Operation Magnus Dismantles RedLine and META Infostealer Networks
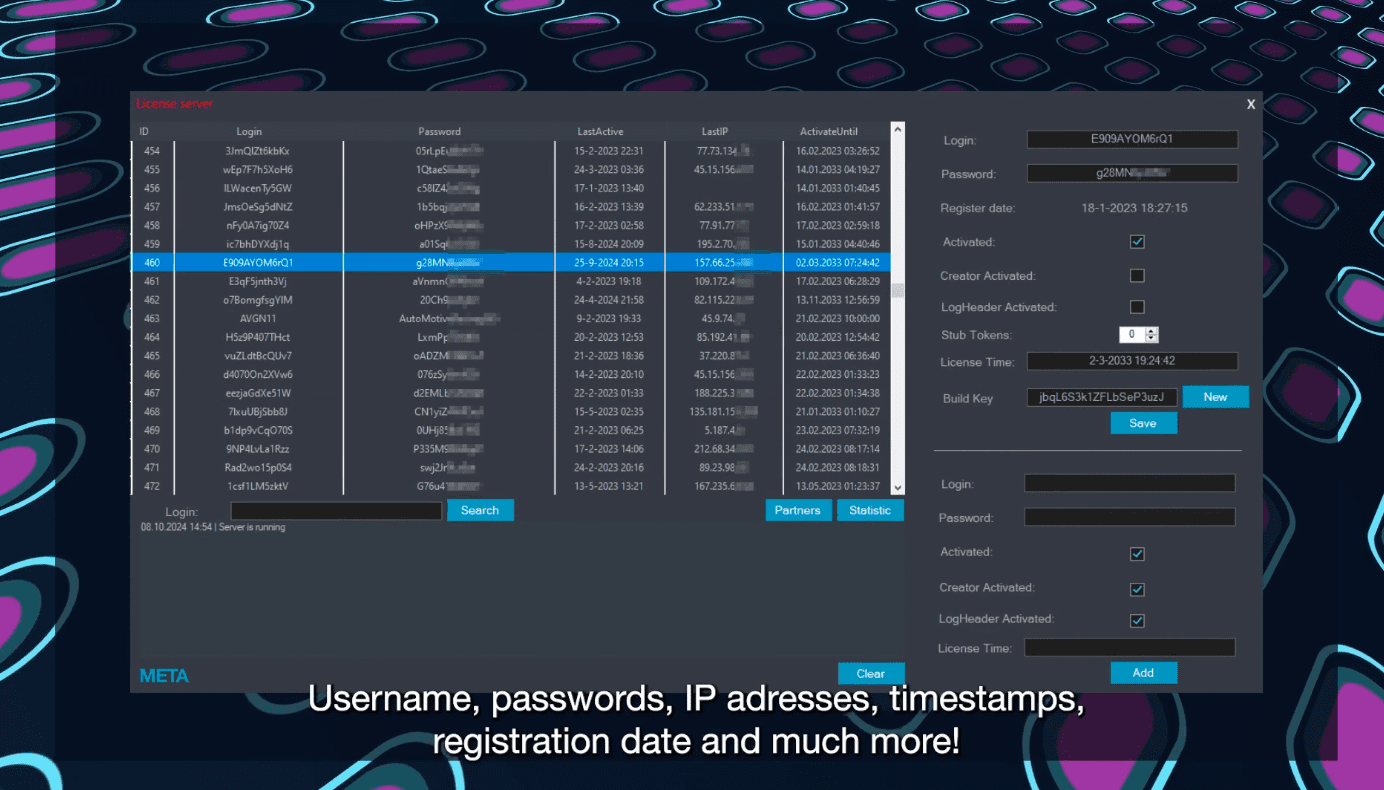
The U.S. Department of Justice, in collaboration with international law enforcement agencies, has disrupted the operations of RedLine and META, two of the world’s most prevalent “infostealers.” These malicious programs have targeted millions of computers globally, pilfering sensitive data such as login credentials, financial information, and cryptocurrency accounts.
Operation Magnus, a joint effort by the Joint Cybercrime Action Taskforce (JCAT) supported by Europol, involved seizing domains, servers, and Telegram accounts used by the malware’s administrators. This operation aimed to disrupt the infostealers’ infrastructure and hinder their ability to distribute and control the malware.
As the Department of Justice press release explains, “Infostealers are a prevalent form of malware used to steal sensitive information from victim’s computers including usernames and passwords, financial information, system information, cookies, and cryptocurrency accounts.” This stolen data is often sold on underground forums, fueling further cybercrime and fraud.
RedLine and META, in particular, have been linked to attacks against major corporations and are capable of bypassing multi-factor authentication (MFA) by stealing authentication cookies and system information.
The operation involved law enforcement agencies from multiple countries, including the Netherlands, Belgium, the United Kingdom, Australia, and Portugal.
In addition to the infrastructure disruption, the Justice Department unsealed charges against Maxim Rudometov, identified as one of the developers and administrators of RedLine. According to the complaint, Rudometov “regularly accessed and managed the infrastructure of RedLine Infostealer, was associated with various cryptocurrency accounts used to receive and launder payments and was in possession of RedLine malware.”
The operation has already recovered millions of stolen credentials and other sensitive data. “While an exact number has not been finalized, agents have identified millions of unique credentials (usernames and passwords), email addresses, bank accounts, cryptocurrency addresses, credit card numbers, etc.,” the press release stated.
To assist potential victims, authorities have launched a dedicated website. This website provides information about the operation and resources for individuals who may have been affected by RedLine or META.
Related Posts:
- RedLine malware pretends to be a Windows 11 upgrade installers
- Redline Stealer Malware Evolves with Sneaky New Tricks, Spreads Globally
- Unit 42’s Insight: The Sophisticated Evasion Tactics of GuLoader and RedLine Stealer
- Infostealers Overcome Chrome’s App-Bound Encryption, Threatening User Data Security
- Phishing Campaign Bypasses MFA to Target Meta Business Accounts, Putting Millions at Risk





