opencve v1.5 releases: CVE Alerting Platform
OpenCVE
OpenCVE (formerly known as Saucs) is a platform that alerts you about new vulnerabilities related to the CVE list.
How does it work
OpenCVE uses the JSON feed provided by the NVD to be synchronized.
After an initial import, a background task is regularly executed to check changes in the list. If a new CVE is added, or if a change is detected, the subscribers of the related vendors and products will be alerted.
For now, the only method of notification is the mail, but we plan to add other integrations (webhooks, Slack, Jira, PagerDuty, OpsGenie…).
Feature
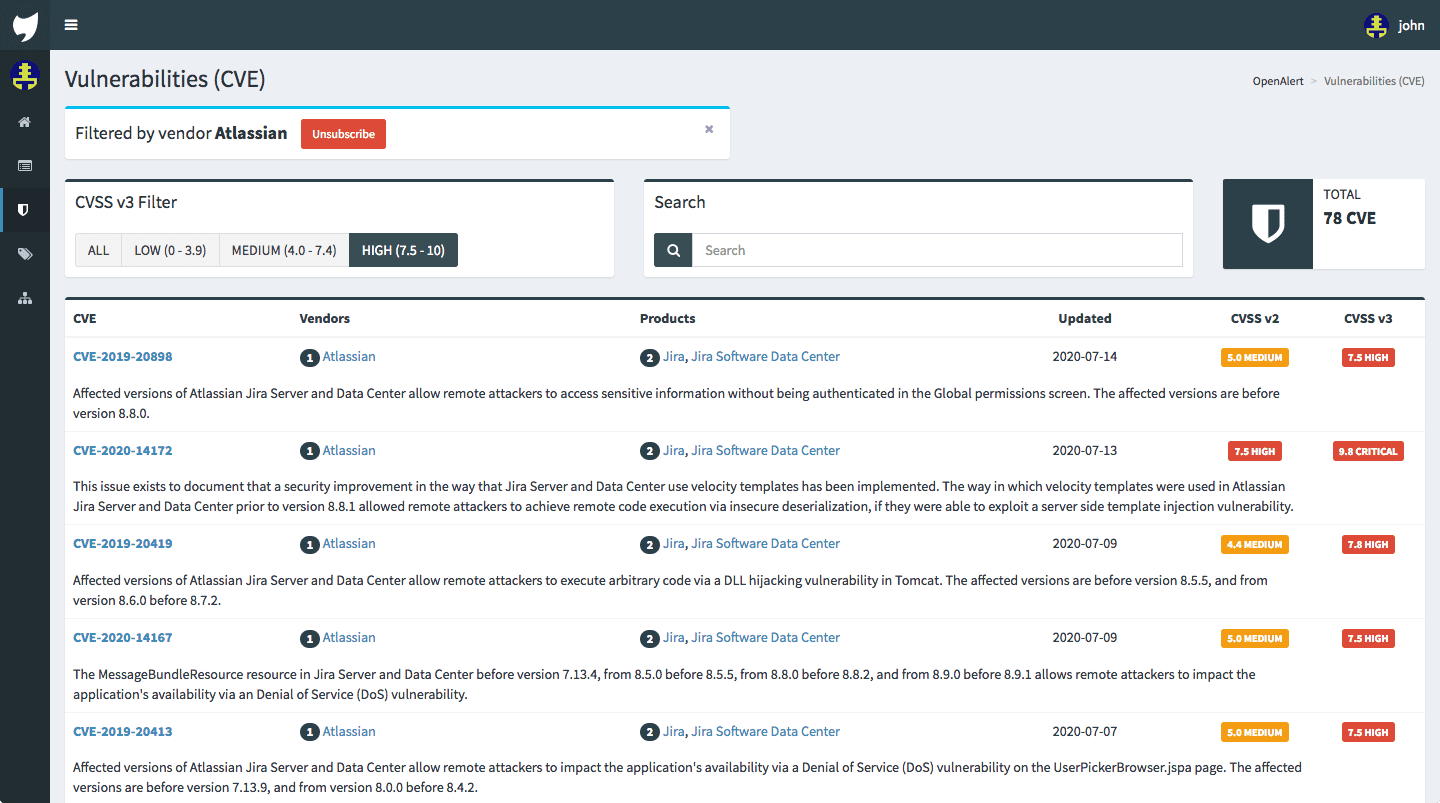
Explore the list of CVE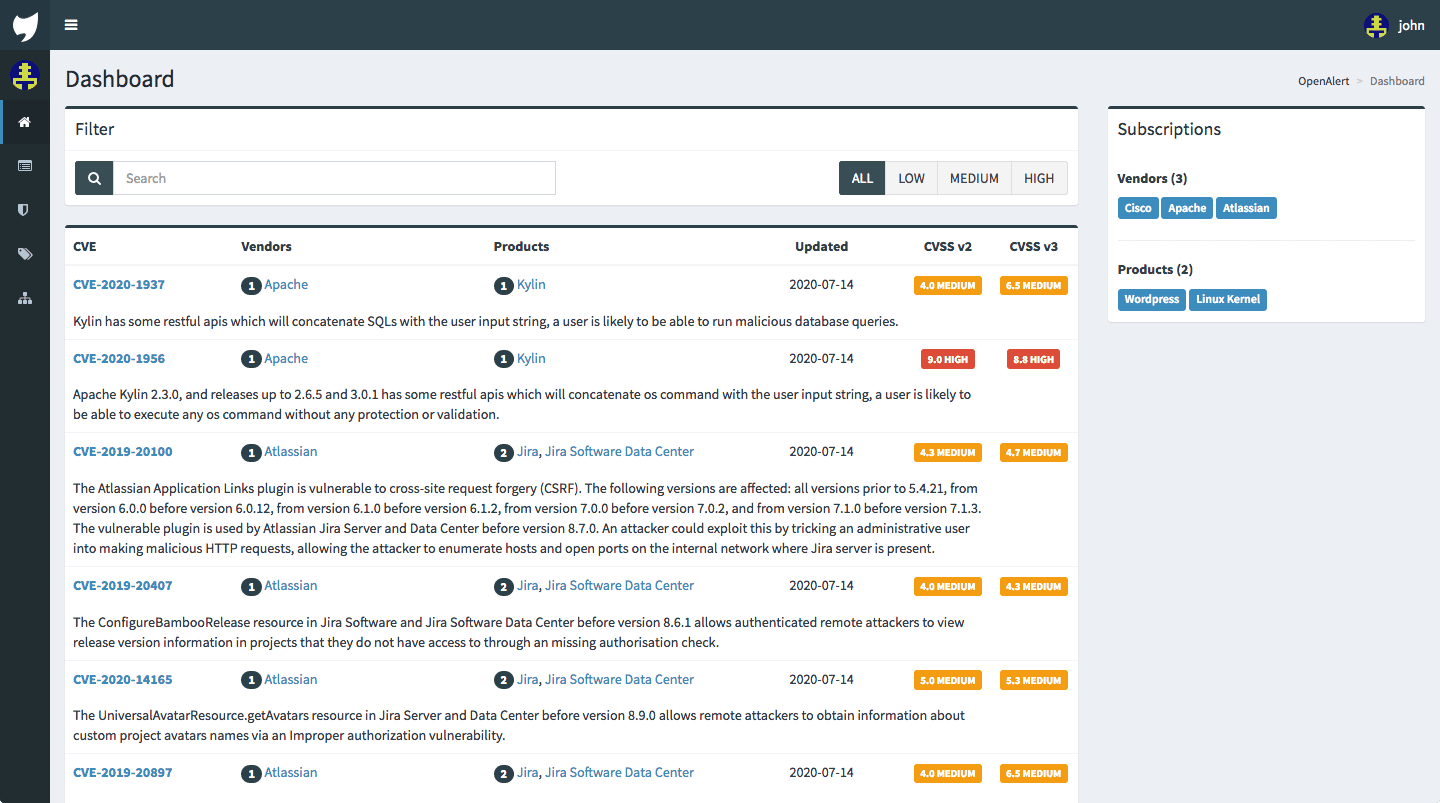
OpenCVE lets you search the CVE you want to be filtered by the vendor, product, CVSS, or CWE.
Because security is our main concern as well, everything is done to ease access to vulnerability warnings and let you know first.
