
The Open Web Application Security Project (OWASP) has released its updated list of the top 10 vulnerabilities affecting smart contracts in 2025. This comprehensive awareness document identifies the most critical vulnerabilities in smart contracts, offering developers and security professionals a roadmap to mitigate risks in decentralized ecosystems.
The OWASP Smart Contract Top 10 highlights the vulnerabilities most frequently exploited in the Web3 landscape. These include:
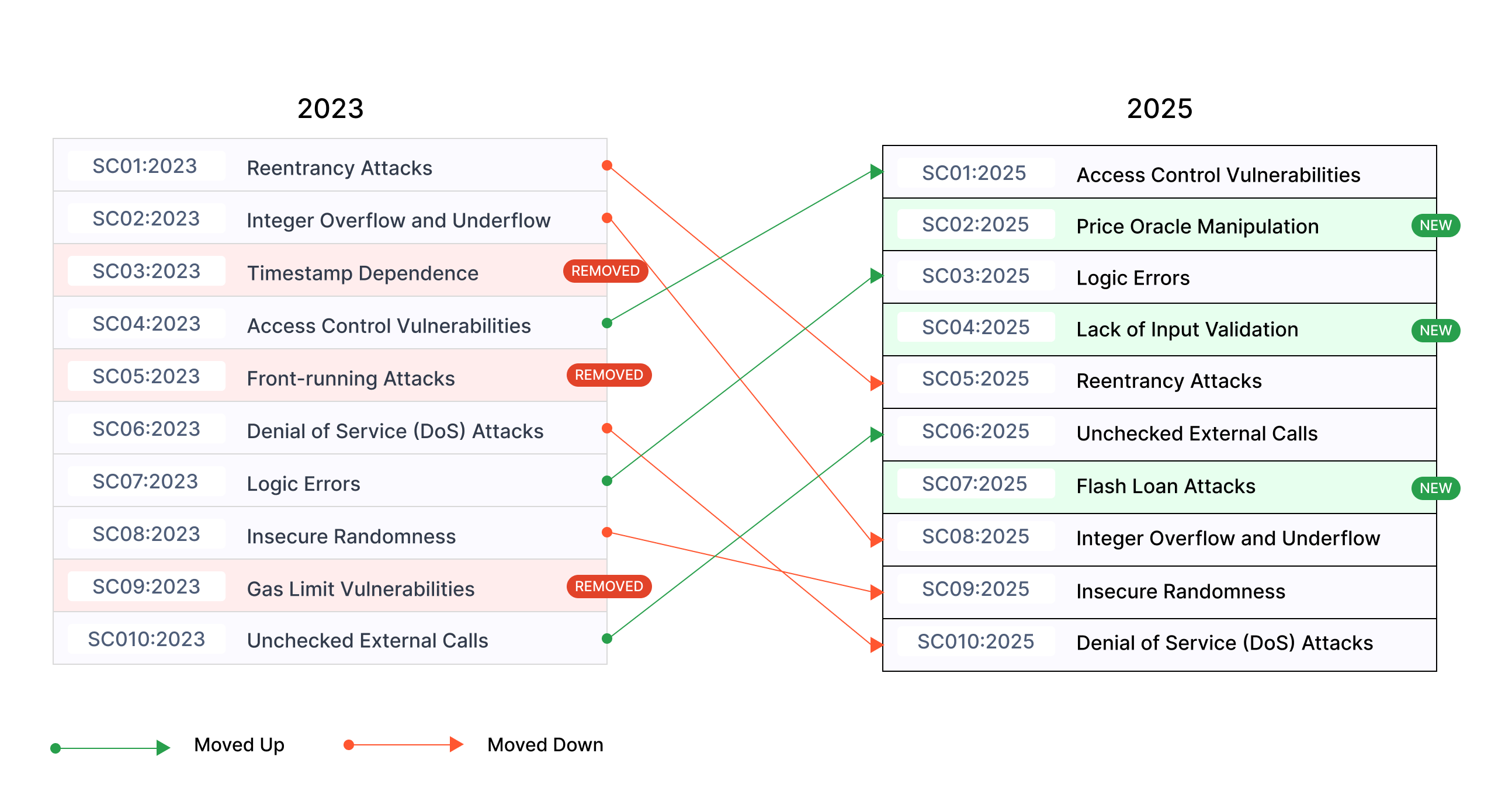
- Access Control Vulnerabilities (SC01:2025): Access control flaws allow unauthorized users to access or modify a contract’s data or functions, potentially leading to severe security breaches. This issue accounted for $953.2 million in losses in 2024, according to SolidityScan’s Web3HackHub.
- Price Oracle Manipulation (SC02:2025): Attackers exploit weak data feeds to tamper with external data sources, destabilizing protocols and causing financial havoc.
- Logic Errors (SC03:2025): Mistakes in business logic remain a costly issue, leading to improper token minting, flawed lending logic, or incorrect reward distributions.
- Reentrancy Attacks (SC05:2025): These exploit a contract’s ability to re-enter vulnerable functions, often resulting in drained funds or broken logic. Such attacks caused $35.7 million in losses in 2024.
- Flash Loan Attacks (SC07:2025): These attacks manipulate protocols using uncollateralized loans, wreaking havoc on liquidity and token pricing mechanisms.
Additional critical vulnerabilities include Integer Overflow and Underflow (SC08:2025), Insecure Randomness (SC09:2025), and Denial of Service Attacks (SC10:2025).
For the full list and detailed recommendations, visit the OWASP Smart Contract Security Project.
Related Posts:
- AWS Patches Vulnerabilities in WorkSpaces, AppStream 2.0, and DCV Clients
- CVE-2024-52281: Rancher Vulnerability Exposes Users to Stored XSS Attacks