ophcrack v3.8 released, A windows password cracker
ophcrack (Time-Memory-Trade-Off-Crack)
Ophcrack is a free Windows password cracker based on rainbow tables. It is a very efficient implementation of rainbow tables done by the inventors of the method. It comes with a Graphical User Interface and runs on multiple platforms.
Features:
- » Runs on Windows, Linux/Unix, Mac OS X, …
- » Cracks LM and NTLM hashes.
- » Free tables available for Windows XP and Vista/7.
- » Brute-force module for simple passwords.
- » Audit mode and CSV export.
- » Real-time graphs to analyze the passwords.
- » LiveCD available to simplify the cracking.
- » Dumps and loads hashes from encrypted SAM recovered from a Windows partition.
- » Free and open source software (GPL).
Changelog v 3.8.0
- (feature) replacement of Qt4 by Qt5
- (feature) replacement of Qwt by Qt5Charts
- (fix) the number of threads can be set to any value > 0 and < 100 in the gui
Install ophcrack
Ophcrack can be downloaded from sourceforge.
Binaries compiled for Windows are provided. These binaries are standalone (portable) and no installation is required.
The Linux version is a source package. It can be compiled and installed using these commands:
./configure
make
make install

By Self-made [GPL, GFDL or CC-BY-SA-3.0], from Wikimedia Commons
Tables
The tables have to be downloaded manually: http://ophcrack.sourceforge.net/tables.php
Usage
Ophcrack and the ophcrack LiveCD are available for free at the ophcrack project page (http://ophcrack.sourceforge.net/).
Ophcrack rainbow tables are available at ophcrack rainbow tables page (http://ophcrack.sourceforge.net/tables.php).
- First step (optional)
This step is optional but will speed up the cracking process.
Run ophcrack and set the number of threads under the Preferences tab to the number of logical cores of the computer running ophcrack (accounting for Hyper-threading). - Second step
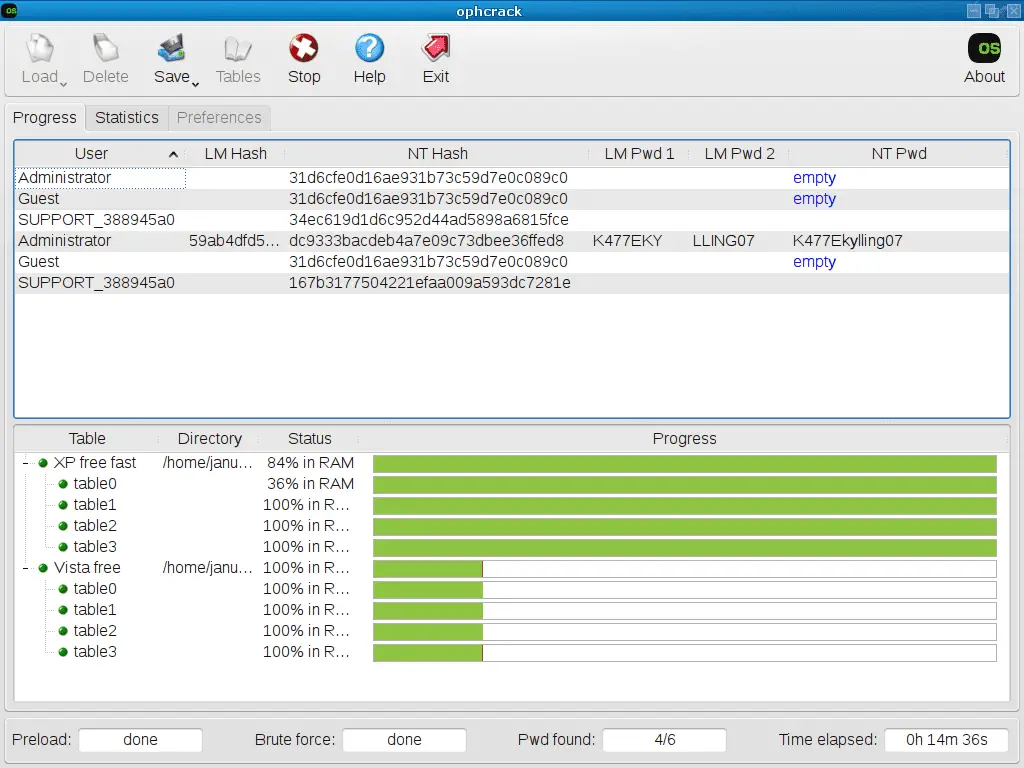
Load hashes using the Load button. You can either enter the hash manually (Single hash option), import a text file containing hashes you created with pwdump, mimikatz or similar third-party tools (PWDUMP file option), extract the
hashes from the SYSTEM and SAM files (Encrypted SAM option) or dump the SAM from the computer ophcrack is running on (Local SAM option). For the Encrypted SAM option, the SAM is located under the Windows system32/config directory and can only be accessed for a Windows partition that is NOT running. For the Local SAM option, you MUST execute ophcrack with the administrator rights on the computer you want to dump the SAM. - Third step (optional)
This step is optional but will speed up the cracking process.
Delete with the Delete button every user account you are not interested in (for example the Guest account). You can use the Ctrl key to make multiple selections. Ctrl-a will select every loaded hash. Keep in mind that the time needed to crack password hashes with rainbow tables is proportional to the number of hashes loaded. With a brute force attack, the
cracking time is NOT dependant on the number of unsalted hashes loaded. That’s why it’s advisable to remove any unnecessary user account with the Delete button. - Fourth step
Install (Tables button), enable (green and yellow buttons) and sort wisely (up and down arrows) the rainbow tables you are going to use. Keep in mind that storing the rainbow tables on a fast medium like an SSD will significantly speed up the cracking process. - Fifth step
Click on the Crack button to start the cracking process. You’ll see the progress of the cracking process in the bottom boxes of the ophcrack window. When a password is found, it will be displayed in the NT Pwd field. You can then save the results of a cracking session at any time with the Save button.
Copyright (c) 2008 Philippe Oechslin, Cedric Tissieres, Bertrand Mesot





