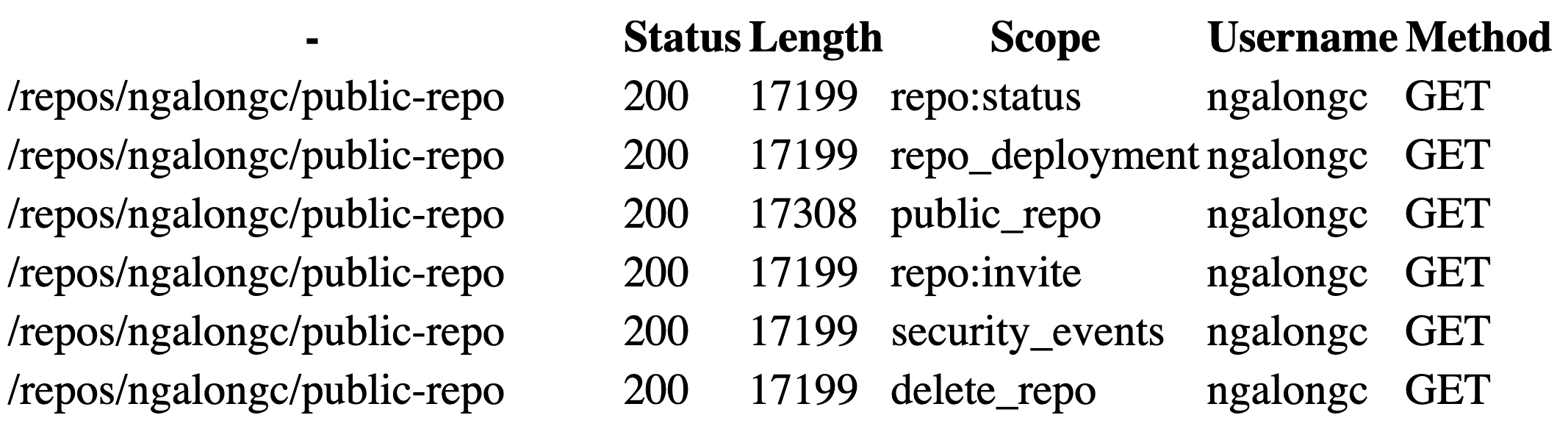
Screenshot of the scanning result in artifacts
OpenAPI Security Scanner
Authorization security issues in modern web applications could not be easily picked up by security scanners. A few examples from Shopify, LINE, NordVPN. One of the reasons is that the security scanners mainly look for SQLi, XSS, RCE instead of looking for authorization security bugs, and the scanners usually do not have knowledge of how the web application is supposed to behave. That’s why the majority of the authorization bugs now are mainly discovered manually. OpenAPI Security Scanner is created to help to discover authorization security issues with both automation and manual review. It behaves like an external unit test tool to make sure everything is behaving the way it should be.
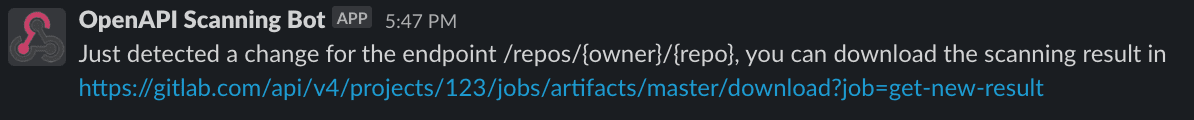
The workflow to use this scanner would look something like this:
- Prepare the OpenAPI yaml file of the targeted API
- Define the targeted endpoints and variables to be used for the API testing
- Generate multiple sets of credentials from different users to make sure a variety of edge cases are covered while performing the API tests
- After the configuration, start the runner and the scanning result could be found in the artifacts
- Schedule the runner to run periodically and customize the way you want to receive the notifications whenever there’s a change in the scanning result
Advantages
For developers, using this tool would add an extra layer of assurance that the API is behaving as expected both internally and externally. And the scanner could be triggered upon every code deployment by triggering the pipeline https://docs.gitlab.com/ee/ci/triggers/.
For bug bounty hunters, using this tool can ensure you can always stay on top of the targeted API, because we all know, even a specific endpoint wasn’t vulnerable before, it could be vulnerable in the future because of various reasons. So it’s easier to have the manual part of bug hunting to be automated using this tool.

Install & Use
Copyright 2021 Ron Chan