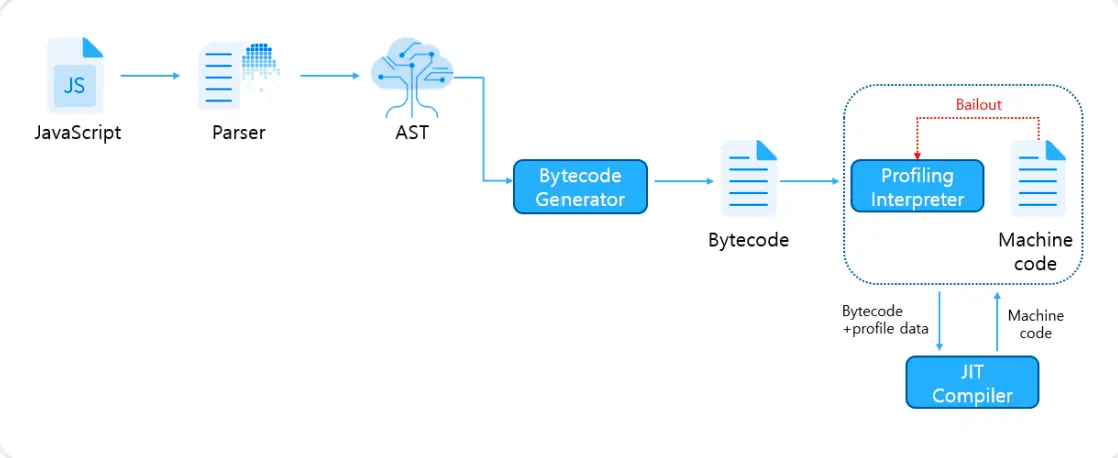
JavaScript execution process in the Chakra engine | Image: NCSC
North Korean-linked hacking group TA-RedAnt has been implicated in a sophisticated large-scale cyber attack dubbed “Operation Code on Toast,” targeting unsuspecting users through a novel Internet Explorer (IE) vulnerability. Security researchers from the Korean National Cyber Security Center (NCSC) and AhnLab revealed the attack in their joint report, which details the mechanics of the exploit and the subsequent malware deployment.
TA-RedAnt, also known as APT37, is no stranger to advanced cyber operations. Historically, this group has conducted targeted attacks against North Korean defectors, South Korean experts on North Korea, and broader South Korean audiences. The report states, “In May 2024, a large-scale attack by TA-RedAnt was detected, involving free software in widespread installation and use among the South Korean public. […] the attack had exploited a new IE vulnerability found in a pop-up ad program embedded within free software, promptly notifying Microsoft to prevent further damage.”
The group leveraged a previously unknown vulnerability (CVE-2024-38178) in IE’s legacy Chakra engine (jscript9.dll). Delivered via seemingly innocuous toast ads—pop-up windows displayed in free software—the attack exploited the vulnerability to execute remote commands.
“The IE vulnerability was exploited through a program that displays toast ads… Hackers infiltrated a server for a domestic ad agency and injected a malicious iframe into the HTML code delivered to the toast ad program,” the report explains.
This is not TA-RedAnt’s first use of IE vulnerabilities. Previous campaigns have included watering hole attacks on media outlets and the distribution of malicious Word documents, as noted in the report: “In January 2021, the first of such cases was a so-called “watering hole attack” on a domestic news outlet… The second case involved a malicious MS Word document distributed in October 2022.”
Once the vulnerability was exploited, a multi-stage malware chain was deployed, culminating in the execution of a variant of RokRAT, a known malicious tool used by TA-RedAnt. The attack stages included:
- First-Stage Malware: Injected into explorer.exe, designed to evade analysis.
- Second-Stage Malware: Collecting system information and relaying it to a staging server.
- RokRAT: Leveraging cloud services for command and control, exfiltrating sensitive data, and executing commands.
AhnLab’s analysis revealed, “The malware was configured to use Yandex Cloud by default, but it also includes functionality to communicate with other cloud services on command”
Microsoft released a patch for CVE-2024-38178 on August 13, 2024, as part of its regular update cycle. “Early detection and cooperative efforts among security companies, including Microsoft, successfully prevented further harm,” the report emphasizes.
The attack underscores the risks of legacy software. Despite Microsoft’s deprecation of IE, its continued integration into some applications leaves systems vulnerable. Developers are urged to abandon risky modules, and users must stay vigilant with updates.
The report concludes, “Users must diligently apply regular security updates for their operating systems and software, while developers must avoid using libraries and modules that are prone to security risks during product development.”
Related Posts:
- Check Point Research Details 0-Day Flaw (CVE-2024-38112), Threatens Windows Users
- Expert: North Korean hackers harvest 11,000 Bitcoins in 2017