OLE Object Offensive: FlowerPower APT’s Novel Attack Vector
In the ever-evolving landscape of cyber threats, a new formidable player has emerged: the FlowerPower APT campaign. This sophisticated cyber-attack scheme, identified by the Genians Security Center, demonstrates a new level of intricacy in the realm of Advanced Persistent Threats (APT).
The FlowerPower campaign ingeniously masquerades as interview requests from foreign news channels, leveraging the widely used Korean HWP (Hangul Word Processor) document format. This approach marks a strategic shift from previous attacks that predominantly used Microsoft Office DOC files. By embedding malicious Object Linking and Embedding (OLE) objects in these documents, the attackers have crafted a new method to infiltrate systems.

Image: Genians
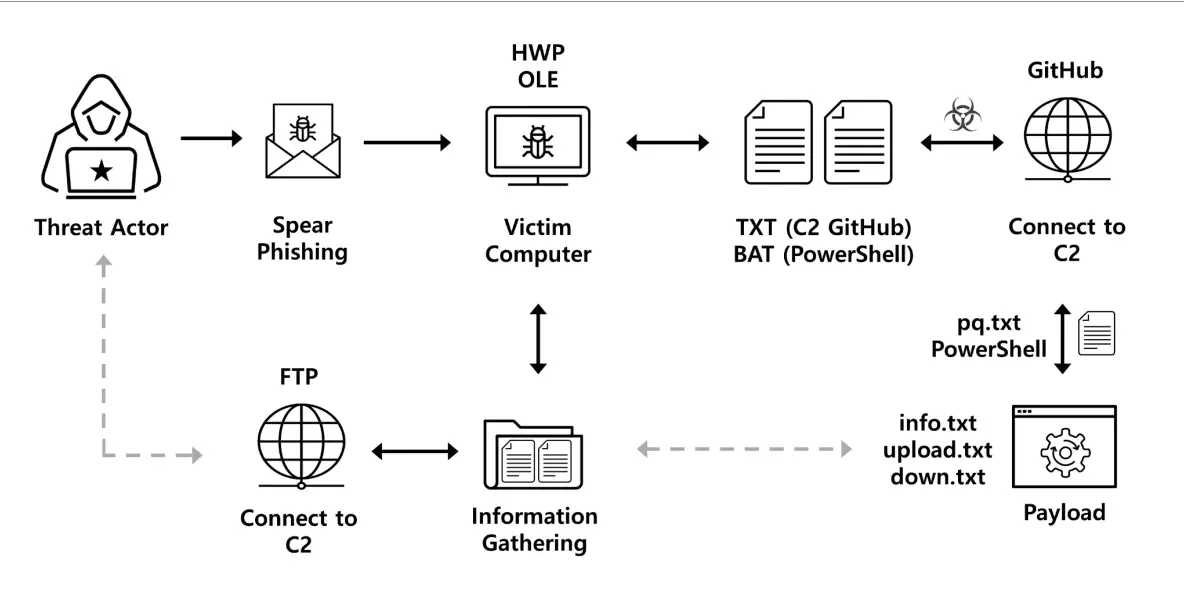
At the heart of the FlowerPower campaign lies a spear-phishing strategy. The attackers send emails posing as interview requests from legitimate news outlets, complete with HWP attachments named ‘CNA[Q].hwp’. These files are meticulously designed to bypass security detection, often requiring a password for access, which is only shared with the email recipient.
Once the victim opens the document and inputs the password, the hidden OLE objects within — named ‘zz.bat’ and ‘oz.txt’ — get activated. The ‘zz.bat’ file cleverly uses PowerShell commands to call upon the ‘oz.txt’ file, which in turn communicates with a specific GitHub repository. This repository acts as the Command and Control (C2) server, directing the attack further.
Utilizing GitHub as a C2 server is a masterstroke, showcasing the adaptability and innovation of the FlowerPower attackers. By storing additional malicious commands in different repositories, they have created a decentralized and hard-to-detect control system.
The implications of FlowerPower are far-reaching. The attack not only compromises the immediate security of the targeted systems but also opens doors for further exploitation and data exfiltration. By establishing persistence through methods like startup folder manipulation and additional file downloads, the campaign ensures a prolonged presence within the infected systems.
Countering this sophisticated attack requires an equally advanced response. Tools like Genian EDR (Endpoint Detection and Response) are crucial in detecting and mitigating such threats. These solutions provide real-time monitoring and analysis of suspicious activities, helping to intercept the attack at various stages.
FlowerPower is more than just a cyber attack; it’s a wake-up call for organizations globally. The use of commonly trusted document formats and reputable platforms like GitHub signifies a shift in APT strategies, emphasizing the need for heightened awareness and advanced security measures.
The FlowerPower APT campaign stands as a testament to the evolving sophistication of cyber threats. Its intricate use of HWP files, OLE objects, and GitHub as a C2 server marks a significant advancement in APT methodologies. As cyber adversaries continue to innovate, so must our strategies to detect, analyze, and counteract these threats. The FlowerPower campaign is not just another entry in the annals of cyber warfare — it is a clear signal that the battleground is shifting, and we must adapt swiftly.