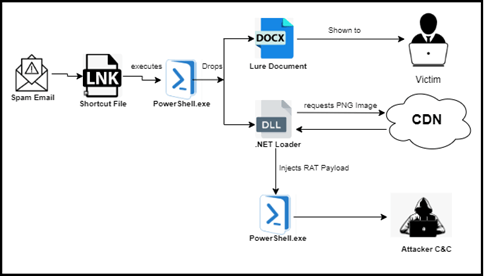
Overview of the Attack | Image: CRIL
Cyble Research & Intelligence Labs (CRIL) has uncovered a sophisticated cyber espionage campaign dubbed “Operation ShadowCat.” This campaign targets individuals with a keen interest in Indian political affairs, including government officials, political analysts, and journalists.
The malicious campaign starts with a deceptive shortcut (.LNK) file disguised as a Word document, distributed through spam emails. Once the .LNK file is executed, it triggers a PowerShell command that deploys a .NET loader file and a decoy Word document on the victim’s machine. The PowerShell script then fetches a steganographic PNG image from a remote server, which contains a Gzip-compressed payload. This payload is decompressed and injected into the PowerShell process, all performed in memory to evade detection.
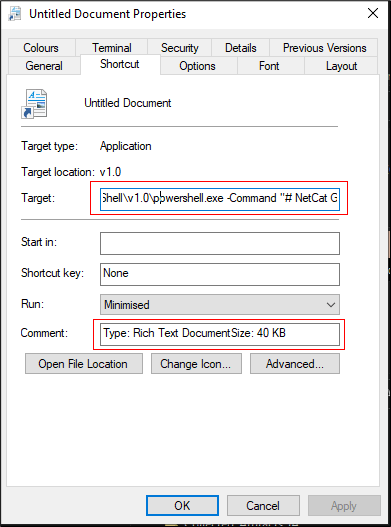
The attack initiates from a shortcut file named “Untitled Document.LNK,” which appears to be a legitimate Word document. Upon execution, the LNK file loads an embedded PowerShell script, which performs several tasks:
- Execution Prevention Based on Geo-location: The script first retrieves the victim’s system’s GeoID to prevent execution in specific countries. If the GeoID matches any listed in the script, the execution terminates.
- String De-obfuscation: The script de-obfuscates an array of strings, including base64-encoded data, PowerShell commands, and URLs necessary for the infection chain.
- Self-deletion and Lure Document Creation: The script deletes the original LNK file, creates a new lure document, and opens it. The lure document is typically a question posed to the Indian parliament, targeting individuals interested in Indian political affairs.
- Malicious DLL Execution: The script loads and executes a malicious DLL file, either directly in memory or by writing it to disk and then executing it.
The .NET loader file fetches a PNG image from a remote server, which contains hidden Gzip-compressed content. The image is parsed, and the compressed data is decompressed to reveal shellcode. This shellcode is injected into the PowerShell process using Asynchronous Procedure Call (APC) injection, a method that queues a call to the shellcode when the process resumes from a suspended state.
The final payload is a Go-compiled RAT utilizing publicly available Go utilities like HashiCorp Yamux for multiplexing communication streams and Secsy goftp for file transfers. This RAT connects to its C&C server via a WebSocket connection on port 443, using a custom “NetCat” subprotocol for reverse shell operations and command execution.
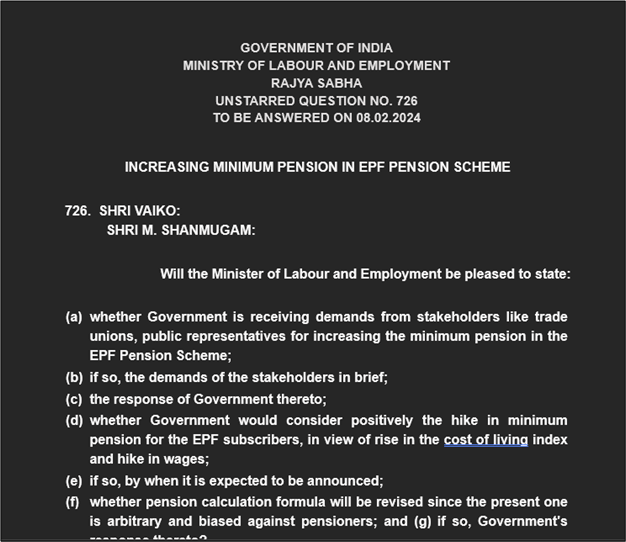
The lure documents and the focus on Indian political affairs suggest a targeted approach to select victims with significant knowledge or involvement in political matters in India. The threat actor’s avoidance of infecting systems in Russian-speaking nations indicates a strategic effort to minimize detection and backlash in regions where they may have a presence.
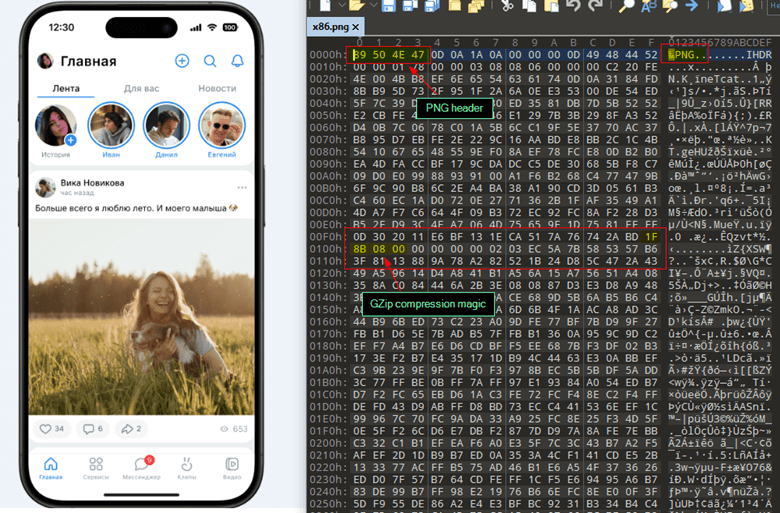
The original image used for steganography was posted on a Russian-speaking social media platform, leading researchers to suspect that the threat actors might be Russian-speaking. While the exact identity of the threat actor remains unknown, the campaign’s sophistication and operational patterns suggest it is likely the work of a financially motivated, Russian-speaking group or Ransomware-as-a-Service (RaaS) entity.
Operation ShadowCat underscores the persistent and evolving nature of cyber espionage threats targeting political entities. By understanding the tactics, techniques, and procedures (TTPs) employed in this campaign, organizations and individuals can enhance their security posture and proactively defend against similar attacks.
For more detailed information, please refer to CRIL’s comprehensive report on Operation ShadowCat.
Related Posts:
- APT29 Strikes German Politics with WINELOADER Malware Assault
- RedLine malware pretends to be a Windows 11 upgrade installers
- Espionage Campaign Returns: LightSpy Targets Southern Asia
- SneakyChef Espionage Campaign Targets Governments Across the Globe
- One Click, Bankrupt: Android Trojan Steals Through WhatsApp