
NullBulge employs a strategy known as “poisoning the well,” targeting the software supply chain by injecting malicious code into legitimate software distribution mechanisms. They exploit platforms like GitHub, Reddit, and Hugging Face, ensuring wide reach and substantial impact. Their primary tools include customized LockBit ransomware builds, Python-based payloads, and malicious mods, all designed to harvest and exfiltrate sensitive data.
Central to NullBulge’s operations is the AppleBotzz identity, used to host compromised repositories and spread malicious mods. Despite NullBulge’s claims that AppleBotzz is a separate entity, evidence suggests otherwise. The threat actors assert control over accounts previously managed by AppleBotzz, leveraging these platforms to distribute their payloads and extend their reach.
NullBulge’s attacks on BeamNG, a vehicle simulation game, underscore their versatility. By injecting obfuscated PowerShell into mod files, they distributed Async RAT or Xworm, leading to the deployment of customized LockBit payloads. These malicious mods were shared via encoded links on social media and forums, further amplifying their distribution.
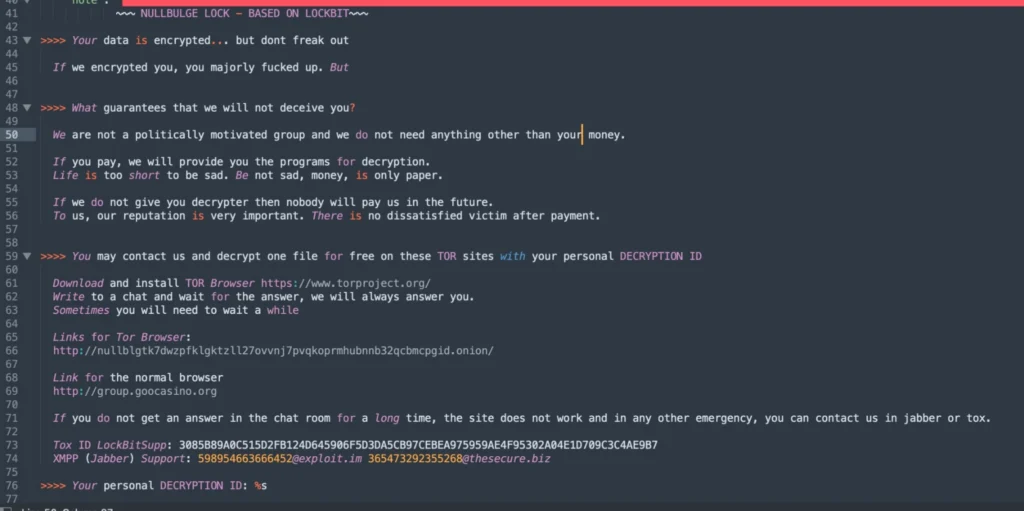
The use of LockBit ransomware by NullBulge signifies their capability to inflict severe damage. Built using the LockBit 3.0 builder, these payloads are configured to encrypt network shares, local volumes, and even send ransom notes to attached printers.
NullBulge operates multiple data leak sites, with domains such as nullbulge.com and nullbulge.se. They recently claimed to have leaked information from Disney, including .web publishing certificates and internal Slack data.
NullBulge maintains active profiles on underground forums, selling infostealer logs and stolen OpenAI API keys. Their GitHub repository, NullBulgeOfficial, contains libraries and tools for furthering their malicious activities. This diverse range of operations indicates a well-organized group with extensive resources.
NullBulge exemplifies the evolving threat landscape, where low-sophistication actors can inflict significant damage using readily available tools. Their focus on AI-centric applications and games highlights a vulnerable sector, ripe for exploitation.