Obfuscation Detection v2.0 releases: pinpoint obfuscated code
Obfuscation Detection
Automatically detect control-flow flattening and other state machines
Scripts and binaries to automatically detect control-flow flattening and other state machines in binaries.
Control-flow flattening is a code transformation that removes structure from a control-flow graph. As a result, the control flow cannot be easily recovered as before. For instance, consider the following graph:
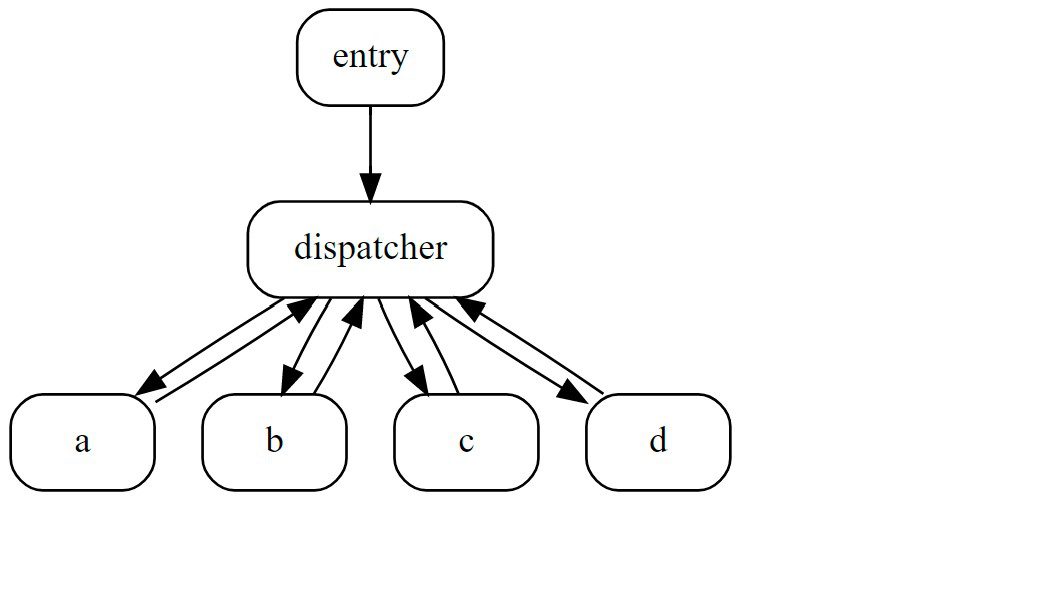
If we apply the same method to recover the control flow, we now only see that the blocks a, b, c and d are connected with a block labeled dispatcher. However, we do not know how these blocks relate to each other:
- Is block
avisited before or after blockb? - Is there any conditional branch?
- Is there any loop?
In other words, we do not get any meaningful information by looking only at the graph, since all blocks are on the same level; they are flattened.
In its most basic form, control-flow flattening has a central basic block—the dispatcher—that directs the control flow to the individual blocks. This is realized by a state variable that tracks which block will be visited next. The entry initially sets the state variable to the first basic block—in this case a; then, each block updates the state variable in correspondence to the underlying program logic. In other words, control-flow flattening can be considered as a state machine in which each basic block represents a single state.
Changelog v2.0
Major version update. Additional to code detection heuristics, this release introduces so-called Util functions, helpers which provide additional information to guide reverse engineering or pinpoint functions using a much narrower scope than heuristics. The first three Util functions are
- entry function detection: lists all functions which are not called from other functions
- leaf function detection: lists all function which do not call other functions
- entropy analysis: computes the entropy for each section and allows to identify packed/encrypted code
Download & Use
Copyright (C) 2021 Tim Blazytko