A new and more dangerous variant of the notorious Octo banking malware, dubbed “Octo2,” has been discovered by cybersecurity researchers at ThreatFabric. Octo2, an evolution of the ExobotCompact malware family, has already begun targeting European financial institutions, with attacks observed in countries such as Italy, Poland, Moldova, and Hungary. With enhanced remote access capabilities and sophisticated anti-detection techniques, Octo2 poses a significant risk to mobile banking users across the region.
Originally known as Exobot when it emerged in 2016, this malware family has evolved over the years to become one of the most widespread and dangerous mobile banking threats. Octo, its predecessor, was notorious for its ability to perform overlay attacks, intercept push notifications, and take over devices. Now, with the release of Octo2, the malware has become even more powerful, featuring improved remote access tools designed to facilitate full device takeover and perform fraudulent transactions without the user’s knowledge.
The malware developers have focused on increasing the stability of remote control sessions, even introducing a “low-quality” setting that allows attackers to maintain connections on poor networks. This allows Octo2 to carry out its attacks even under less-than-ideal conditions, ensuring consistent and reliable device access.
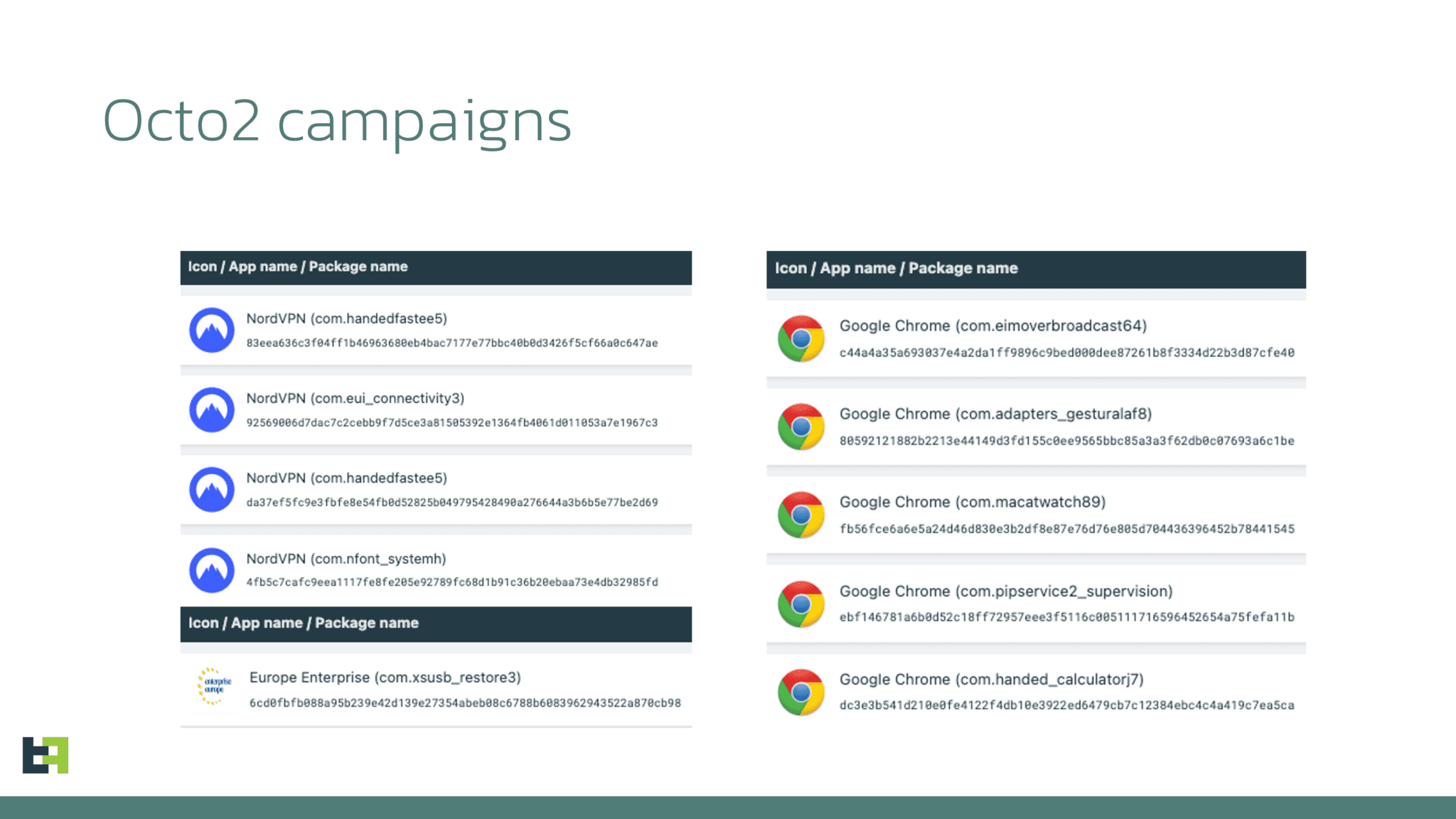
The first Octo2 campaigns, discovered by ThreatFabric in early 2024, masqueraded as legitimate apps such as Google Chrome, NordVPN, and Enterprise Europe Network. These fraudulent apps, once installed, deployed Zombinder, a tool that allows Octo2 to bypass Android 13+ security restrictions by disguising itself as a necessary plugin.
Once installed, Octo2 is capable of intercepting push notifications and concealing them from the victim, a technique that cybercriminals use to block important security alerts. The malware’s reach is not limited to Europe; Octo2 is expected to expand globally, with its operators targeting users in the U.S., Canada, Singapore, and other regions.
To evade detection, Octo2 incorporates a Domain Generation Algorithm (DGA) that dynamically generates command-and-control (C2) domain names, making it harder for security systems to block its operations. Additionally, the malware uses an innovative encryption method, generating a new cryptographic key for every communication with the C2 server, further complicating efforts to intercept and analyze its traffic.
Octo2’s obfuscation techniques are more advanced than previous versions, using multiple layers of encryption and dynamically loading additional malicious libraries to evade both manual and automated analysis by security researchers.
As Octo2 campaigns continue to spread, both mobile users and financial institutions are urged to stay alert. The malware’s ability to remain undetected while executing highly targeted attacks marks it as a serious threat in the world of cybercrime.
Related Posts:
- Hackers use three malware simultaneously in cyber espionage against Ukraine
- Threat Actors Exploit GitHub to Spread Malware, Targeting Multiple Operating Systems
- Two New Variants of the Spectre Vulnerability were found by Security researchers
- 32% Surge in US Mobile Fraud! Banking Malware Run Rampant as Market Booms