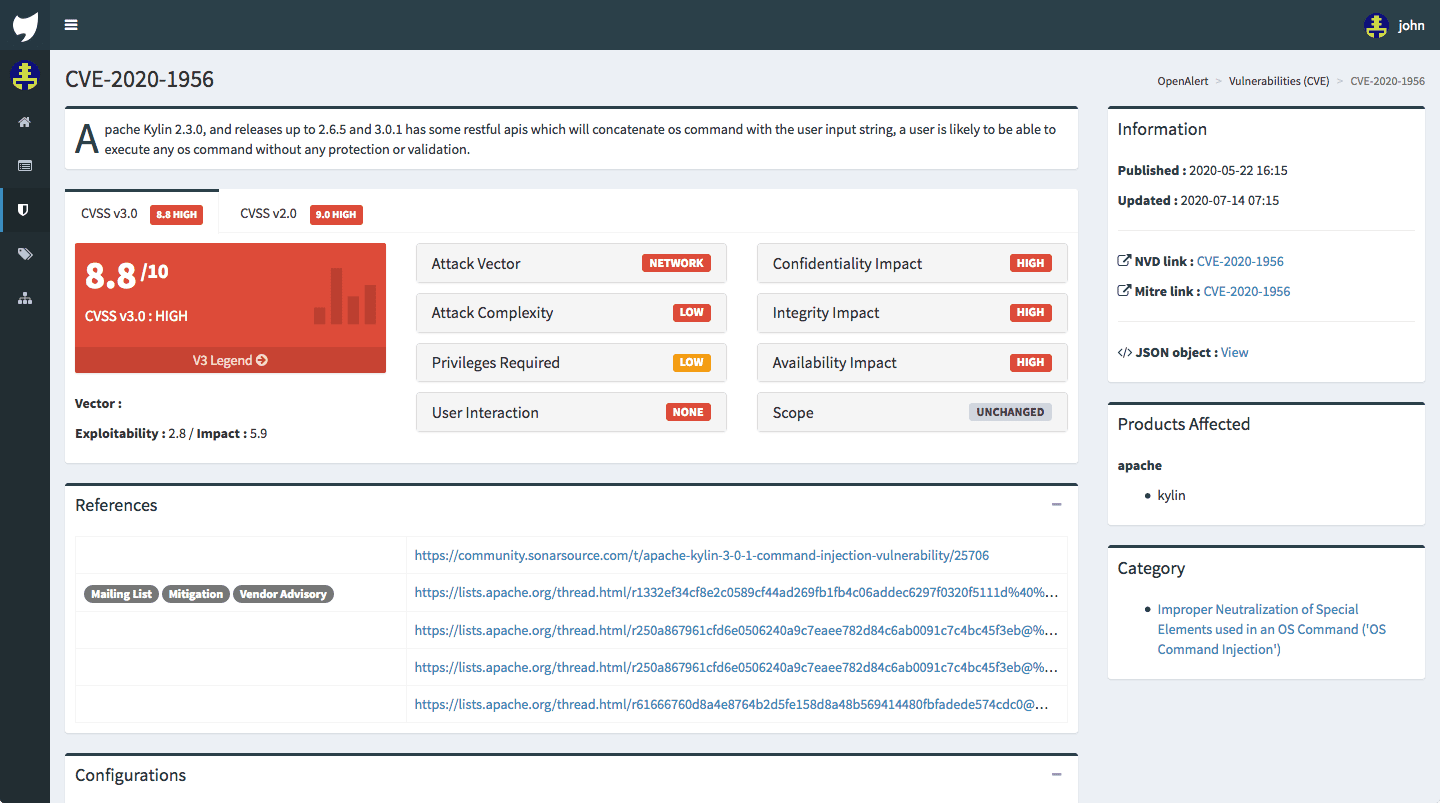
Analyse CVE details
 OpenCVE is synchronized with the feed provided by the NVD. So each CVE displays the standards you already know :
OpenCVE is synchronized with the feed provided by the NVD. So each CVE displays the standards you already know :
- CVE (Common Vulnerability Enumeration)
- CPE (Common Platform Enumeration)
- CWE (Common Weakness Enumeration)
- CVSS (Common Vulnerability Scoring System)
Manage your subscriptions
 OpenCVE parses the CPEs of each CVE and extracts the associated vendors and products.
OpenCVE parses the CPEs of each CVE and extracts the associated vendors and products.
You can then subscribe to as many vendors or products as you want, and you will be notified as soon as a CVE concerning them is published or updated.
