Nvidia’s leaked code-signing certificate is used by hackers to sign malware
The South American hacker group is currently gradually releasing the confidential data stolen from NVIDIA, and the latest leak is the code signing certificate used by NVIDIA. The code signing certificate is used to sign the software to prevent it from being tampered with. If the software is tampered with, the signature will automatically become invalid and the verification cannot be continued. All kinds of software and drivers released by NVIDIA have dedicated digital signatures, which can be verified by Microsoft and provide security protection.
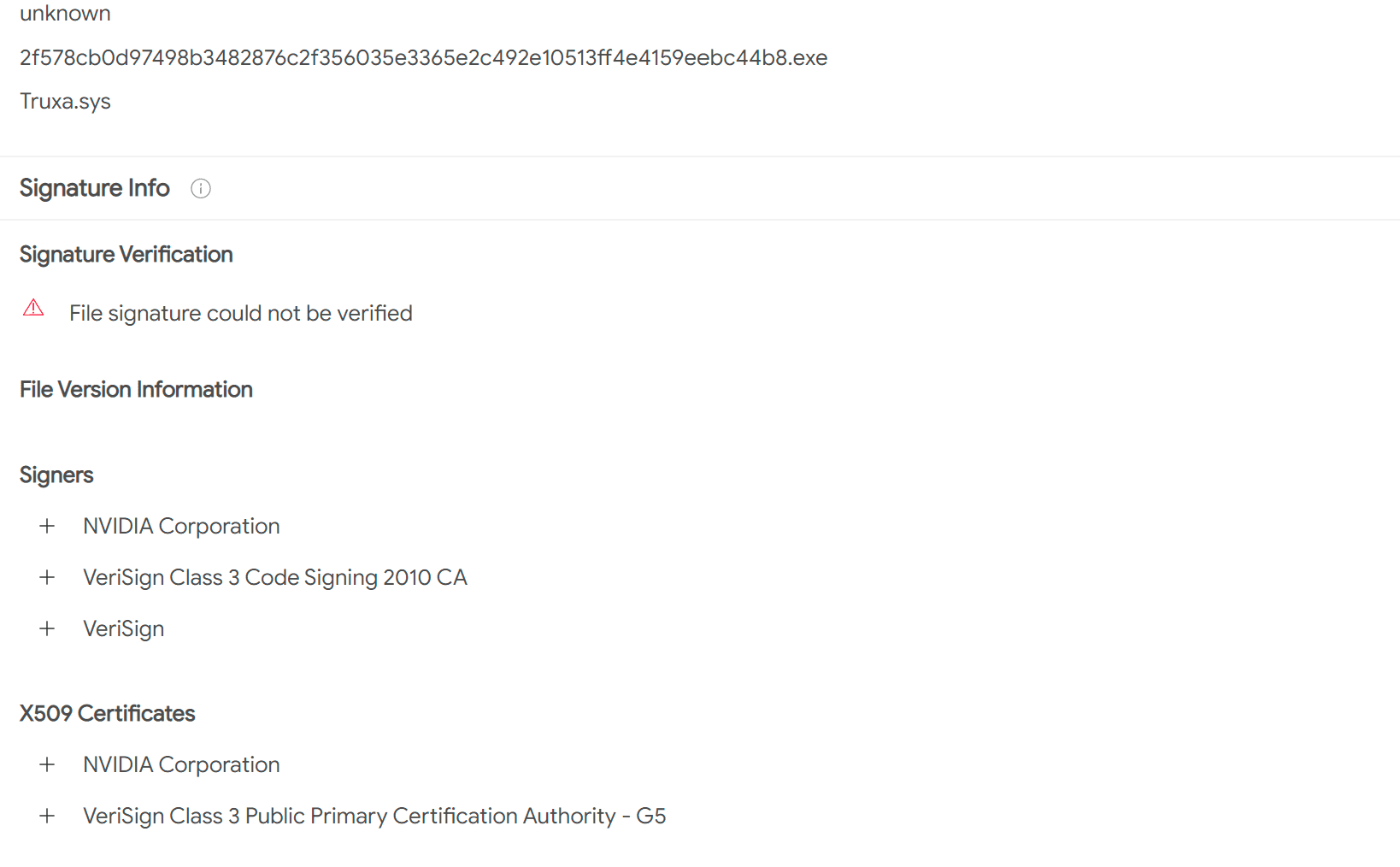
It has to be said that these hackers exploited various vulnerabilities very quickly. Only a few days after the code signing certificate was leaked, hackers began to use the certificate to sign malware. Of course, hackers are not using normal software to sign, and security researchers have found multiple pieces of malware that carry Nvidia’s code-signing certificate.
The classification statistics found that the software currently signed with NVIDIA’s code signing certificate includes malware, backdoors, remote access Trojans, and other types. Microsoft Defender won’t pop up a warning when users open the malware, and the UAC popup will display Nvidia’s company name. Therefore, it can be expected that a large number of malicious software will use NVIDIA signatures and pretend to be various crack software or activation tools to induce users to download and install.

Image: virustotal
Because it is a valid signature, it is very confusing, which may cause serious harm, and both Microsoft and NVIDIA are currently actively dealing with it.
It should be emphasized that although Microsoft Defender does not currently pop up a warning, it will kill the identified malware directly. There is a simpler and more convenient way to directly revoke the NVIDIA certificate. As long as it is revoked, these malwares will be directly blocked when the users try to open them. But for now, Microsoft can’t add Nvidia certificates to the revocation list, because once added, a lot of Nvidia’s existing software will be affected. So at present, we can only wait for NVIDIA to quickly deploy the new certificate and replace various software packages, and then apply for revocation of the digital signature after the replacement is completed.
At present, this problem is more difficult for Microsoft to deal with, mainly relying on Microsoft antivirus software to automatically identify and block signed malware. But Microsoft also provides a way for enterprise administrators to use application control policies to restrict enterprise users to downloading and installing only specific Nvidia drivers. However, this operation is more troublesome for individual users. Individual users can only maintain the status quo and do not download software of unknown origin. In addition, users must install and enable security software.





