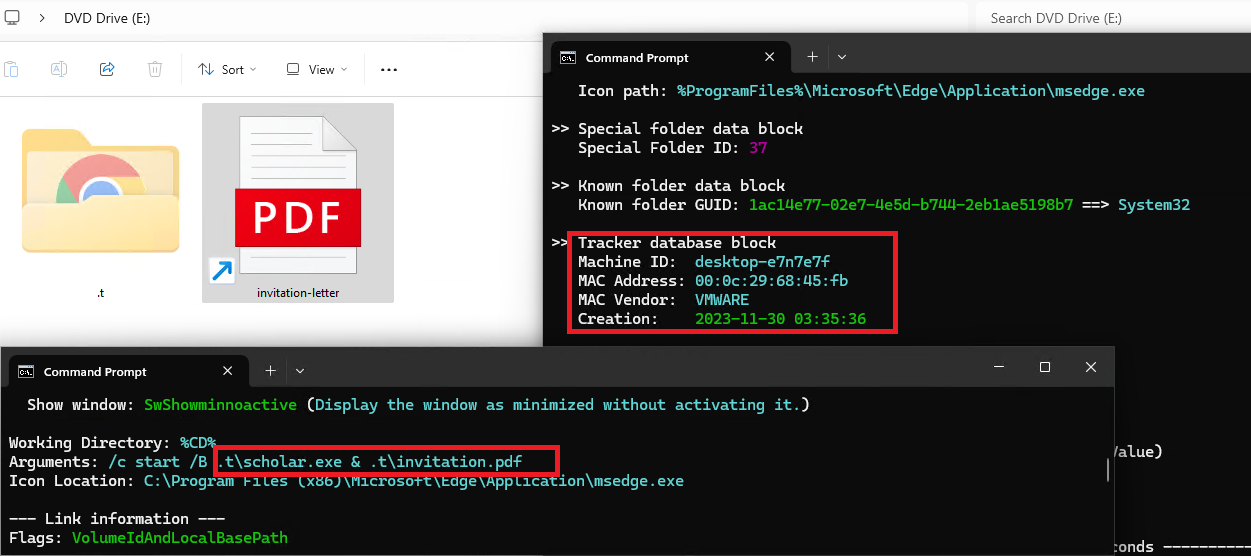
Machine ID metadata in shortcut file (LNK).
A new report from EclecticIQ analysts has uncovered a sophisticated cyber espionage campaign dubbed “Operation FlightNight”. The attackers, using a modified version of an open-source tool, have successfully infiltrated multiple Indian government agencies and private energy companies.
Phishing Lure and Data Theft

The campaign began with carefully crafted phishing emails disguised as official invitations from the Indian Air Force. Hidden within these emails was a malicious information stealer designed to exfiltrate confidential documents, emails, and even sensitive web browser data. These emails contained a modified version of the open-source HackBrowserData information stealer. Once a victim was tricked into opening the attachment, this malware stealthily went to work, stealing vast amounts of data, including:
- Confidential internal documents
- Private email communications
- Cached web browser data (login credentials, cookies, browsing history)
- Financial records and employee details from targeted energy companies
- Information about oil and gas drilling activities
To further evade detection, the attackers used Slack, a popular team communication platform, as a means of exfiltrating stolen data. By blending their malicious traffic with legitimate use of the platform, they were able to mask their movements.
Espionage Motives, Shared Tactics
Operation FlightNight’s nefarious activities bear striking resemblances to another espionage endeavor, the Go-Stealer campaign, previously unearthed by researcher ElementalX2. Such parallels draw a convincing line connecting both campaigns to the same threat actor, with a highly likely motive of cyber espionage.
The arsenal for this clandestine operation included a modified version of HackBrowserData, equipped with additional functionalities for Slack communication, document theft, and malware obfuscation to evade detection. This bespoke malware variant exhibited code similarities with its GitHub origin, yet was fine-tuned to stealthily exfiltrate select file types, including Microsoft Office documents, PDFs, and SQL database files, effectively accelerating the theft process.
Victimology was meticulously compiled through FlightNight Slack channels, where messages listed victims, file paths, timestamps, and URLs for downloading the pilfered data. This method of data cataloging underscores the meticulous planning and execution of Operation FlightNight.
Open-Source Tools, Surprising Exfiltration
Notably, the attackers relied heavily on modified open-source tools and abused the legitimate Slack platform to mask their activities. This highlights the growing trend of threat actors repurposing readily available resources to evade detection while minimizing their investment.
Recommendations
In light of Operation FlightNight, security experts recommend:
- Robust phishing defenses: Implement multi-layered email filtering and user awareness training.
- Behavior-based detection: Focus on detecting suspicious patterns of activity rather than relying solely on signature-based antivirus.
- Network monitoring: Scrutinize traffic on platforms like Slack for unusual data transfers.
- Threat intelligence sharing: Collaborate with security providers and industry peers to stay ahead of evolving threats.
The EclecticIQ report on Operation FlightNight serves as a stark reminder that cyber espionage poses a very real threat to governments and critical industries. By taking proactive measures and understanding the attacker’s methods, organizations can better protect themselves from these sophisticated campaigns.