Unit 42’s Insight: The Sophisticated Evasion Tactics of GuLoader and RedLine Stealer
Among the myriad of threats, GuLoader and RedLine Stealer stand out for their sophisticated anti-analysis techniques. Unit 42 Incident Response team from Palo Alto Networks reveals the intriguing world of these malware families, unveiling their cunning methods to thwart analysis and detection.
GuLoader: A Master of Obfuscation
GuLoader, notorious for its complex C2 (Command and Control) configuration, has continuously evolved its obfuscation techniques. Researchers from the Unit 42 Incident Response team have observed significant changes in GuLoader’s approach, notably in how it stores and secures its configuration data.

Comparing old and new methods of storing ciphertext | Image: Unit 42
- Ciphertext Splitting: Initially, GuLoader encrypted its configuration data as a continuous byte sequence. However, newer versions exhibit an intricate method where ciphertext is divided into 4-byte DWORDs. Each DWORD is encrypted using randomized mathematical operations, demanding a more nuanced approach to decryption.
- Control Flow Obfuscation: A 2023 GuLoader sample revealed an advanced level of anti-analysis instructions. These instructions, designed to trigger exceptions like EXCEPTION_BREAKPOINT and EXCEPTION_ACCESS_VIOLATION, rendered previous analysis techniques ineffective. The Unit 42 team had to adapt, manually bypassing these anti-analysis instructions to extract the configuration data.
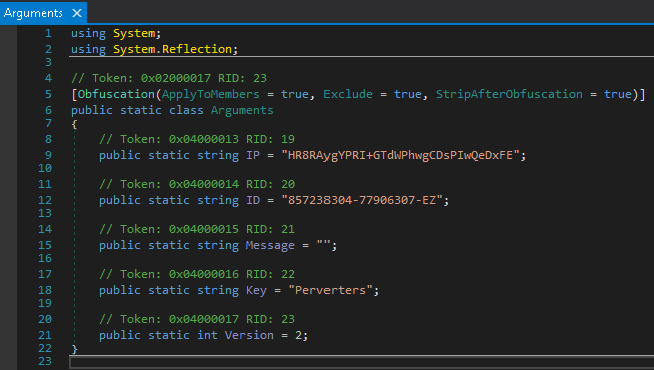
RedLine Stealer: Stealth and Complexity
RedLine Stealer, another formidable threat, employs unique methods to protect its configuration data. The analysis of a specific RedLine Stealer sample, with a SHA256 hash of a4cf69f849e9ea0ab4eba1cdc1ef2a973591bc7bb55901fdbceb412fb1147ef9, provided insights into its encryption mechanisms.

Screenshot taken from dnSpy that contains the RedLine Stealer sample’s encrypted configuration block | Image: Unit 42
Using an MSIL decompiler like dnSpy, researchers could locate the encrypted configuration block. However, extracting usable information required the implementation of a custom decryption routine in Python. This process involved manually obtaining ciphertexts and keys from the decompiled result, followed by executing the decryption routine.
The exploration of GuLoader and RedLine Stealer’s anti-analysis techniques offers a glimpse into the sophisticated world of malware evasion tactics. For a more detailed technical analysis, refer to the original document.






