osueta: exploit the OpenSSH User Enumeration Timing Attack
What’s OSUETA?
Osueta it’s a simple Python2 script to exploit the OpenSSH User Enumeration Timing Attack, present in OpenSSH versions <= 7.2 and >= 5.* . The script has the ability to make variations of the username employed in the bruteforce attack, and the possibility to establish a DOS condition in the OpenSSH server.
Installing
# apt-get install python-ipy python-nmap
# pip install paramiko
# git clone https://github.com/c0r3dump3d/osueta.git
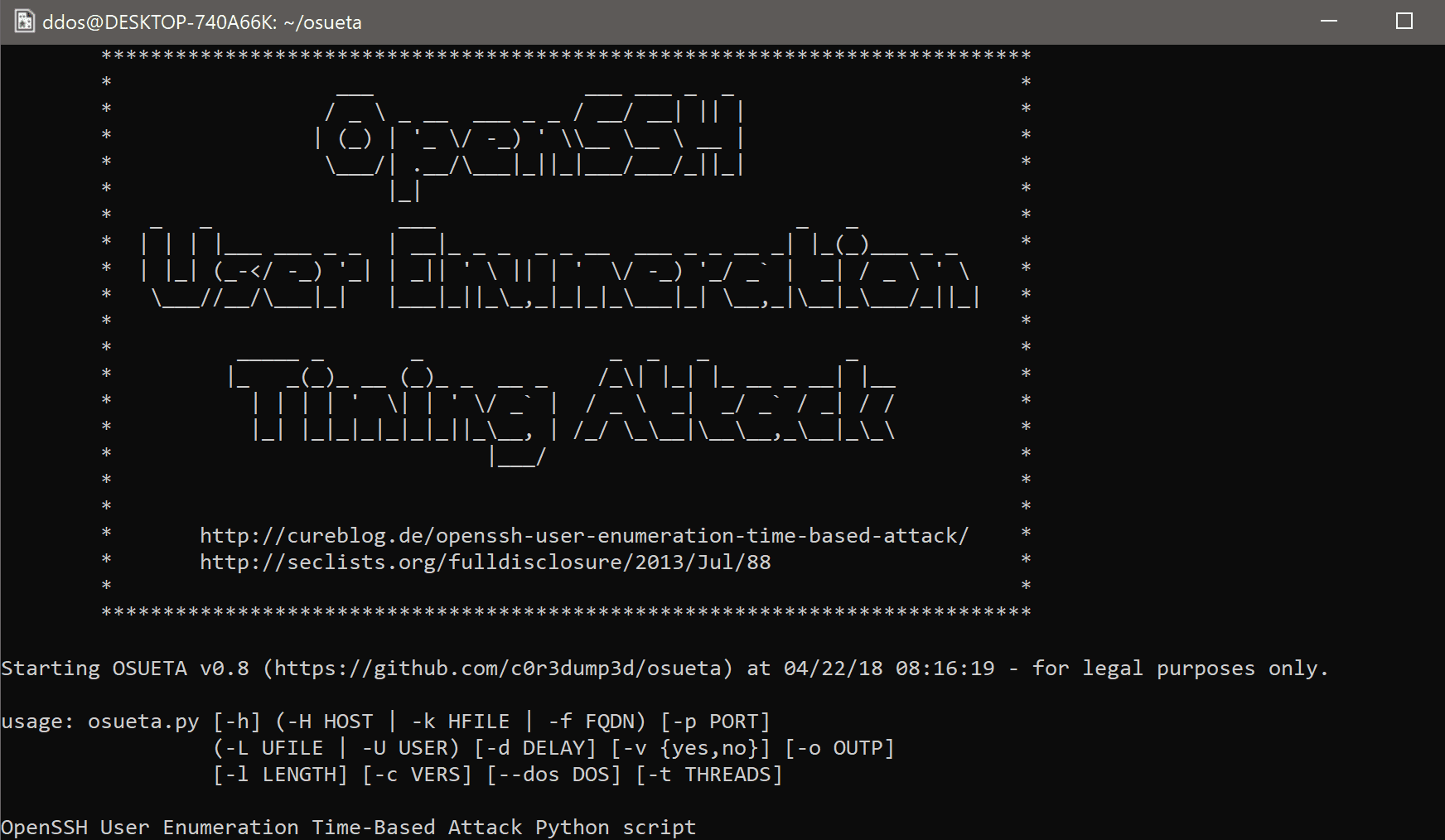
Usage
osueta.py [-h] [-H HOST] [-k HFILE] [-f FQDN] [-p PORT] [-L UFILE]
[-U USER] [-d DELAY] [-v VARI] [-o OUTP] [-l LENGTH]
[-c VERS] [–dos DOS] [-t THREADS]OpenSSH User Enumeration Time-Based Attack Python script
optional arguments:
-h, –help show this help message and exit
-H HOST Host Ip or CIDR netblock.
-k HFILE Host list in a file.
-f FQDN FQDN to attack.
-p PORT Host port.
-L UFILE Username list file.
-U USER Only use a single username.
-d DELAY Time delay fixed in seconds. If not, delay time is calculated.
-v VARI Make variations of the username (default yes).
-o OUTP Output file with positive results.
-l LENGTH Length of the password in characters (x1000) (default 40).
-c VERS Check or not the OpenSSH version (default yes).
–dos DOS Try to make a DOS attack (default no).
-t THREADS Threads for the DOS attack (default 5).
Copyright (C) 2013 c0r3dump3d
Source: https://github.com/c0r3dump3d/





