Download page | Image: K7 Labs
A new report from K7 Labs has uncovered a sophisticated Android banking Trojan campaign that uses the guise of a popular AI chatbot to deceive users. The malware, known as OctoV2, is being spread through deceptive websites that mimic the official Deepseek AI chatbot application.
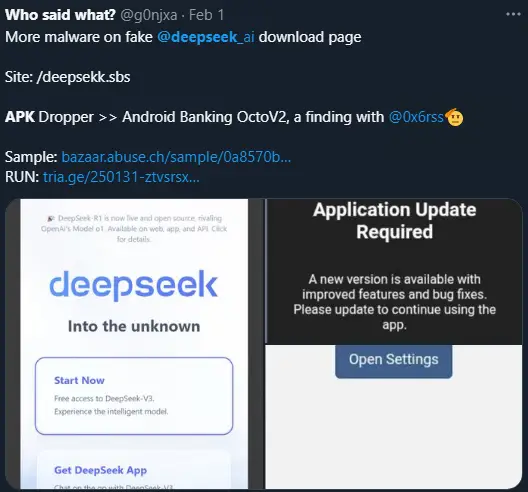
The malicious campaign begins with a phishing link, “hxxps://deepsekk[.] sbs”, which leads to a website that closely resembles the legitimate Deepseek AI interface. The report indicates that threat actors are creating these deceptive websites to trick users into downloading their malicious application.
Users who fall victim to the scam and attempt to download the Deepseek AI application are instead served with a malicious APK file named “DeepSeek.apk”. Once installed, the malware uses the genuine Deepseek icon in the device app drawer.
The malicious app then prompts users to enable the “Allow from this source” option and install an additional app. K7 Labs’ analysis revealed that two instances of the Deepseek malware are installed on the device, each with a different package name. The report refers to the packages as the “parent app” (com.hello.world) and the “child app” (com.vgsupervision_kit29).
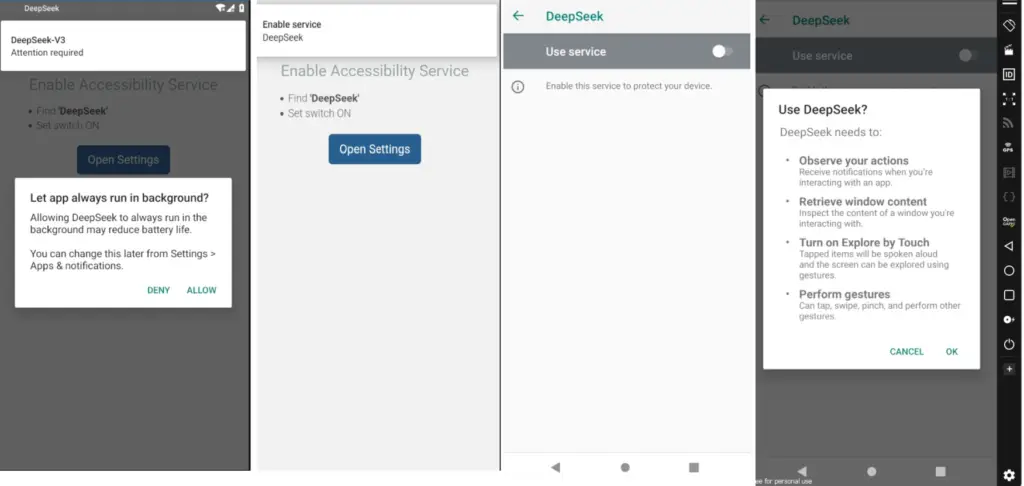
The child app frequently prompts the user to enable the Accessibility Service setting.
K7 Labs researchers faced challenges in analyzing the parent app due to its password protection. “This is unusual and we have been observing a rapid increase in the number of such password-protected malicious APK files in our zoo collection,” the report stated. Reversing tools like APKTool and Jadx also failed to parse the APK files. However, the Android SDK tool aapt was able to successfully parse the application.
Further analysis revealed that the parent app scans the app’s assets directory to locate a file with the “.cat” extension. The parent app then opens the “.cat” file, copies it into the “data/data/com.hello.world/cache/Verify.apk” folder, and uses the android method “PackageManager.getPackageArchiveInfo()” to check if it’s a valid APK. After verification, the app installs the child package.
The report also details the child app’s communication with its command and control (C2) server. The malware uses a Domain Generation Algorithm (DGA) to dynamically generate domain names for C2 communication, a technique used to evade domain blacklisting. The child app also scans and retrieves a list of all installed applications on the victim’s device and transmits this information to the C2 server.