Custom dashboard and reports
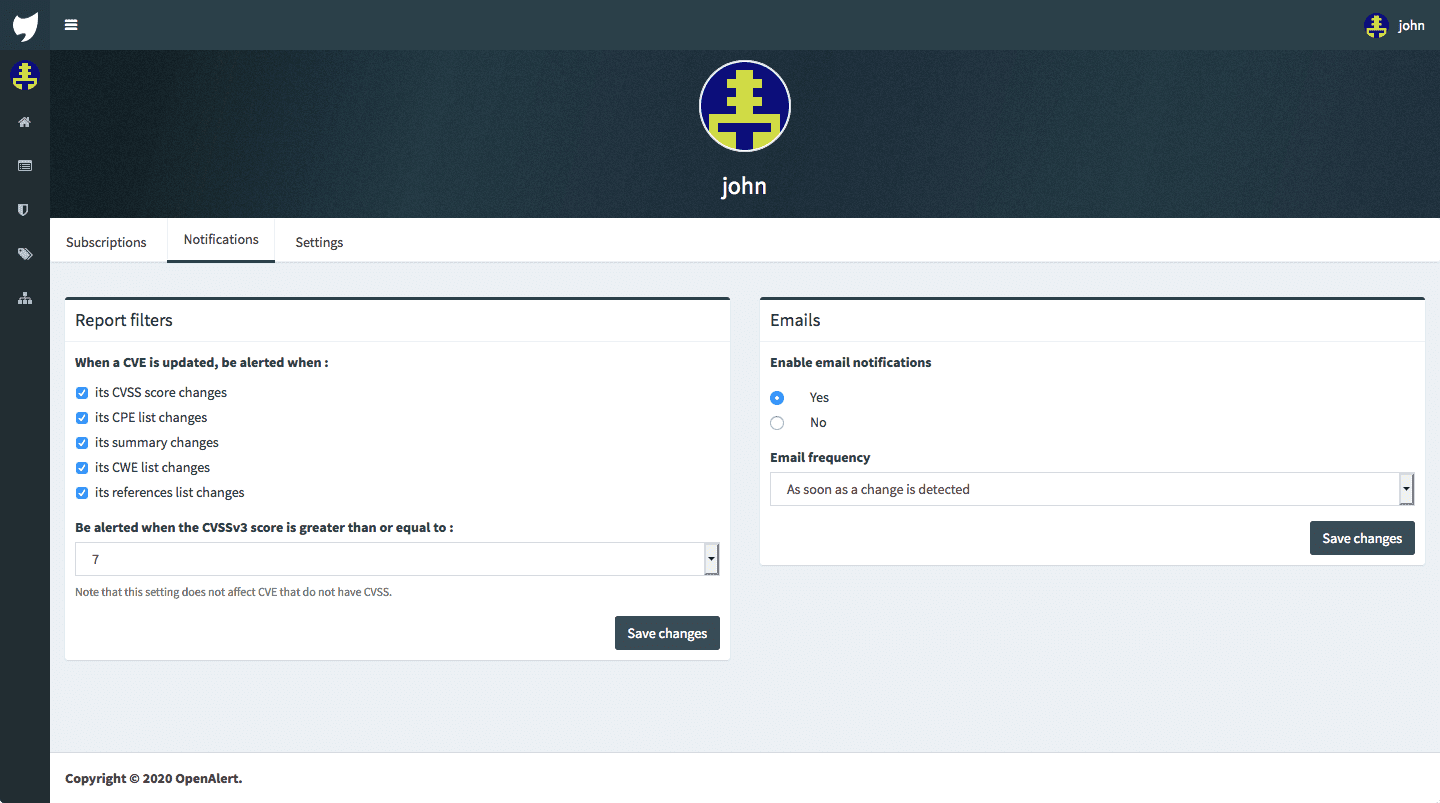 Your dashboard only includes the CVE associated to your subscriptions, and you can filter the list by keywords of CVSS score.
Your dashboard only includes the CVE associated to your subscriptions, and you can filter the list by keywords of CVSS score.
OpenCVE keeps track of the changes, so you can find the history of your alerts on your Reports page.
Email notifications
Don’t miss a vulnerability disclosure anymore: you subscribe in one click on any vendors or products, and you receive an alert as soon as a CVE is published or updated.
OpenCVE formats the notifications in such a way that you can quickly see what are the affected vendors and products.
Changelog v1.5
The objective of this release is to support the 2.0 API endpoints of the NVD instead of the old data feeds.
Important note: this is the last minor version of the 1.x major one (meaning no 1.6 release will be done). The next major version (2.0.0) is a complete refactoring of the stack (from Flask & Celery to Django & Airflow). You can find information on this page to find out more about this new version and the changes compared to the v1.
NVD CVE 4.0 to CVE 5.0 Transition
At the beginning of November 2023, the NVD started to migrate their datasets from CVE 4.0 to CVE 5.0 format. The list of changes for the users can be found here.
The OpenCVE 1.5.0 release uses the 2.0 API of the NVD, therefore the CVE 5.0 format will be now used. Consequently the OpenCVE API users have to notice that the raw_nvd_data field of the GET /cve/<string:id> endpoint is impacting by this change (its content now returns the CVE 5.0 payload).
Upgrade Process
For the new installation this release has no impact, the process (manual or using docker) remains the same.
For existing installation the users need to follow this process:
- stop the Celery beat process
- check the logs of the Celery worker process and stop it too when no task is active
- backup your database
- launch the database migration using the upgrade-db command
- launch the NVD data migration using the migrate-nvd command
- restart the Celery worker and beat processes